The integrity of hardware is foundational to cybersecurity. As systems become more interconnected and reliance on digital infrastructure escalates, concerns around potential hidden control [...]
A silent, fundamental flaw within the aged yet ubiquitous HTTP/1.1 protocol now poses a critical threat to millions of websites. This decades-old ambiguity at [...]
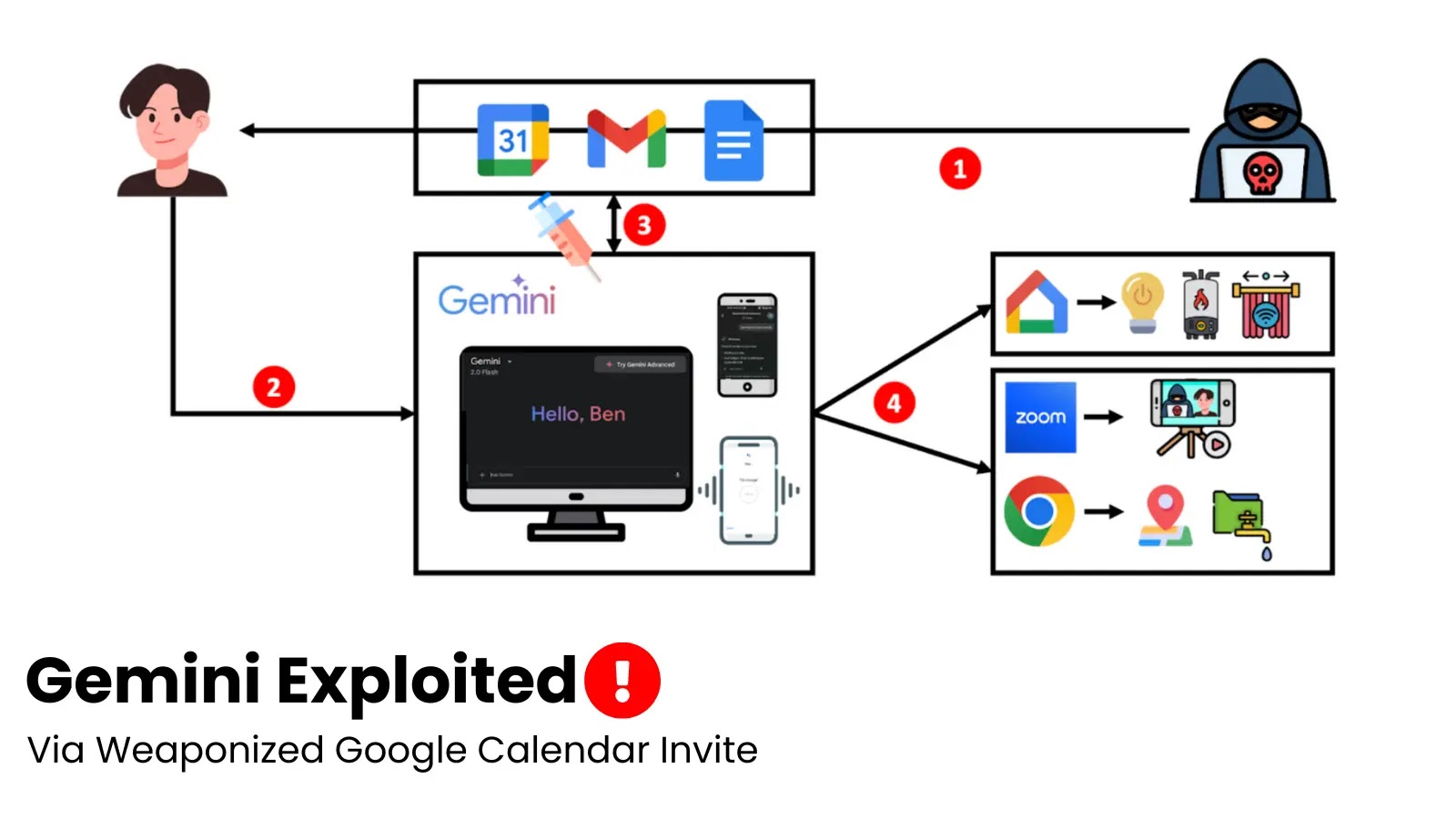
The lines between our digital assistants and our personal lives are blurring, bringing convenience but also unprecedented security risks. Imagine an attacker leveraging your seemingly [...]
In the high-stakes world of cybersecurity, speed is paramount. While security teams work diligently to implement robust defenses, threat actors are continuously innovating, finding [...]
In the rapidly evolving digital world, cybersecurity has become a cornerstone of protecting organizational integrity and data privacy. Artificial intelligence is at the forefront of [...]
In today’s digital age, ensuring the security of your wireless network is more critical than ever. As businesses and individuals increasingly rely on wireless connectivity, [...]
Unpacking CVE-2025-53786: The New Exchange Server Privilege Escalation Threat A critical security vulnerability has emerged within Microsoft Exchange Server hybrid deployments, posing a significant [...]
Cloud security is a shared responsibility, and while service providers like Amazon Web Services (AWS) build robust infrastructure, the configuration and management of applications [...]
The digital landscape is a minefield of both innovation and deception. For cybersecurity professionals, staying ahead of sophisticated threats is paramount, especially when those [...]
Managed Service Providers (MSPs) and small businesses face an unrelenting barrage of cyber threats. Among the most insidious are the sophisticated ransomware operations, Akira [...]