What is a Security Operations Center (SOC)? In this article, we will explore the concept of a Security Operations Center (SOC) in greater detail, including [...]
Network Security Checklist – Complete Guide To Protect Enterprise Networks (2024) Network security is paramount in today’s digital landscape, where organizations face increasingly sophisticated threats. [...]
The Future of IoT Gateways: Bridging Devices for Seamless Connectivity The future of IoT gateways holds significant promise as these devices play a crucial role [...]
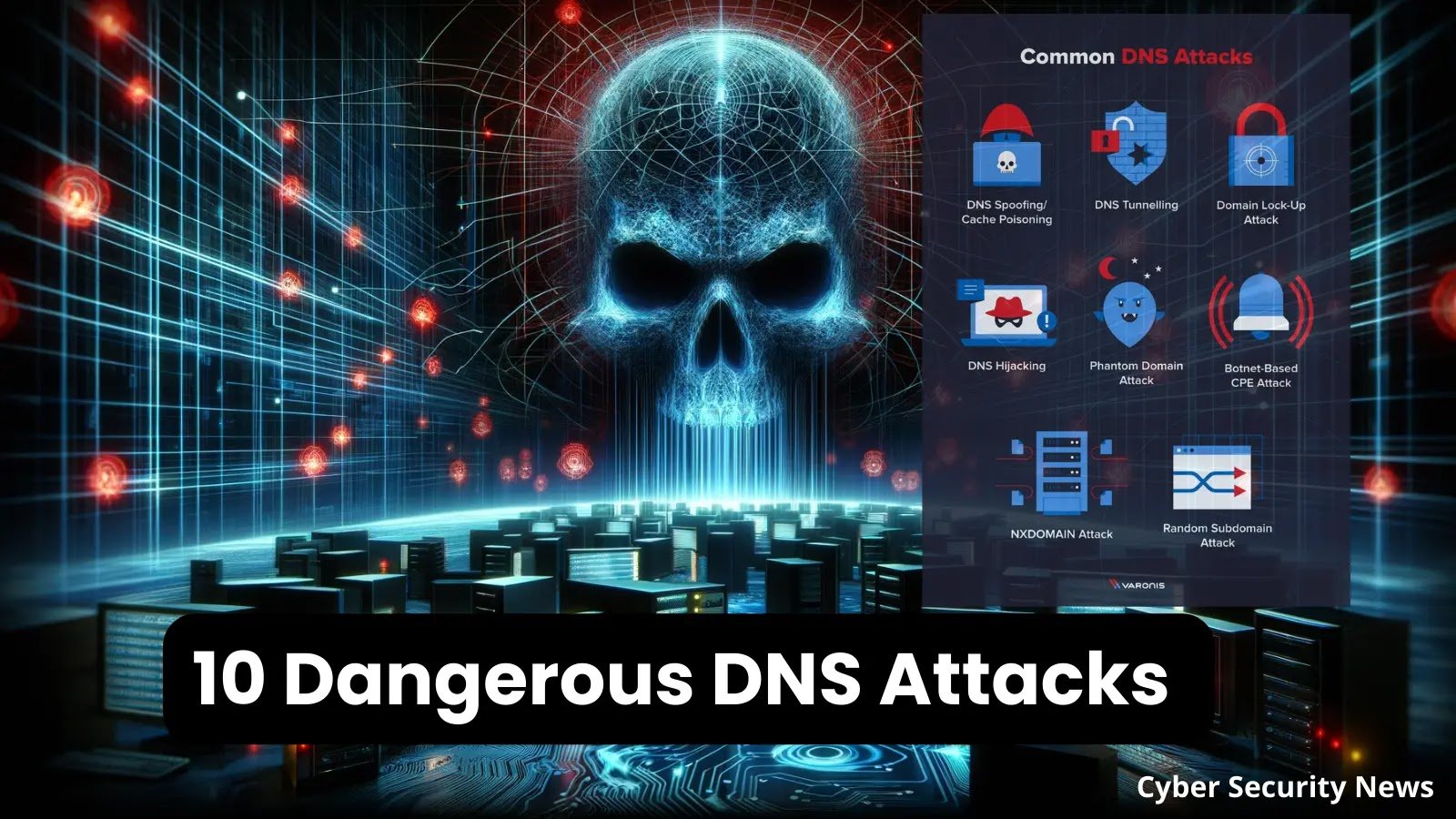
10 Dangerous DNS Attacks Types & Prevention Measures – 2024 Our topic for today seems to be centered around the most common 10 DNS attacks and how [...]
What is Secure Access Service Edge (SASE) – A Managerial Guide For Network Security Secure Access Service Edge (SASE) is a cloud-based security service that [...]
Best Network Security Companies for CISOs Features. Network security vendors offer a variety of products and services to prevent harm to an organization’s computer networks, [...]
Fortinet Secure SD-WAN: The Fortinet Secure SD-WAN solution provides all these and more, protecting your investment along your digital-first journey by scaling and adapting to [...]
Approximately sixteen years ago, in the year 2007, Palo Alto Networks introduced their inaugural product, thus significantly transforming the realm of network security. At that [...]
In the ever-evolving landscape of cybersecurity, vulnerabilities are discovered and exploited with alarming frequency. Today, we shine a light on an insidious flaw in FortiOS [...]
As technology continues to advance at a rapid pace, so do the methods used by cyber criminals to breach an organization’s defenses. With Multi-Factor Authentication [...]