The digital landscape is relentlessly shaped by innovation, but with every new tool comes the potential for new vulnerabilities. A critical flaw has recently [...]
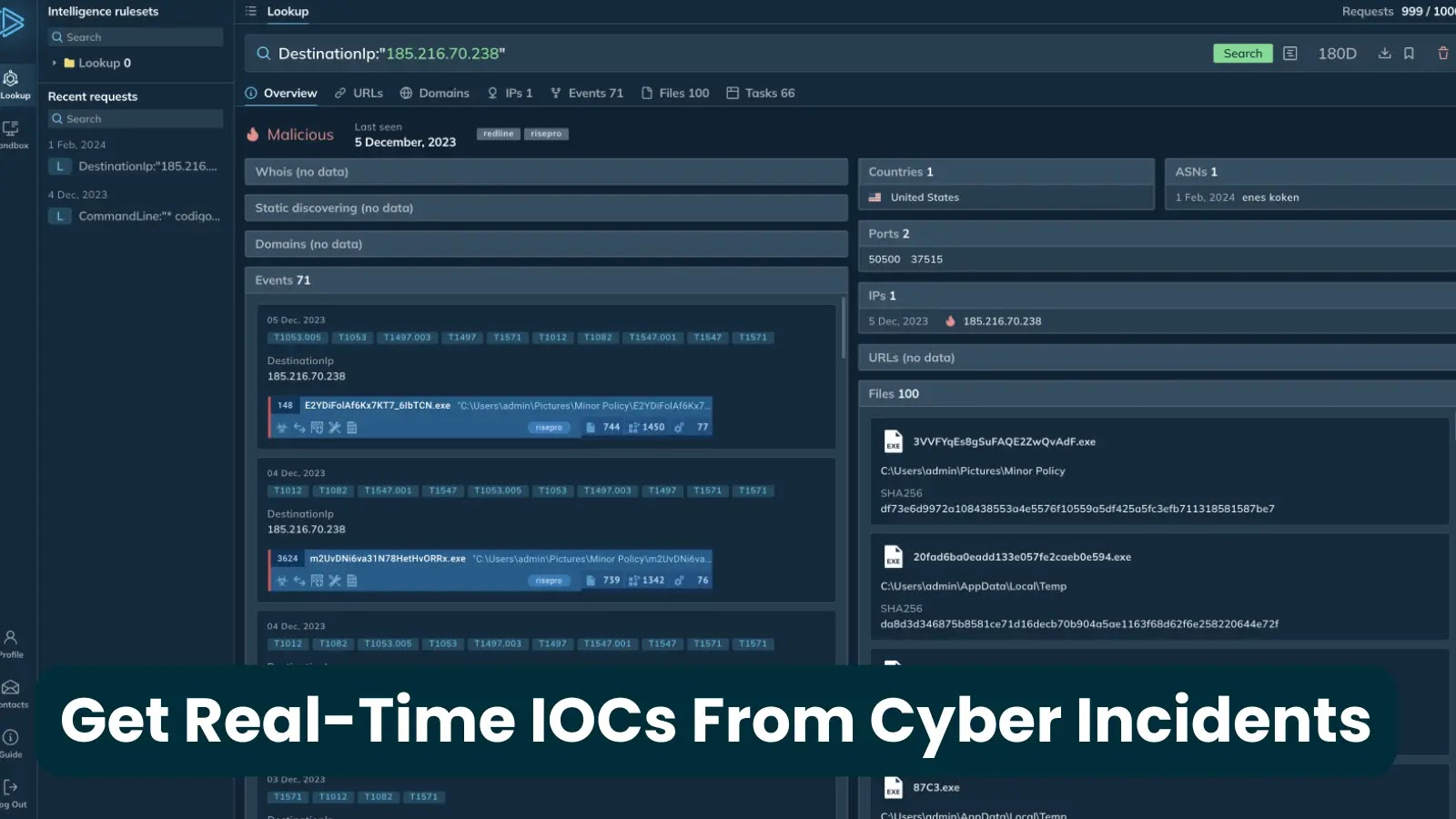
In the relentless battle against cyber threats, mere reactivity is a losing strategy. Proactive defense hinges on immediate access to critical intelligence. For security [...]
The Silent Takeover: How Threat Actors Are Weaponizing RMM Tools to Seize Control and Steal Data Imagine your IT team’s most trusted tool, designed [...]
In the dynamic landscape of enterprise security, the emergence of a critical vulnerability, especially one under active exploitation, demands immediate attention. Organizations leveraging Trend [...]
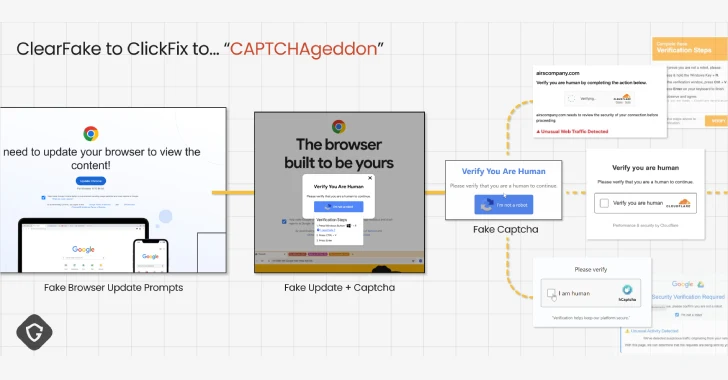
ClickFix Malware Campaign Exploits CAPTCHAs to Spread Cross-Platform Infections The digital threat landscape constantly evolves, with new attack methodologies pushing the boundaries of social engineering [...]
Cisco Hacked: Understanding the Vishing Attack That Compromised User Data A recent cyberattack on Cisco has highlighted the persistent threat of sophisticated social engineering [...]
Unmasking MCPoison: A Critical RCE Vulnerability in Cursor IDE In the rapidly evolving landscape of AI-powered development tools, security vulnerabilities can have far-reaching consequences [...]
Navigating the New SEC Compliance Mandate: Your Network Security Checklist for Audit Readiness The landscape of cybersecurity compliance has shifted dramatically. With new SEC [...]
Secure Socket Layer (SSL) certificates, more accurately known as Transport Layer Security (TLS) certificates, are the silent guardians of digital trust. They underpin the security [...]
Unlocking the Future of Software Security: Microsoft’s $5 Million Zero Day Quest The digital landscape is a constant battleground, with new threats emerging daily. [...]