How Small Businesses Use FortiGate FG-30G To Cut Threats By 45% Firewall: Fortinet Is the 30G Right for Your Network? In an era defined by [...]
SSL/SSH Inspection Explained: Deep Packet Inspection Analysis on FortiGate SSH Inspection and SSL Inspection. In the ever-evolving landscape of cybersecurity threats, safeguarding your enterprise’s data [...]
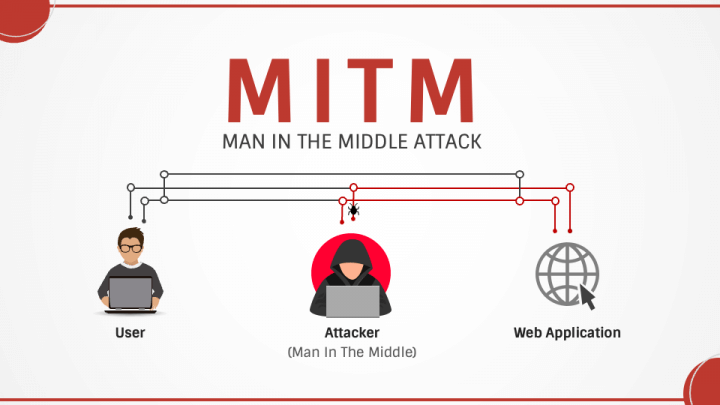
Preventing Man-in-the-Middle Attacks at layer 2: A Security Guide In today’s interconnected digital landscape, understanding and mitigating cyber threats is paramount. This guide provides essential [...]
Network Switch Cyber Security Best Practices for Switch Deployment In today’s interconnected world, the security of your network is paramount. Network switches, the unsung heroes [...]
Cloud Security Risk: Mitigation Strategies for Cloud Computing In today’s digital age, cloud computing has become an indispensable part of modern business. As organizations increasingly [...]
How to Audit Layer 2 Switch Configurations In today’s interconnected world, a properly configured Layer 2 network is the backbone of efficient and secure data [...]
PCI DSS Network Segmentation for Compliance: Achieving PCI DSS Compliance In today’s digital landscape, ensuring the security of cardholder data is paramount for any organization [...]
Cybersecurity Predictions for 2026: what’s next The Future of Cyber Security As we look ahead to 2026 and beyond, the future of cyber security presents [...]
Financial Services Sector Cybersecurity: Regulatory Pressure and Response to Threats and Protection In today’s digital age, the financial services sector faces unprecedented cybersecurity challenges. The [...]
Wireless Network Security: Cybersecurity in Layer 2 Wireless Access Point Protection In today’s interconnected world, a secure wireless network is indispensable. The proliferation of wireless [...]