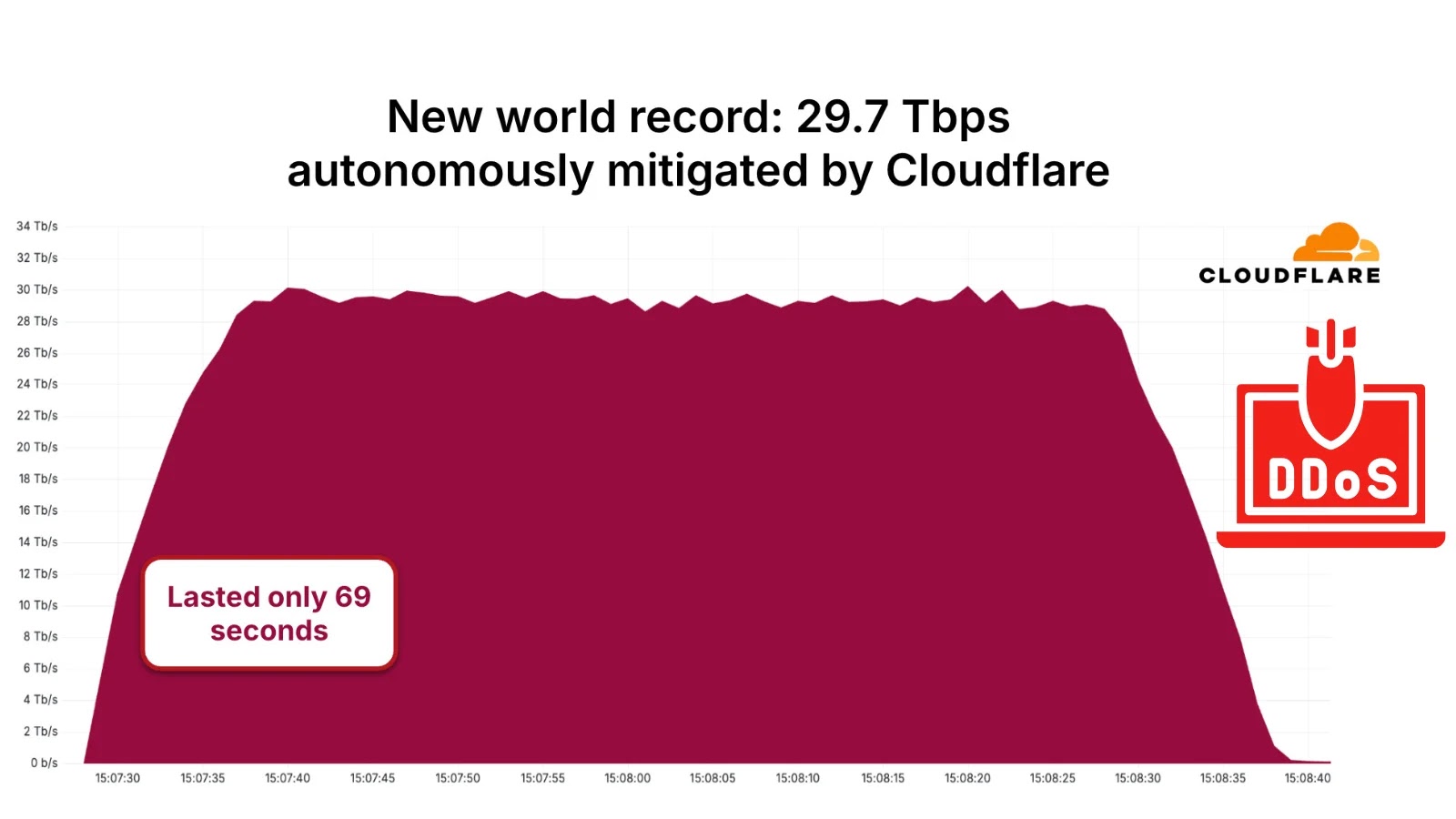
29.7 Tbps DDoS Attack Via Aisuru Botnet Breaks Internet With New World Record
The internet, a foundational pillar of modern society, just experienced an unprecedented assault. A staggering 29.7 Terabits per second (Tbps) Distributed Denial-of-Service (DDoS) attack originating from the Aisuru botnet shattered previous records, exposing critical vulnerabilities in global network infrastructure. This isn’t merely an inconvenience; it’s a stark reminder of the escalating arms race in cyber warfare and the urgent need for robust defense mechanisms.
This post delves into the specifics of this record-breaking cyberattack, examining its implications and outlining essential strategies for cybersecurity professionals to bolster their defenses against the evolving threat landscape of multi-terabit DDoS assaults.
