Assessing the Role of AI in Zero Trust
The Unseen Guardian: How AI is Forging the Future of Zero Trust
By 2025, Zero Trust has evolved from a conceptual framework into an essential pillar of modern security. No longer merely theoretical, it’s now a requirement that organizations must adopt. A robust, defensible architecture built on Zero Trust principles does more than satisfy baseline regulatory mandates. It underpins cyber resilience, secures third-party partnerships, and ensures uninterrupted business operations.
The inherent complexity of implementing and maintaining a true Zero Trust paradigm often presents significant hurdles. This is where Artificial Intelligence (AI) emerges as a transformative force, providing the agility, analytical power, and automation necessary to move beyond traditional perimeter defenses. AI’s capabilities are not just enhancing Zero Trust; they are redefining its very scalability and effectiveness.
Zero Trust: The Non-Negotiable Imperative
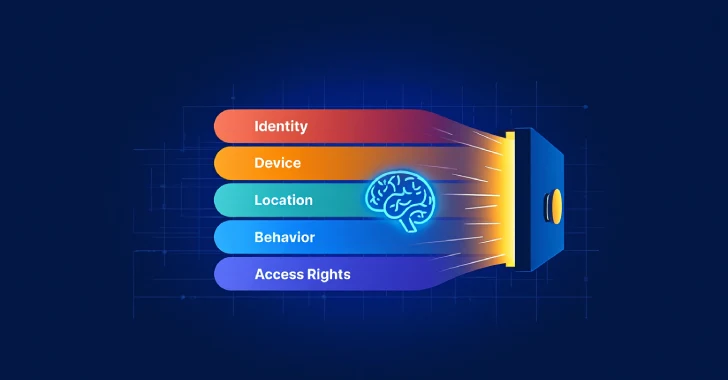
The “never trust, always verify” ethos of Zero Trust is fundamentally reshaping how enterprises approach security. It mandates strict identity verification for every user and device attempting to access resources, regardless of their location on or off the network. This micro-segmentation strategy moves away from the implicit trust granted to devices once inside the network, acknowledging that threats can originate from anywhere, including internal sources.
Without Zero Trust, organizations remain vulnerable to sophisticated attacks like ransomware, insider threats, and supply chain compromises. For example, a successful phishing attempt leveraging a zero-day vulnerability (e.g., CVE-2024-XXXXX) could grant an attacker initial access. In a perimeter-based model, this could lead to widespread lateral movement. With Zero Trust, granular policies and continuous verification significantly limit the blast radius.
AI’s Catalytic Role in Zero Trust Evolution
The integration of AI into Zero Trust frameworks addresses several critical challenges:
- Adaptive Access Control: AI analyzes user behavior, device posture, and environmental factors in real-time to make dynamic access decisions. This moves beyond static rules, identifying anomalous behavior that could indicate a compromise.
- Threat Detection and Response: Machine learning algorithms can process vast amounts of telemetry data – network traffic, endpoint logs, identity data – to detect subtle indicators of compromise that human analysts might miss. It’s about spotting patterns that deviate from established baselines and flagging them instantly.
- Automated Policy Enforcement: AI can automate the creation, refinement, and enforcement of Zero Trust policies. As environments change, such as the introduction of new applications or users, AI can suggest or even automatically implement policy adjustments, reducing manual overhead and potential for misconfiguration.
- Reduced Alert Fatigue: By correlating disparate data points and prioritizing true threats, AI minimizes false positives, allowing security teams to focus on legitimate incidents and improving operational efficiency.
AI-Powered Components of Advanced Zero Trust Architectures
Modern Zero Trust implementations heavily leverage AI across several key components:
- Identity and Access Management (IAM) with Behavioral Analytics: AI scrutinizes login patterns, access times, geo-location, and resource requests to build a ‘normal’ profile for each user. Deviations trigger step-up authentication or denial of access.
- Network Micro-segmentation and Policy Orchestration: AI can analyze network flows to recommend optimal micro-segmentation boundaries and automatically generate the necessary firewall rules or network access control policies.
- Endpoint Detection and Response (EDR) with Machine Learning: AI-powered EDR solutions continuously monitor endpoint activity, identifying malware, exploits, and lateral movement attempts. This extends Zero Trust principles directly to the device level, verifying their integrity.
- Security Information and Event Management (SIEM) with AI/ML: Integrating AI into SIEM platforms dramatically enhances their ability to ingest, parse, and analyze security logs from across the enterprise, enabling real-time threat correlation and actionable intelligence.
Remediation Actions: Leveraging AI for Zero Trust Resilience
Building an AI-driven Zero Trust architecture requires a strategic approach. Here are actionable steps:
- Inventory and Classify All Resources: Before implementing Zero Trust, accurately identify and tag all assets, applications, services, and data. AI can assist in this discovery phase by analyzing network traffic and usage patterns.
- Establish Robust Identity Governance: Implement strong multi-factor authentication (MFA) everywhere. Leverage AI-driven adaptive authentication for continuous verification based on context.
- Implement Least Privilege Access: Define access policies based on the principle of least privilege, ensuring users and devices only have access to what they absolutely need. AI can help identify and enforce optimal privilege sets.
- Monitor and Analyze Continuously: Deploy AI-powered EDR, SIEM, and network traffic analysis (NTA) tools. These systems provide the continuous visibility required for Zero Trust and allow AI to detect anomalies.
- Automate Orchestration and Response: Integrate Security Orchestration, Automation, and Response (SOAR) platforms with your AI tools to automate incident response workflows and policy adjustments. For instance, if an AI detects a compromised device (e.g., related to CVE-2023-XXXXX activity), the SOAR platform can instantly isolate it and revoke access.
- Regularly Test and Refine Policies: Zero Trust policies are not static. Use AI to analyze vast datasets for policy optimization and risk reduction. Conduct regular penetration testing and red teaming to validate the effectiveness of your AI-driven Zero Trust controls.
Conclusion: The Future is Verified, Dynamically
The symbiotic relationship between AI and Zero Trust is not a futuristic concept; it is the present reality of advanced cybersecurity. For organizations navigating an increasingly complex threat landscape, embracing this synergy is paramount. AI provides the essential intelligence and automation to operationalize Zero Trust at scale, enabling adaptive access, proactive threat detection, and resilient business continuity. The security posture of enterprises in 2025 and beyond will be defined by their ability to harness AI as the unseen guardian, continuously verifying every interaction and solidifying the ‘never trust, always verify’ foundation.





