Hackers Actively Exploiting Zyxel 0-day Vulnerability to Execute Arbitrary Commands A significant zero-day vulnerability in Zyxel CPE series devices, identified as CVE-2024-40891, is being actively exploited by [...]
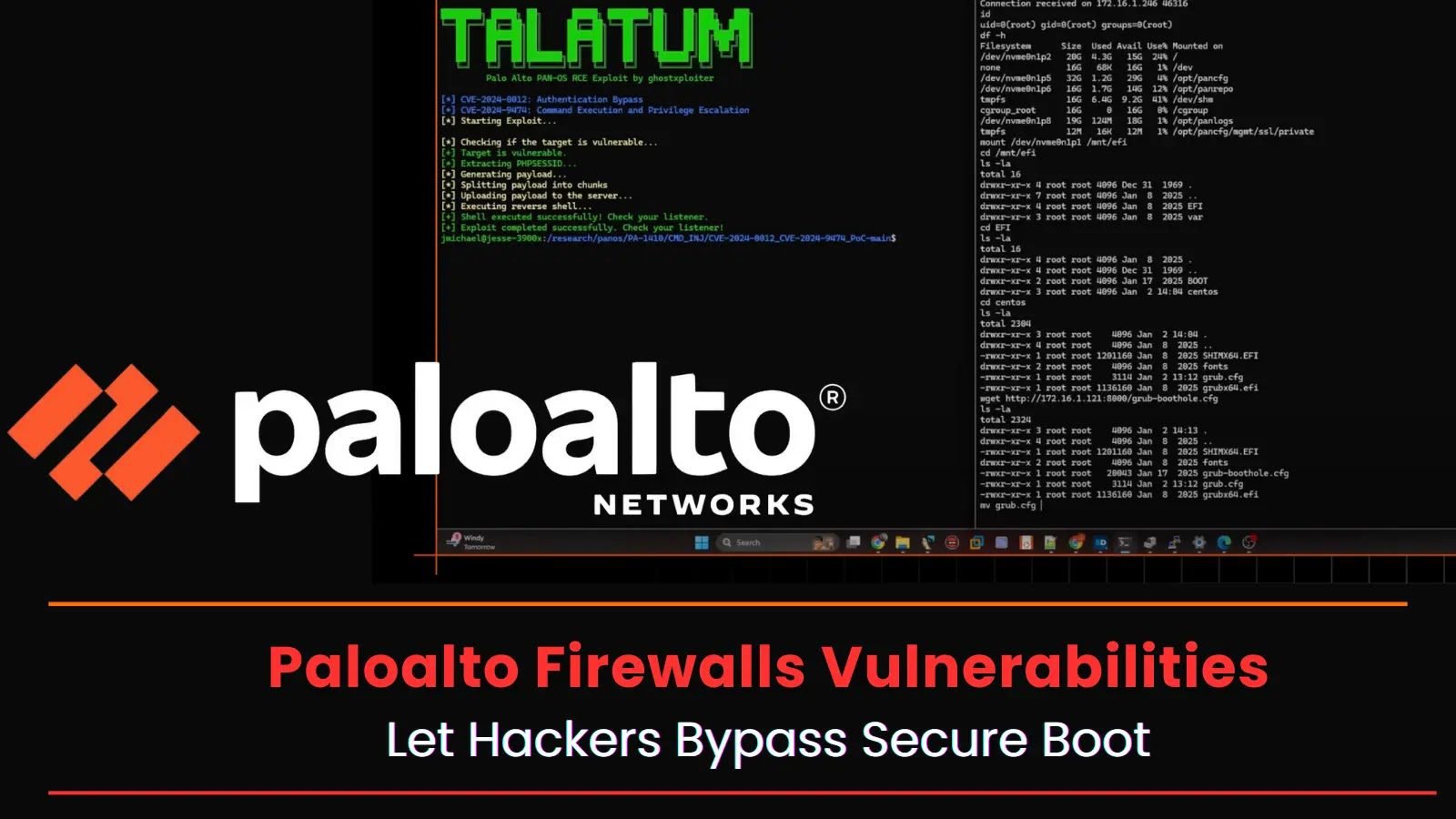
Critical Palo Alto Firewall Vulnerabilities Let Hackers Bypass Secure Boot & Exploit Firmware A recent cybersecurity report has identified critical vulnerabilities in Palo Alto Networks [...]
SonicWall 0-day Vulnerability Exploited In Attacks Execute Arbitrary OS Commands A critical security vulnerability, tracked as CVE-2025-23006, has been identified in SonicWall’s SMA1000 Appliance Management [...]
Hackers Exploited Fortigate 0-Day & Leaked 15,000+ Firewall Configs & Passwords A hacking collective known as the “Belsen Group” has released over 15,000 unique FortiGate [...]
Palo Alto Networks Expedition Tool Vulnerability Exposes Firewall Credentials Multiple vulnerabilities in Palo Alto Networks’ Expedition migration tool have been discovered, potentially exposing sensitive firewall [...]
Top 15 Firewall Management Tools in 2025 Firewall management tools are essential for maintaining network security by monitoring and controlling incoming and outgoing traffic based [...]
ASUS Routers Vulnerabilities Allows Arbitrary Code Execution ASUS, a leading networking equipment manufacturer, has issued a critical security advisory for several router models. The company [...]
Critical Sophos Firewall Vulnerabilities Let Attackers Execute Remote Code Sophos warns of three critical security vulnerabilities in its Sophos Firewall product. These vulnerabilities could potentially [...]
Palo Alto Warns of Hackers Exploiting RCE Flaw in Firewall Management Interfaces Palo Alto Networks has issued an urgent security warning regarding the exploitation of [...]
Palo Alto Networks Warns Of Critical PAN-OS Remote Code Execution Vulnerability Palo Alto Networks has issued an urgent warning about a potential critical remote code [...]