VMware HCX Vulnerability Let Attackers Inject Malicious SQL Queries VMware has disclosed a critical security vulnerability in its HCX platform, a key component for hybrid [...]
Nation-State Actors Exploiting Ivanti CSA 0-days To Compromise Victims’ Networks Researchers have uncovered a sophisticated attack campaign targeting Ivanti Cloud Services Appliance (CSA) users. Nation-state [...]
What is Banner Grabbing? Types, Features & How it Works! Both hackers and security professionals employ various techniques to gather information about computer systems and [...]
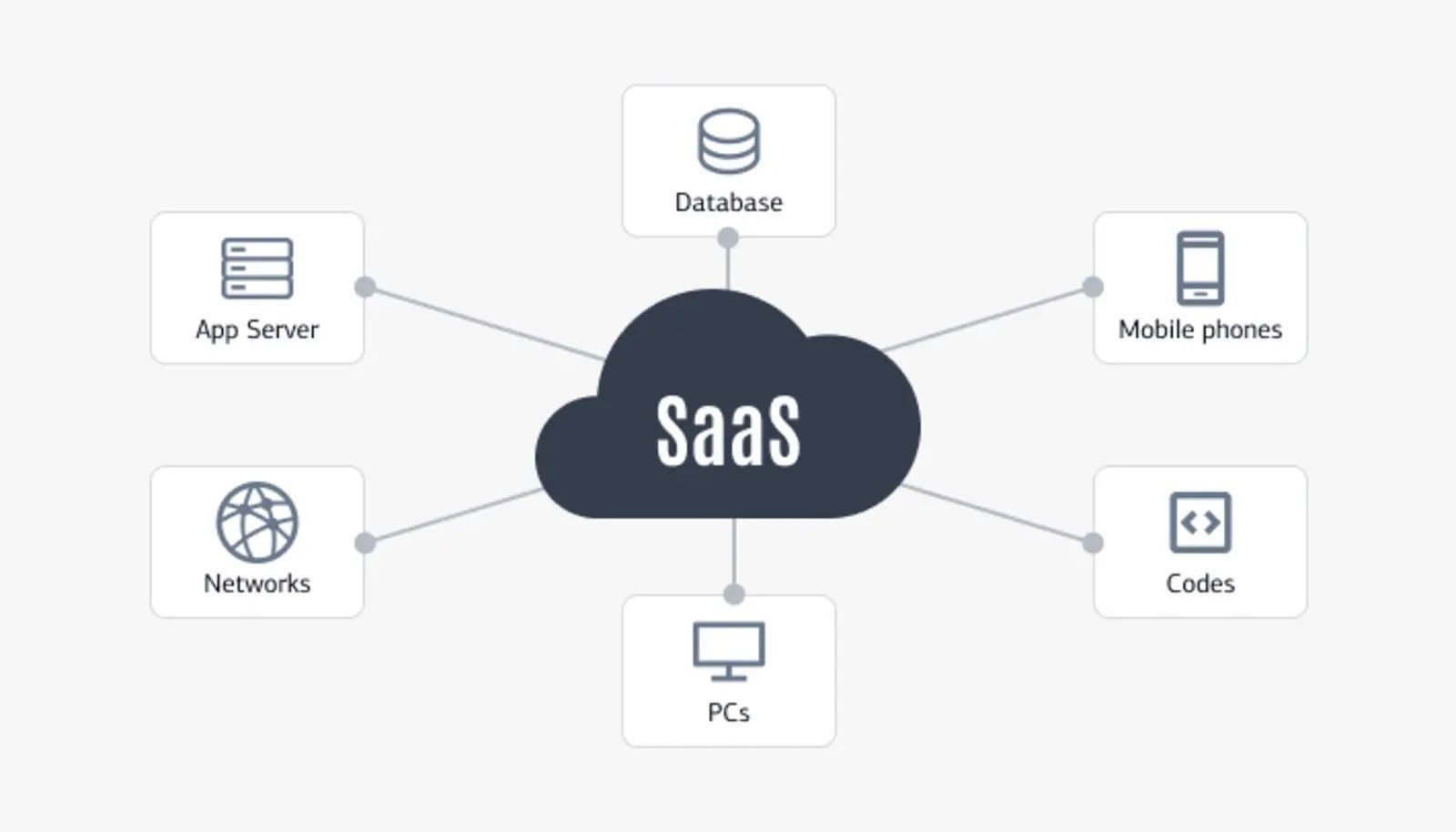
SaaS Product Management: Definition, Process & Best Practices. The software-as-a-service (SaaS) industry has exploded in recent years. As more businesses adopt cloud-based solutions, the market [...]
AI-Powered Networking: Smarter Connections for a Hyperconnected World “AI-Powered Networking: Smarter Connections for a Hyperconnected World” refers to how artificial intelligence (AI) technologies are [...]
