Securing Trunk Links in VLAN Environments: Cisco Network Trunking and VLANs Port Best Practices In today’s complex network environments, securing trunk links is crucial for [...]
Retail Cybersecurity Fortinet FortiGate fg-50g vs Point-of Sale Firewall: Network Security & Threat Protection In today’s digital landscape, network security is paramount. The Fortinet FortiGate [...]
FortiGate Firewall Global Tech Case Studies: Secure Network Performance for Branch Offices In today’s rapidly evolving cybersecurity landscape, securing branch offices presents unique and significant [...]
How Small Businesses Use FortiGate FG-30G To Cut Threats By 45% Firewall: Fortinet Is the 30G Right for Your Network? In an era defined by [...]
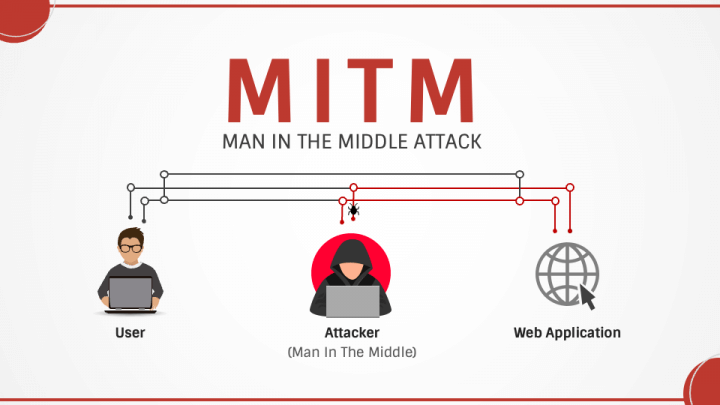
Preventing Man-in-the-Middle Attacks at layer 2: A Security Guide In today’s interconnected digital landscape, understanding and mitigating cyber threats is paramount. This guide provides essential [...]
