Top 10 Best SOC Tools In 2024 An organization’s SOC (Security Operations Center) monitors and analyzes network, system, and data security. The SOC tools detect, investigate, [...]
Bitdefender Security Privilege Escalation Vulnerability – Patch Now The popular cybersecurity technology firm Bitdefender has patched a vulnerability that might lead to privilege escalation in its widely [...]
SDP vs VPN: Which is the Best Security Solution for Enterprise Business Introduction As organizations move towards digitization, security has become a significant part of [...]
What is Malware? Removal and Prevention Malware, which is an abbreviation for “malicious software,” is any software that is purposefully designed to do damage to [...]
What Is SOAR and How It Works? Features and Benefits The famous word SOAR’s complete form is security orchestration, automation, and response. It is a [...]
Firewall Tips and Tricks for Secure Remote Work Environments Securing remote work environments is crucial to protect sensitive data and maintain the integrity of your [...]
Strengthening Digital Defenses: The Vital Role of Cybersecurity in Database Automation In the contemporary era, where data stands as the backbone of organizations, the security [...]
10 Best Firewall as a Service (FWaaS) Providers – 2024 Firewall as a Service (FWaaS) is an emerging security model in cloud computing and network [...]
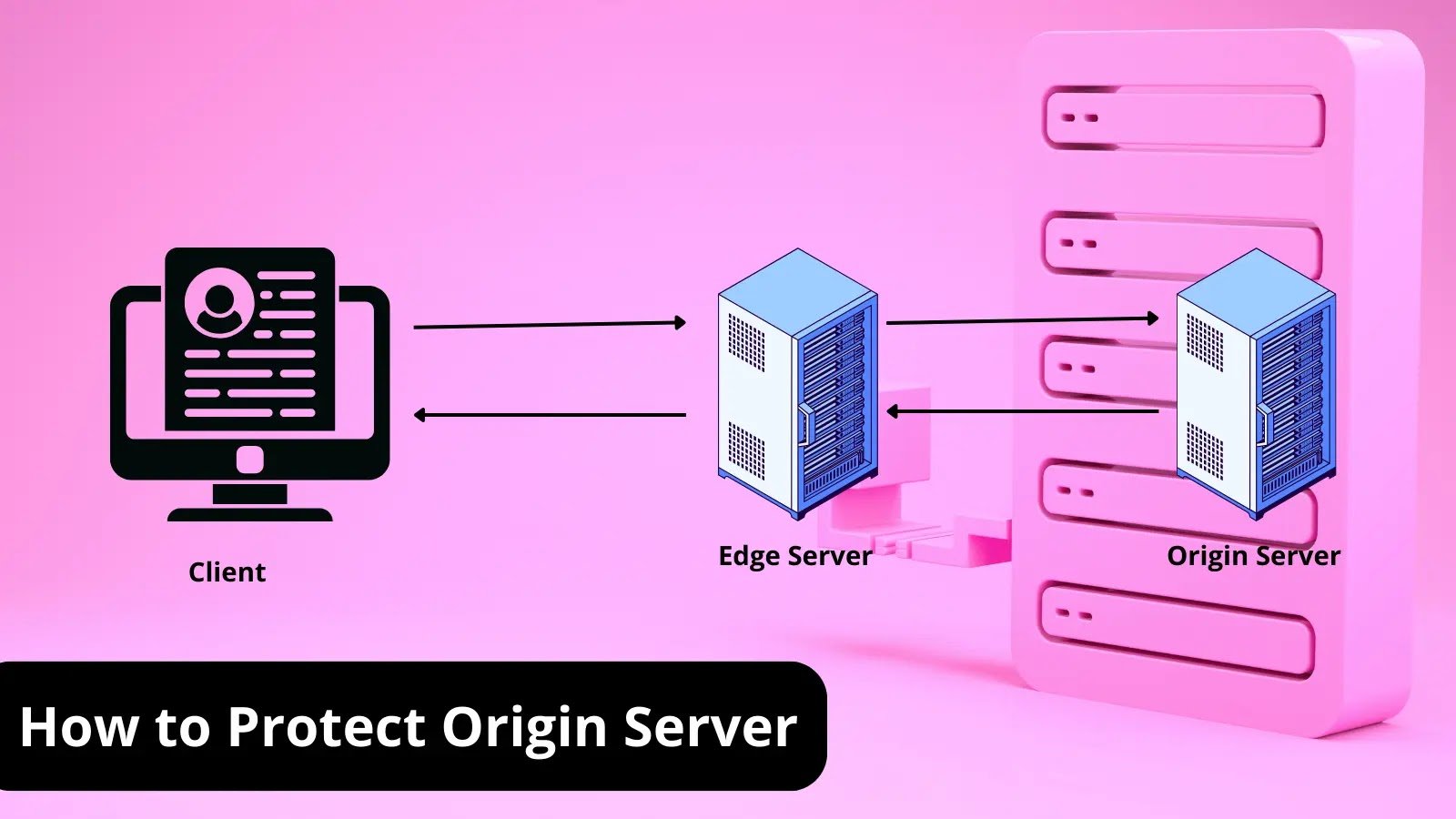
What is Origin Server? How To Protect it? A Detailed Guide The origin server stores a website’s or application’s content and data. As the starting [...]
3 Key Ways VPNs Can Benefit Your Business In an age when security and privacy have become major considerations on the Internet, VPNs have become [...]