Canon Caught in Clop Ransomware Net via Oracle E-Business Suite 0-Day: A Deep Dive The digital threat landscape continues its relentless expansion, and the [...]
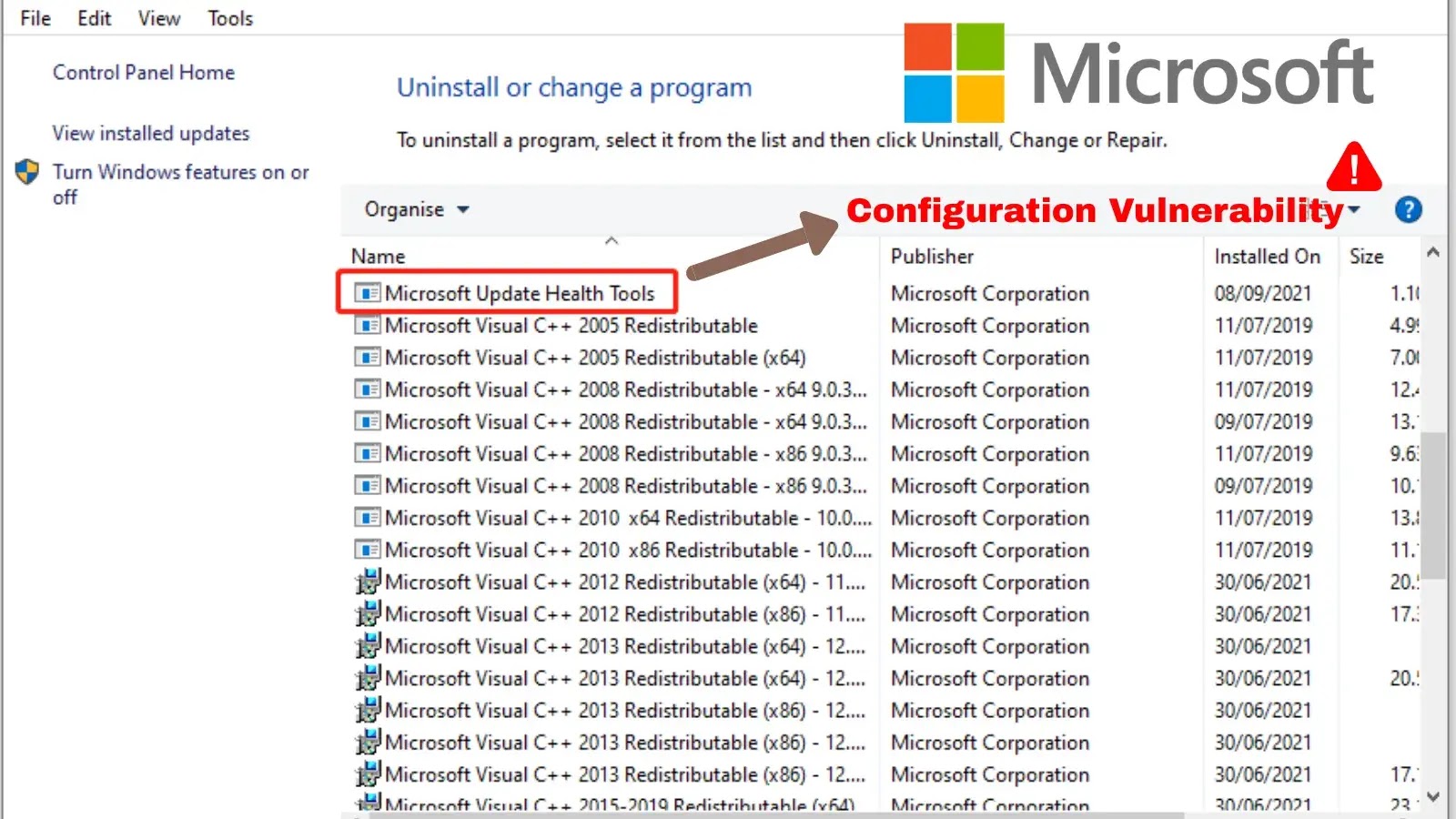
Unpacking a Critical Flaw: RCE in Microsoft’s Update Health Tools The intricate dance between maintaining a secure IT environment and ensuring operational efficiency often [...]
Critical HashiCorp Vault Vulnerability: Unauthenticated Access via Terraform Provider Flaw A severe security vulnerability has been identified within HashiCorp’s Vault Terraform Provider, posing a [...]
Navigating the Evolving Threat Landscape: The Imperative of Exposure Management The cybersecurity paradigm has shifted. Reactive defense, characterized by perimeter security and incident response, is [...]
Compliance Automation: Automate Compliance With Rules as Code A Step By Step Guide In today’s rapidly evolving technological landscape, organizations face the daunting task of [...]
