5 Sandbox Tools for Phishing Analysis in 2026
Navigating the Phishing Frontier: Essential Sandbox Tools for 2026
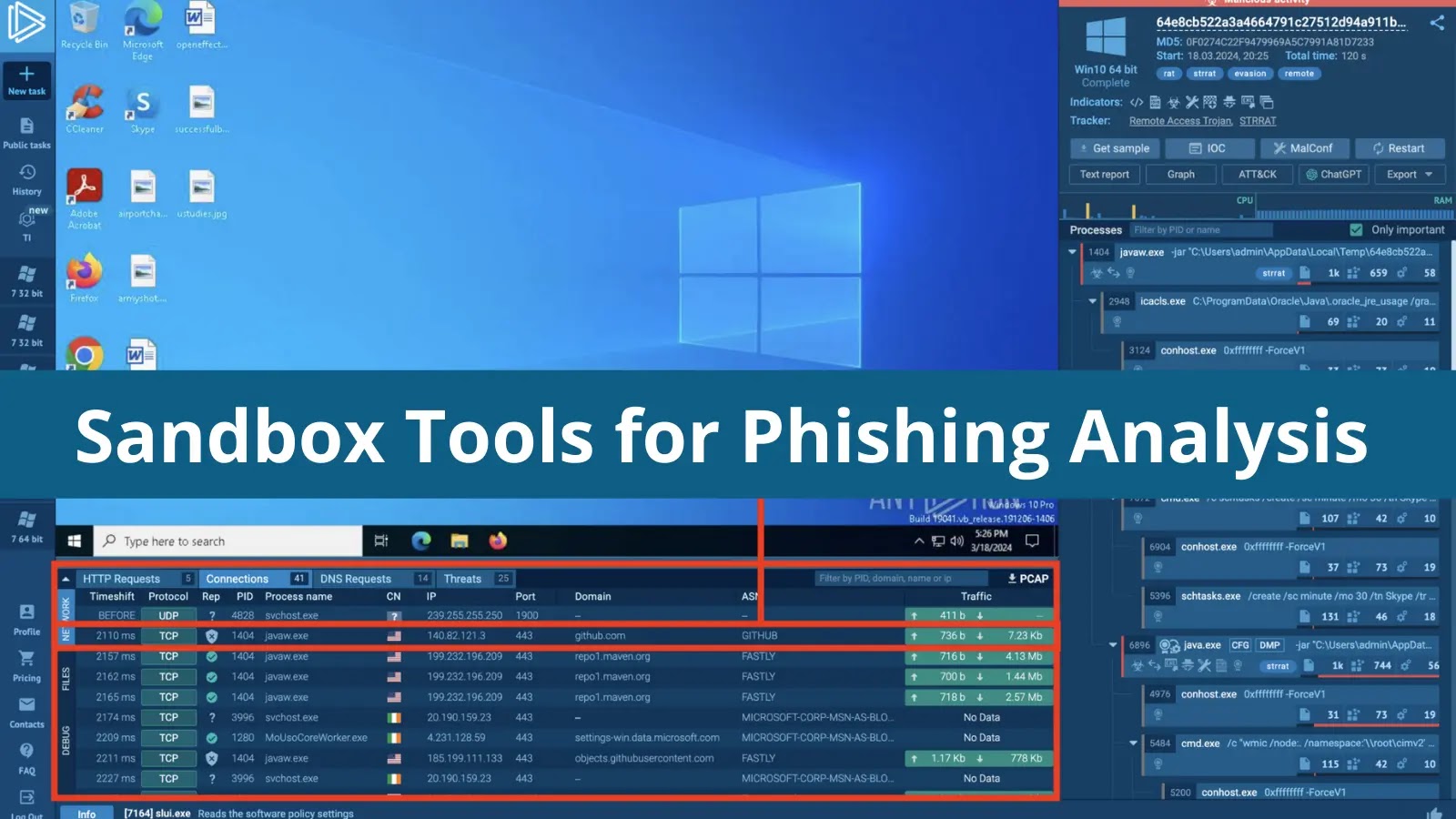
Phishing attacks continue to evolve in sophistication, bypassing traditional defenses and posing significant threats to organizations worldwide. For cybersecurity analysts, effectively dissecting and understanding these elusive threats is paramount. While numerous tools exist for probing phishing attempts, a robust malware analysis sandbox stands out as a singularly powerful solution. By seamlessly integrating both static and dynamic analysis techniques, these specialized environments excel at uncovering even the most complex phishing campaigns. This article delves into five top sandbox solutions that cyber professionals can leverage in 2026 to elevate their investigations and bolster their defenses.