The Aisuru Botnet: A New Benchmark in Cyber Destructiveness
The Aisuru botnet has etched its name into cybersecurity history with an attack volume that eclipses all predecessors. At 29.7 Tbps, this DDoS blast significantly surpasses the previous record of 22 Tbps, which was quietly mitigated by Cloudflare in Q3 2023. Such an immense volume of malicious traffic has the potential to overwhelm even the most resilient networks, leading to widespread service disruptions and economic fallout.
Understanding the architecture and methods employed by the Aisuru botnet is crucial. While specific details of its command-and-control infrastructure and propagation methods are still emerging, the sheer scale of this attack suggests a highly sophisticated and rapidly expanding network of compromised devices. Expect further analysis on this particular botnet and its unique characteristics from threat intelligence researchers in the coming months.
Implications of Multi-Terabit DDoS Attacks
The transition from gigabit to multi-terabit DDoS attacks marks a significant paradigm shift for internet infrastructure. These attacks are no longer fringe events; they are now a clear and present danger to the stability of global digital services. The core implications include:
- Internet Core Fragility: Even robust internet backbones and critical service providers are vulnerable under such extreme load, potentially leading to cascading failures.
- Economic Disruption: Downtime for major online services, e-commerce platforms, and financial institutions translates directly into massive financial losses.
- Enhanced Attack Sophistication: The record-breaking volume points to advanced orchestration capabilities within botnets, potentially leveraging new amplification techniques or a vast array of compromised devices.
- Increased Mitigation Costs: Defending against such large-scale attacks requires significant investment in advanced DDoS mitigation services, specialized hardware, and expert personnel.
Remediation Actions and Proactive Defenses Against DDoS Threats
In the face of unprecedented DDoS attacks, proactive measures and robust mitigation strategies are paramount. Organizations must move beyond reactive responses and build resilient architectures designed to withstand multi-terabit assaults.
- Implement Advanced DDoS Mitigation Services: Partner with specialized DDoS mitigation providers that offer always-on, high-capacity scrubbing centers capable of handling terabit-scale attacks. These services can detect, analyze, and filter malicious traffic before it reaches your infrastructure.
- Distributed Network Architecture: Distribute your applications and services across multiple geographical regions and cloud providers. This reduces single points of failure and allows for traffic rerouting during an attack.
- Bandwidth Provisioning: Ensure your network infrastructure has sufficient excess bandwidth to absorb significant traffic spikes, even legitimate ones, and especially during a low-level DDoS attempt.
- Rate Limiting and Traffic Filtering: Implement strong rate-limiting policies at the edge of your network and configure Web Application Firewalls (WAFs) to filter known malicious traffic patterns.
- Network Monitoring and Anomaly Detection: Deploy advanced network monitoring solutions that can detect anomalous traffic patterns indicative of a DDoS attack in its nascent stages. Early detection is critical for effective mitigation.
- Incident Response Plan Development: Develop and regularly test a comprehensive DDoS incident response plan. This plan should clearly define roles, responsibilities, communication protocols, and escalation procedures.
- Educate Your Teams: Ensure your cybersecurity and IT operations teams are well-versed in DDoS attack vectors, mitigation techniques, and incident response procedures.
Tools for DDoS Detection and Mitigation
Effective DDoS defense relies on a combination of robust services and specialized tools. Here are some essential categories and examples:
| Tool/Service Category | Purpose | Link |
|---|---|---|
| Cloud-based DDoS Mitigation | Filters and absorbs large-scale DDoS attacks before they reach the target network. | Cloudflare / Akamai / AWS Shield |
| Network Traffic Analysis (NTA) | Monitors network traffic for anomalies and potential attack signatures. | Splunk / IBM QRadar |
| Web Application Firewalls (WAF) | Protects web applications from various attacks, including some L7 DDoS. | F5 ASM / Imperva WAF |
| Router/Switch ACLs | Basic filtering of traffic based on source/destination IP, port, etc., at the network edge. | (Vendor documentation, e.g., Cisco / Juniper) |
Looking Ahead: The Evolving DDoS Landscape
The 29.7 Tbps attack from the Aisuru botnet serves as a stark warning: the capabilities of malicious actors are advancing at an alarming rate. Organizations can no longer afford to underestimate the threat of DDoS attacks. Focusing on layered defenses, continuous monitoring, and strategic partnerships with security vendors is not just a best practice, but a necessity for maintaining operational continuity in an increasingly hostile digital environment.
The internet’s future resilience depends on a collective effort to secure its foundational infrastructure against these record-breaking threats. Proactive defense, rather than reactive mitigation, will be the differentiator for surviving the next wave of cyber assaults.





