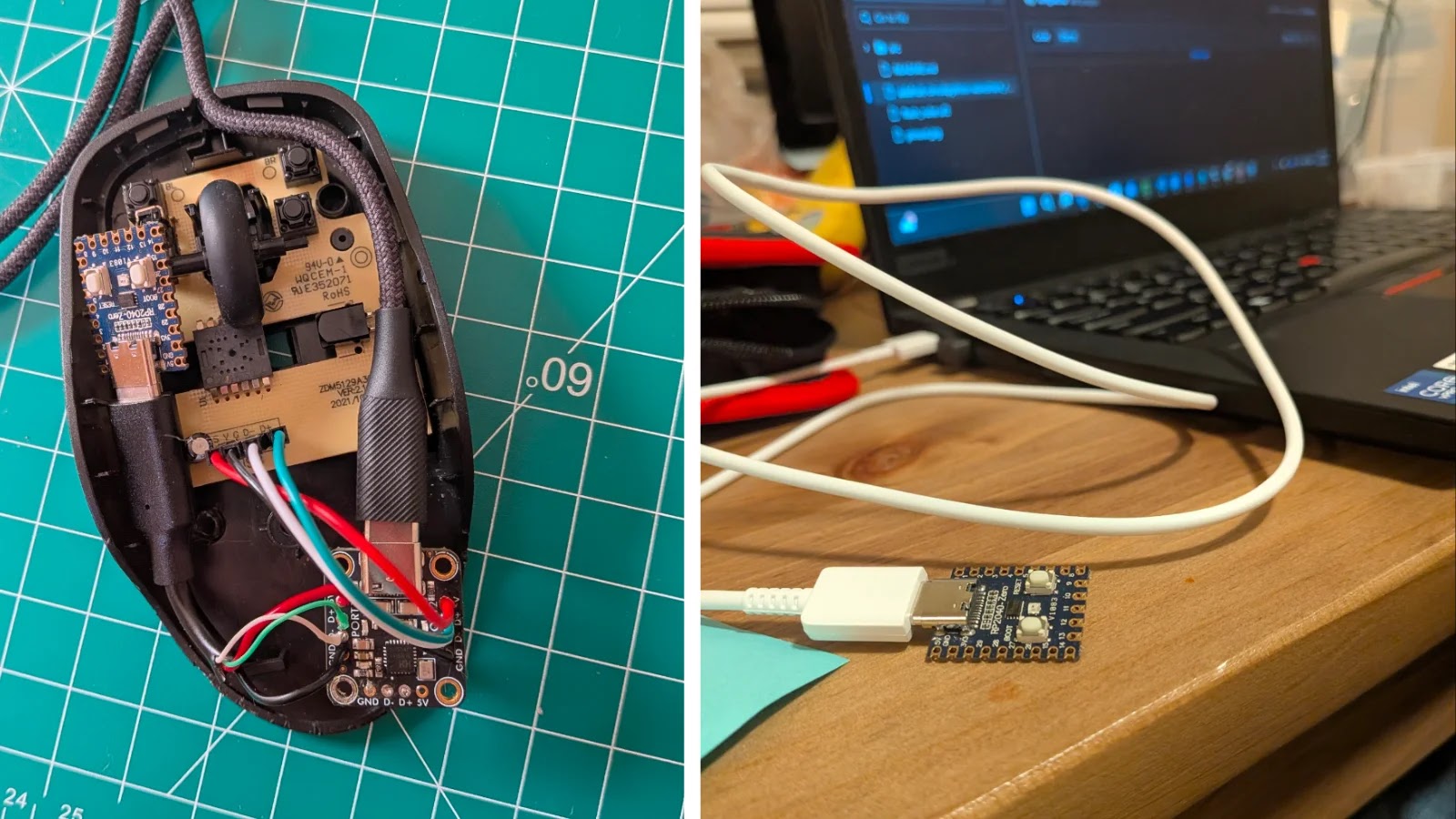
$44 Evilmouse Autonomously Executes Commands and Compromises Systems Once Connected
Imagine plugging in a seemingly innocuous computer mouse, only for it to autonomously execute malicious commands on your system, deliver reverse shells, or worse. This isn’t a scene from a cyberpunk movie; it’s the stark reality presented by “Evilmouse,” a $44 hardware implant that is ingeniously disguised and dangerously effective. In an era where hardware-based attacks are becoming increasingly sophisticated, understanding and mitigating such threats is paramount for any organization or individual.
The Devious Design of Evilmouse
The Evilmouse isn’t just another low-cost peripheral; it’s a covert keystroke injector cleverly concealed within the shell of a standard computer mouse. Drawing parallels to the notorious Hak5 Rubber Ducky, this device bypasses a significant layer of defense: human awareness. While vigilant users might question an unfamiliar USB drive, a mouse often raises no suspicion, especially in environments where peripheral sharing or hot-desking is common.
