The Silent Swipe: ToxicPanda Android Malware Infiltrates 4500+ Devices Mobile banking applications have become indispensable, offering unparalleled convenience for managing finances. However, this convenience [...]
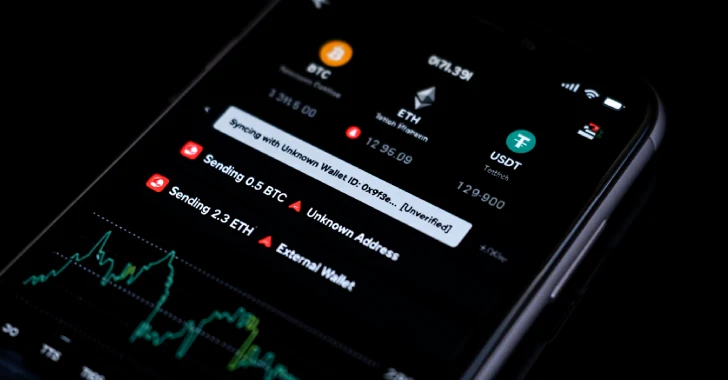
In the rapidly evolving landscape of digital finance, the allure of quick returns on cryptocurrency investments presents a fertile ground for malicious actors. A new, [...]
In the relentless landscape of cybersecurity, rapid response to active exploitation is paramount. Google has once again demonstrated its commitment to Android security with [...]
The digital battleground intensifies as a cunning and persistent threat actor, the Pakistan-linked APT36 (also known as “Mythic Leopard” or “Operation Transparent Tribe”), sets [...]
The digital landscape is fraught with hidden dangers, and even the most cutting-edge tools can harbor critical vulnerabilities. This is particularly true for applications at [...]
The digital landscape is relentlessly shaped by innovation, but with every new tool comes the potential for new vulnerabilities. A critical flaw has recently [...]
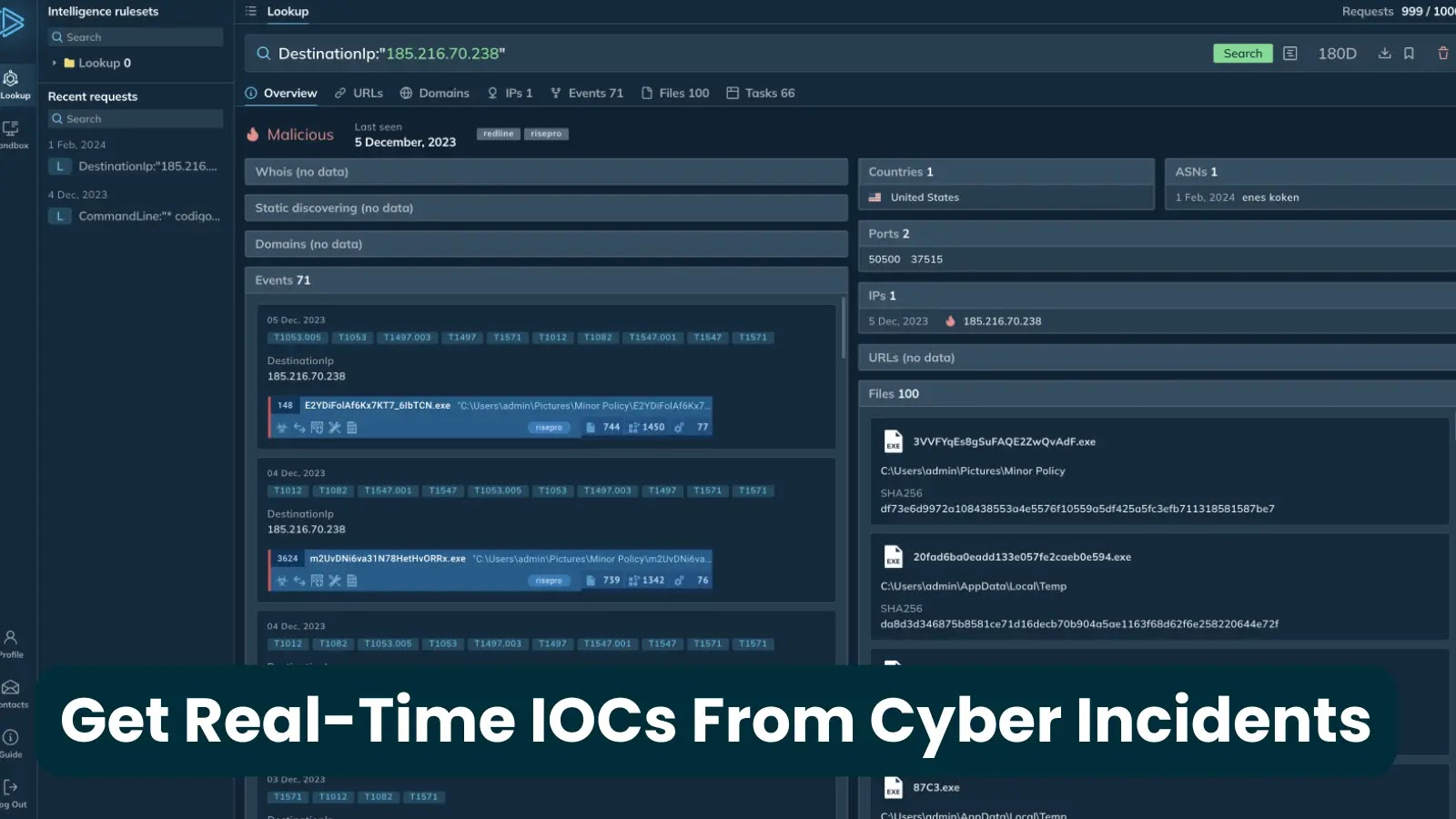
In the relentless battle against cyber threats, mere reactivity is a losing strategy. Proactive defense hinges on immediate access to critical intelligence. For security [...]
The Silent Takeover: How Threat Actors Are Weaponizing RMM Tools to Seize Control and Steal Data Imagine your IT team’s most trusted tool, designed [...]
In the dynamic landscape of enterprise security, the emergence of a critical vulnerability, especially one under active exploitation, demands immediate attention. Organizations leveraging Trend [...]
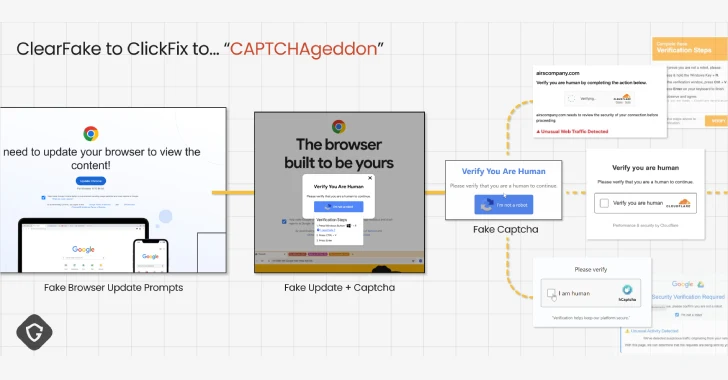
ClickFix Malware Campaign Exploits CAPTCHAs to Spread Cross-Platform Infections The digital threat landscape constantly evolves, with new attack methodologies pushing the boundaries of social engineering [...]