Avoid Phishing Attacks: Spot and how to Avoid Phishing Scams and Protect Yourself In today’s digital landscape, understanding and avoiding phishing attacks is crucial for [...]
Artificial Intelligence in Modern Cybersecurity: Exploring the Role of AI in Cybersecurity. In an era where digital threats are constantly evolving, the integration of artificial [...]
Cyber Hygiene: Best Practices for Individuals and Organisations for Enhanced Security In today’s digital age, cybersecurity is paramount for both individuals and organizations. Cyber hygiene, [...]
Cybersecurity in Healthcare: Protect Patient Data and Systems In today’s digital age, the healthcare sector faces unprecedented cybersecurity risks. The importance of cybersecurity in healthcare [...]
Top 10 Cybersecurity Threats Facing Enterprises Today & Associated Risks: Cyber Security Threats Update In an increasingly interconnected world, understanding the evolving landscape of cyber [...]
Remote Code Execution (RCE) Explained: Understanding RCE Attacks AI Platforms In today’s interconnected digital landscape, safeguarding your enterprise against cyber threats is paramount. Remote Code [...]
Top 8 Open-Source Threat Detection Tools for 2025 As we advance into 2025, the landscape of cybersecurity continues to evolve, presenting both challenges and opportunities [...]
Why Cyber Hygiene Definition & Checklist: Your Foundation for Good Security In the digital age, where cyber threats are ever-evolving, maintaining a robust cybersecurity posture [...]
Securing Your IoT Device: Internet of Things in Smart Cybersecurity Tips In an increasingly interconnected world, the Internet of Things (IoT) has revolutionized how we [...]
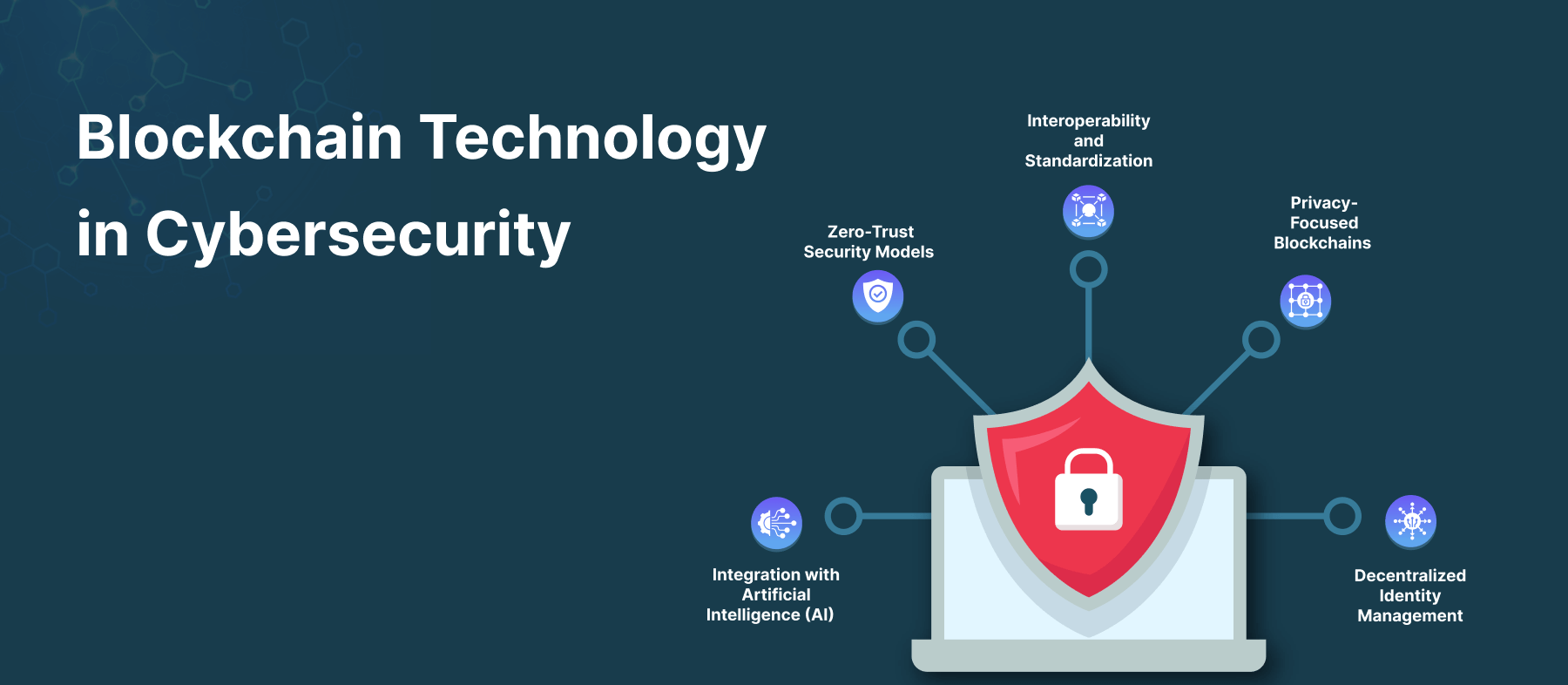
In an era defined by the increasing reliance on technology, understanding blockchain and its implications for cybersecurity is more important than ever. digital transformation, the [...]