Its primary mechanism of attack involves autonomous payload execution. Once connected to a target system, the Evilmouse doesn’t wait for user interaction; it immediately begins to run pre-programmed instructions. These payloads can range from simple command execution to the delivery of sophisticated reverse shells, granting attackers remote access and control over the compromised system. The cost-effectiveness of $44 makes it an accessible tool for a wide range of malicious actors, from opportunistic attackers to those engaged in targeted industrial espionage.
How Evilmouse Bypasses Defenses
The effectiveness of the Evilmouse lies in its ability to exploit trust and familiarity. Here’s how it circumvents typical security measures:
- User Awareness Training: Most user awareness programs emphasize caution with unknown USB drives. A mouse, however, is often perceived as harmless, making it an ideal vector for social engineering attacks that bypass this training.
- Endpoint Detection and Response (EDR): While advanced EDR solutions might detect suspicious command execution, the initial connection and enumeration of the device itself might not trigger immediate alerts, especially if it registers as a legitimate human interface device (HID). The autonomous nature of the attack means that the malicious activity can begin before EDR has a chance to fully analyze the behavior.
- Physical Security: In environments with less stringent physical security, an attacker could briefly access a system to plug in such a device, leaving little to no trace of their presence once removed.
The Peril of HID Emulation
At its core, the Evilmouse leverages Human Interface Device (HID) emulation. HIDs are devices like keyboards and mice that are universally trusted by operating systems. When an Evilmouse is plugged in, the system recognizes it as a legitimate input device, bypassing many security checks designed for storage devices or network adapters. This trust allows the device to “type” commands rapidly and imperceptibly, effectively acting as if a user is physically interacting with the keyboard. This method is incredibly difficult for traditional antivirus software to detect, as it operates at a fundamental level of device interaction.
Remediation Actions and Protective Measures
Combating threats like Evilmouse requires a multi-layered approach that addresses physical security, endpoint protection, and user education. Organizations and individuals must be proactive in their defense strategies.
- Implement Strict USB Device Controls: Utilize software and hardware solutions to restrict or monitor the use of unknown USB devices. This includes whitelisting approved devices and blocking mass storage or HID devices not explicitly permitted.
- Enhance Physical Security: Control access to workstations and servers. Ensure that USB ports are physically secured or monitored, especially in public-facing or high-traffic areas. Consider implementing tamper-evident seals on critical ports.
- Advanced Endpoint Monitoring: Deploy EDR solutions that focus on behavioral analysis and can detect anomalous command execution, even if initiated by a trusted HID. Look for activity that deviates from normal user patterns.
- Regular User Training Revisions: Update security awareness training to include hardware-based threats. Educate users about the dangers of plugging in any unfamiliar peripheral, regardless of its appearance. Emphasize reporting suspicious devices.
- Principle of Least Privilege: Ensure that user accounts operate with the minimum necessary privileges. Even if a command execution occurs, limited privileges can contain the damage.
- Patch Management: While not directly preventing a hardware attack, keeping systems patched and updated minimizes the chances of secondary exploits being successful once a foothold is established.
Tools for Detection and Mitigation
While direct detection of the Evilmouse itself before insertion is challenging, several categories of tools can aid in detection and mitigation once its malicious activity begins or to prevent such devices from functioning:
| Tool Name | Purpose | Link |
|---|---|---|
| EnCase Forensic Suite | Forensic analysis of system activity post-compromise; can help identify command execution trails. | https://www.guidancesoftware.com/products/security/encase-forensic |
| Sysmon (Windows Sysinternals) | Detailed logging of system activity, including process creation, network connections, and driver loads, which can aid in identifying malicious activity from a keystroke injector. | https://docs.microsoft.com/en-us/sysinternals/downloads/sysmon |
| Port Control Software (Various Vendors) | Software solutions for managing and restricting access to USB ports, such as Device Lock DLP. | https://www.devicelock.com/ |
| USB Port Locks (Hardware) | Physical locks for USB ports to prevent unauthorized device insertion. | (Varies by vendor, search for “USB port locks”) |
| Endpoint Detection and Response (EDR) Platforms | Behavioral analysis to detect anomalous process execution or network activity originating from user sessions. (e.g., CrowdStrike Falcon, SentinelOne) | (Varies by vendor) |
Conclusion
The $44 Evilmouse serves as a stark reminder that cyber threats are constantly evolving, moving beyond purely software-based vulnerabilities to leverage the physical layer. Its ability to autonomously inject commands and compromise systems by simply being plugged in highlights critical gaps in traditional security postures. By understanding the mechanism of such attacks, reinforcing physical security measures, implementing robust endpoint controls, and fostering continuous user education, organizations can significantly reduce their attack surface against these deceptively simple yet potent hardware implants.