Network Switch Cyber Security Best Practices for Switch Deployment In today’s interconnected world, the security of your network is paramount. Network switches, the unsung heroes [...]
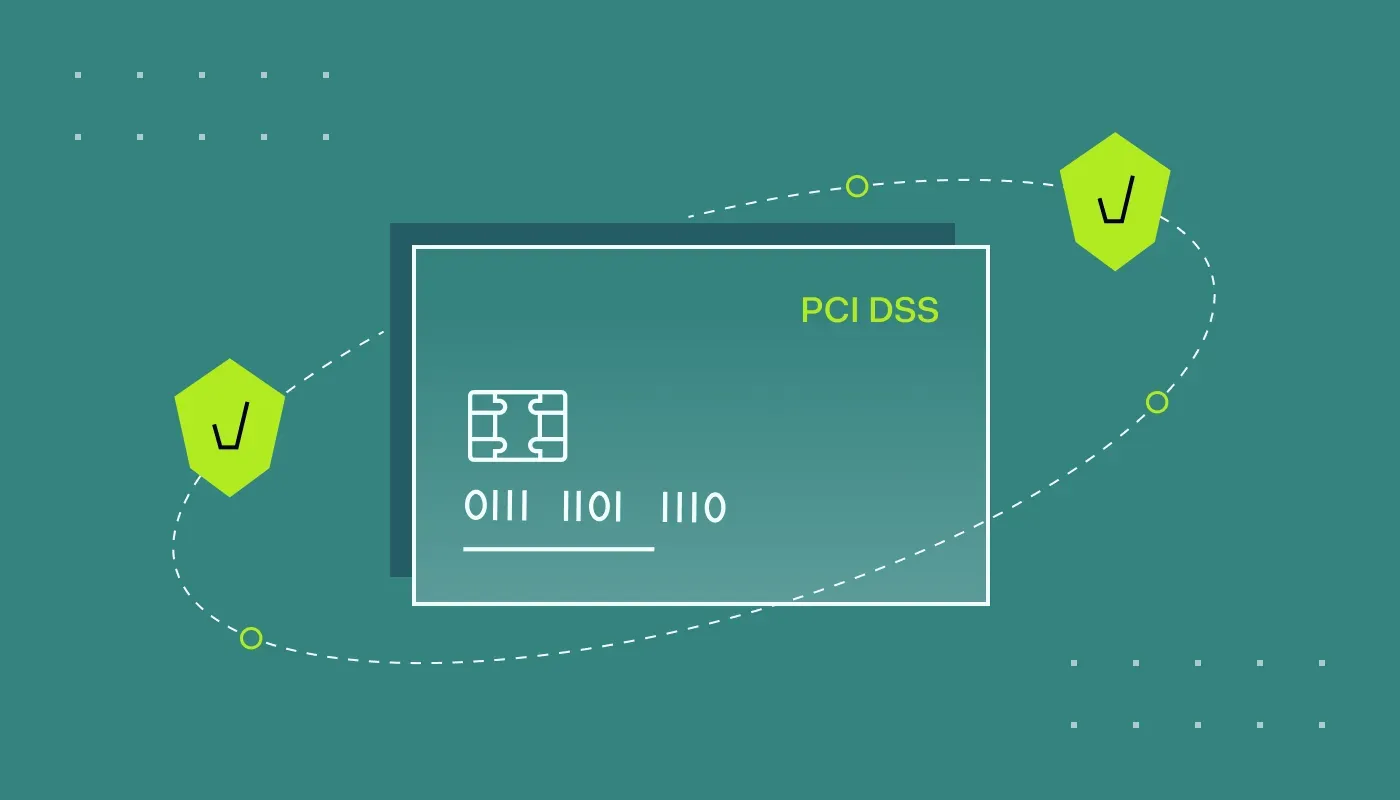
PCI DSS Network Segmentation for Compliance: Achieving PCI DSS Compliance In today’s digital landscape, ensuring the security of cardholder data is paramount for any organization [...]
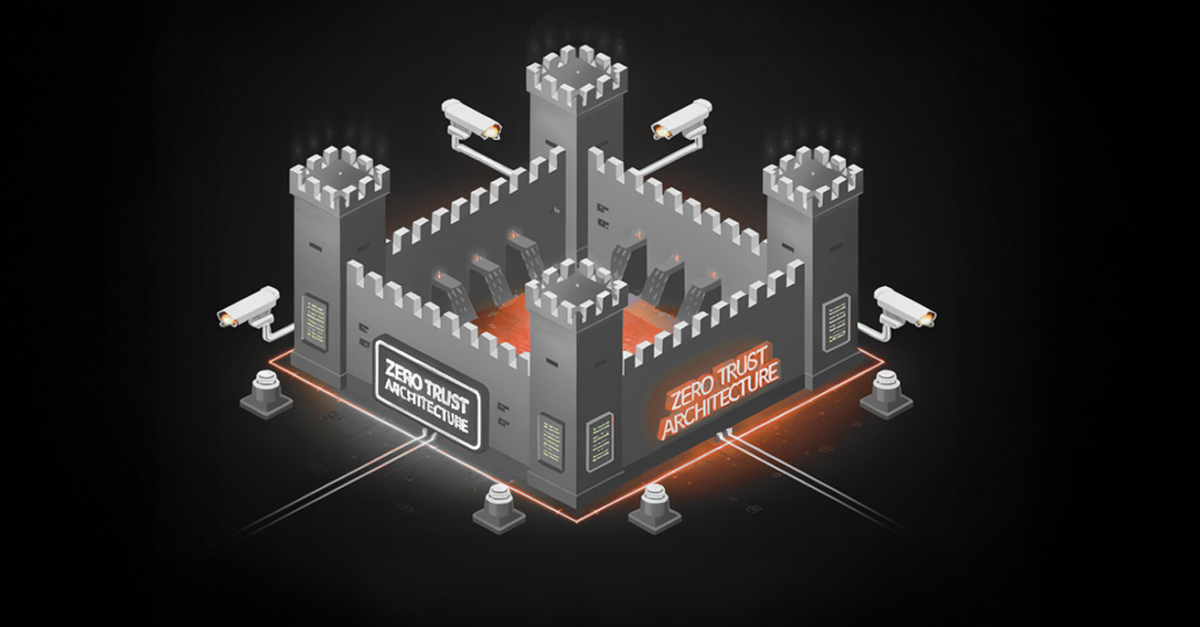
Role of Layer 2 Switches in Zero Trust Architecture: Layer 2 Segmentation, Zero Trust Security Use Cases & Verification In today’s dynamic threat landscape, a [...]
Fortigate Fortinet: Unify Security Operations & Unified Threat Management In today’s rapidly evolving digital landscape, safeguarding your infrastructure is paramount to ensuring the success of [...]
SSL/SSH Inspection Explained: Deep Packet Inspection Analysis on FortiGate SSH Inspection and SSL Inspection. In the ever-evolving landscape of cybersecurity threats, safeguarding your enterprise’s data [...]