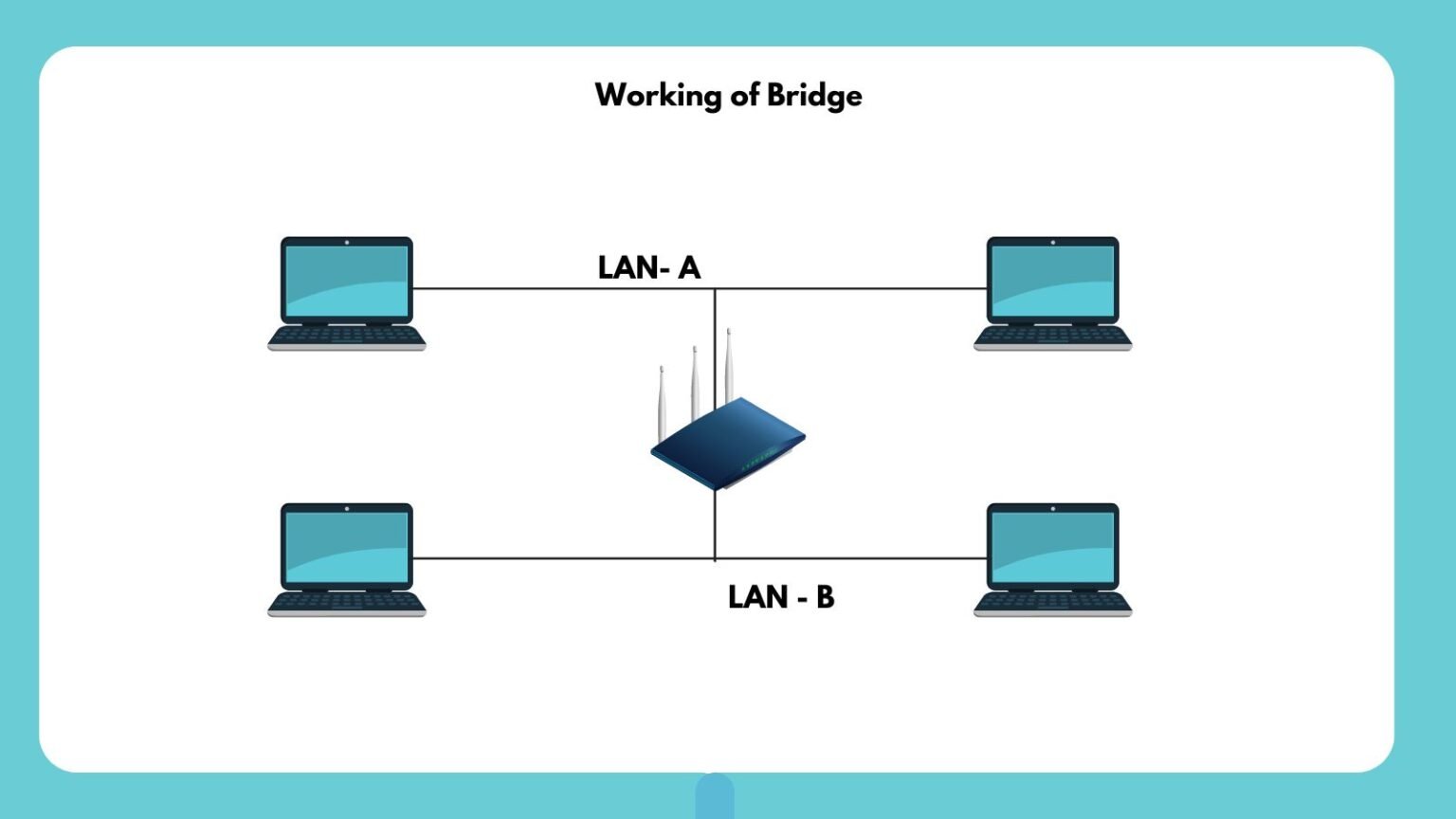
What is Bridge in Computer Network? Types, Uses & Functions In computer networks, various devices work together in computer networks to ensure seamless communication between network segments. [...]
CISA Warns of Fortinet RCE Vulnerability Actively Exploited The Cybersecurity and Infrastructure Security Agency (CISA) has issued a critical warning regarding a remote code execution [...]
Palo Alto Warns of Critical Flaw That Let Attackers Takeover Firewalls Palo Alto Networks, a leading cybersecurity company, has issued an urgent warning to its [...]
Cisco Small Business Routers Vulnerabilities Allow Attacker Exploits It Remotely In a recent security advisory, Cisco has disclosed multiple vulnerabilities affecting its Small Business RV340, [...]
Ivanti Endpoint Manager Vulnerability Public Exploit is Now Used in Cyber Attacks The Cybersecurity and Infrastructure Security Agency (CISA) has announced the addition of a [...]