The Power of Sandbox Analysis in Phishing Investigations
A sandbox provides a secure, isolated environment where suspicious files and URLs, commonly found in phishing attempts, can be executed and observed without risking the organization’s production systems. This controlled detonation allows analysts to thoroughly understand the malware’s behavior, identify Indicators of Compromise (IOCs), and extract crucial threat intelligence. The blending of analysis types is key:
- Static Analysis: This involves examining the code without executing it, looking for suspicious patterns, obfuscation techniques, and embedded URLs or scripts.
- Dynamic Analysis: This entails running the suspected malicious content within the sandbox and monitoring its interactions with the operating system, network, and file system. This reveals runtime behavior, C2 communications, and payload drops.
Modern sandboxes often incorporate advanced features like interactive analysis, allowing analysts to manually interact with the simulated environment, mimicking a user’s actions to trigger specific malware behaviors or bypass anti-analysis techniques. This level of control is invaluable when dealing with highly evasive threats.
Top 5 Sandbox Tools for Phishing Analysis in 2026
1. ANY.RUN
Widely recognized for its capabilities, ANY.RUN offers an interactive sandbox environment that provides complete control over the analysis process. This interactivity is a significant advantage when dissecting complex phishing attacks, enabling analysts to force specific actions or observe different execution paths. Its real-time monitoring and detailed reports make it a favorite for in-depth investigations, allowing analysts to trace execution flows, network connections, and system modifications caused by suspicious emails or attachments.
2. VMRay Analyzer
VMRay Analyzer distinguishes itself with its unique agentless monitoring approach, which allows it to detect and analyze even the most sophisticated and evasive malware. By avoiding the presence of an agent within the guest system, VMRay minimizes the chances of malware detecting the analysis environment. This tool provides deep insights into malware behavior, including process injections, anti-analysis checks, and obfuscated code, making it an excellent choice for uncovering advanced phishing threats.
3. Cuckoo Sandbox
As an open-source solution, Cuckoo Sandbox offers unparalleled flexibility and customization. Its strong community support means it’s continually evolving with new features and integrations. While it requires more setup and maintenance compared to commercial offerings, its extensibility makes it ideal for organizations that need to tailor their analysis environment precisely to their specific needs. Cuckoo is a powerful foundation for building a robust in-house phishing analysis platform.
4. Falcon Sandbox (CrowdStrike)
CrowdStrike’s Falcon Sandbox leverages cutting-edge technology to provide comprehensive threat intelligence and advanced behavioral analysis. Integrated with CrowdStrike’s broader cybersecurity platform, it offers a holistic view of threats, correlating sandbox analysis results with endpoint detection and response (EDR) data. This integration is crucial for understanding the wider implications of a phishing attack and accelerating incident response, especially for organizations already utilizing CrowdStrike’s ecosystem.
5. Intezer Analyze
Intezer Analyze focuses on code reuse detection and genetic analysis, providing a unique perspective on malware family identification. By breaking down malware into its genetic components, Intezer can quickly identify known code snippets, link new threats to existing families, and reveal unseen malware variants. This approach is highly effective in understanding the sophistication and origin of phishing payloads, enabling analysts to anticipate future attacks from the same threat actors.
Remediation Actions and Best Practices
While sandbox tools are indispensable for analysis, preventing and mitigating phishing attacks requires a multi-layered approach:
- User Education and Training: Regular training programs to help employees recognize and report phishing attempts are crucial. Focus on common red flags such as suspicious sender addresses, urgent language, and unexpected attachments.
- Email Filtering and Authentication: Implement robust email security gateways that include spam filters, anti-phishing capabilities, and email authentication protocols like DMARC, SPF, and DKIM.
- Endpoint Protection: Deploy advanced endpoint detection and response (EDR) solutions that can detect and prevent the execution of malicious payloads, even if they bypass initial email filters.
- Patch Management: Keep all software and operating systems updated to patch known vulnerabilities that attackers frequently exploit. For example, staying current with patches can prevent exploitation of vulnerabilities like CVE-2023-23397 (Outlook Elevation of Privilege) that could be leveraged by sophisticated phishing campaigns.
- Incident Response Plan: Develop and regularly test a comprehensive incident response plan specifically for phishing attacks, outlining steps for detection, containment, eradication, and recovery.
Conclusion
The landscape of cyber threats is dynamic, with phishing attacks consistently evolving to circumvent enterprise defenses. Equipping cybersecurity analysts with advanced sandbox tools is not merely a convenience but a necessity. The solutions discussed provide various capabilities, from interactive control to genetic analysis and agentless monitoring, each offering a distinct advantage in dissecting complex and evasive phishing threats. By integrating these powerful sandboxes into their analytical workflows and combining them with robust preventative measures, organizations can significantly enhance their ability to detect, analyze, and neutralize phishing campaigns, ultimately safeguarding their assets and data in 2026 and beyond.