How Guide to Build A Secure Software Supply Chain Security: Best Practices Guide to Software Supply Chain In the digital era, secure software development is [...]
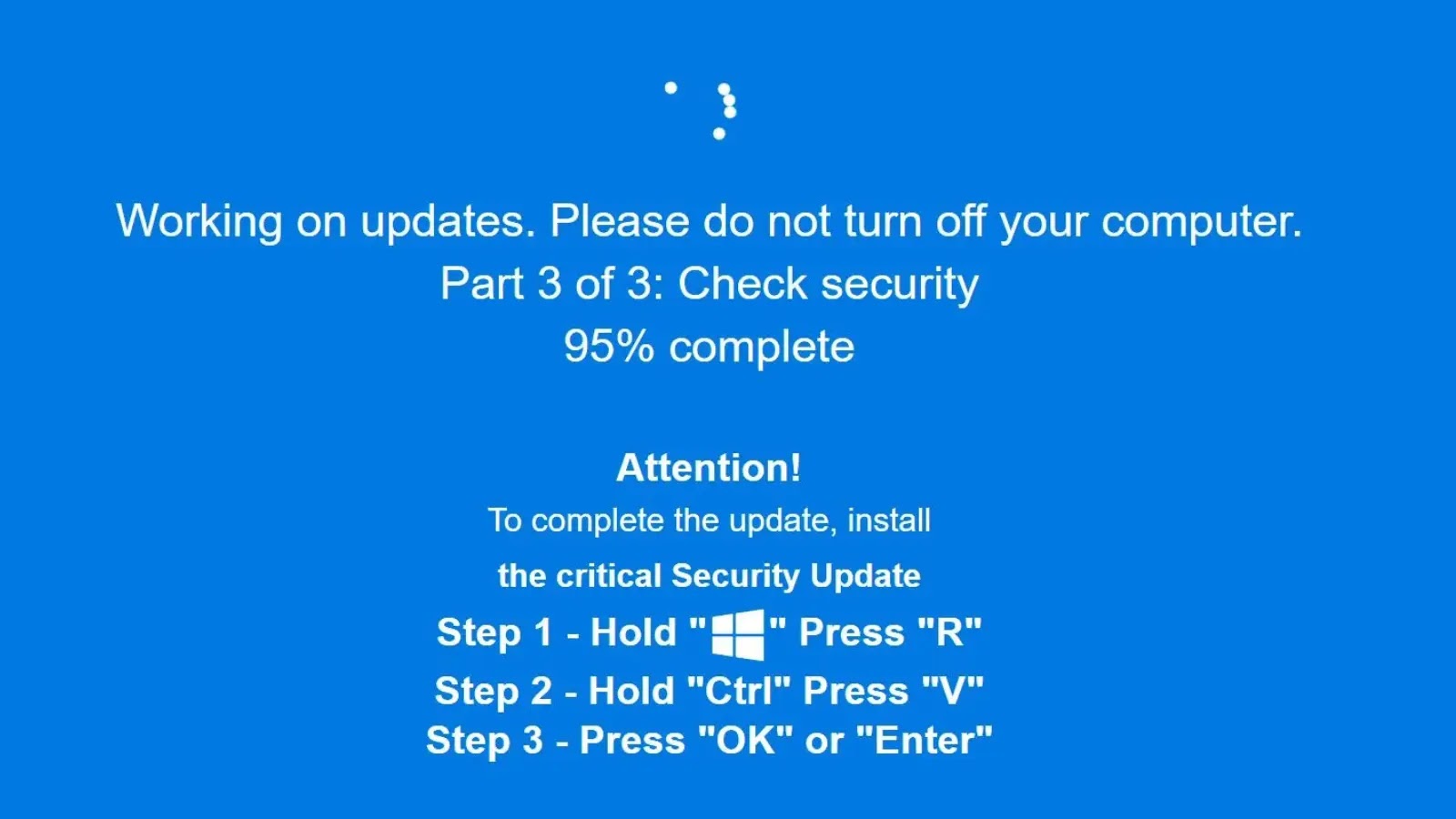
The Devious Disguise: ClickFix Attack Hides Malware in Fake Windows Updates via Steganography A new, highly concerning cyber threat has emerged, leveraging sophisticated social [...]
The AI Paradox: How GPT-3.5 and GPT-4 Are Fueling Autonomous Malware The landscape of cyber warfare is undergoing a seismic shift. Large Language Models [...]
A disturbing trend in software supply chain attacks has emerged, directly targeting users and their valuable cryptocurrency assets. The seemingly innocuous act of installing [...]
In the intricate landscape of enterprise cybersecurity, internal communications remain the lifeblood of organizations. Email, whether hosted on-premises via Microsoft Exchange or leveraging cloud [...]