Hackers Use Facebook Ads to Spread JSCEAL Malware via Fake Cryptocurrency Trading Apps
In the rapidly evolving landscape of digital finance, the allure of quick returns on cryptocurrency investments presents a fertile ground for malicious actors. A new, concerning campaign has emerged, leveraging sophisticated social engineering tactics and cutting-edge malware to compromise unsuspecting users. Cybersecurity researchers are raising alarms about an active threat distributing fake cryptocurrency trading applications, ultimately deploying a potent form of malware known as JSCEAL.
This attack vector highlights the persistent danger of seemingly legitimate online advertisements and the critical need for vigilance in the digital realm. Understanding the mechanics of this campaign is paramount for IT professionals, security analysts, and anyone involved in protecting digital assets.
The Deceptive Lure: Facebook Ads and Counterfeit Sites
The latest wave of malicious activity hinges on a classic social engineering trick: impersonation and baiting. Thousands of malicious advertisements are being propagated across Facebook, a platform with a vast global reach. These ads are meticulously crafted to appear legitimate, often promising lucrative cryptocurrency trading opportunities or promoting seemingly official trading platforms.
Once a user clicks on one of these deceptive ads, they are not redirected to a genuine investment platform. Instead, they land on counterfeit websites designed to mimic legitimate cryptocurrency exchanges or trading applications. These fake sites are crucial to the attack chain, serving as the initial point of compromise and building a false sense of security for the victim.
JSCEAL Malware: A Potent Data Thief
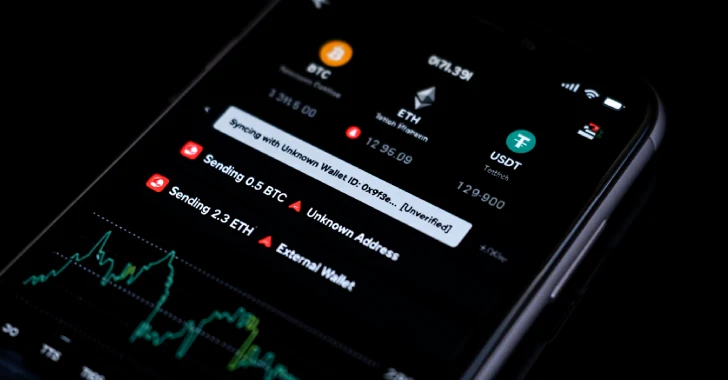
The ultimate goal of this campaign is the deployment of JSCEAL malware. JSCEAL is not a typical executable; it’s a compiled V8 JavaScript (JSC) malware. This technical detail is significant as it allows the malware to operate within environments where traditional executables might be flagged or blocked more easily. Its JavaScript nature also offers a degree of cross-platform potential, though the current campaign appears focused on specific user environments.
Once deployed, JSCEAL is highly capable of capturing sensitive personal and financial data. Its primary objectives include:
- Credential Harvesting: Stealing usernames, passwords, and other authentication details from various online accounts, including banking, email, and other cryptocurrency platforms.
- Wallet Data Exfiltration: Accessing and exfiltrating private keys, seed phrases, and other critical information stored in cryptocurrency wallets, directly leading to the theft of digital assets.
The stealthy nature of a compiled JavaScript malware makes its detection challenging, making user awareness and proactive security measures even more critical.
Attack Chain Deep Dive
The attack chain is a multi-step process, each designed to progress the compromise:
- Initial Lure (Facebook Ads): Malicious actors create and disseminate thousands of alluring but fake cryptocurrency-related advertisements on Facebook. These ads exploit user interest in crypto investments.
- Redirection to Counterfeit Sites: Clicking on the malicious ad diverts the victim to sophisticated fake cryptocurrency trading websites. These sites are often visually convincing and designed to elicit trust.
- Fake App Download Prompts: The counterfeit websites instruct users to download what appears to be a legitimate cryptocurrency trading application. This “app” is, in reality, the dropper for the JSCEAL malware.
- JSCEAL Deployment: Upon execution of the downloaded “app,” the compiled V8 JavaScript engine within initiates the deployment of JSCEAL onto the victim’s system.
- Data Exfiltration: Once active, JSCEAL begins its malicious activities, scanning for and exfiltrating sensitive data, particularly credentials and cryptocurrency wallet information, back to the attackers’ command and control (C2) servers.
This carefully orchestrated sequence leverages human curiosity and the desire for financial gain against the victim, making it a highly effective social engineering campaign.
Remediation Actions and Prevention Strategies
Defending against sophisticated campaigns like the JSCEAL distribution requires a multi-layered approach focusing on user education, technical controls, and proactive monitoring.
- Enhanced User Education:
- Scrutinize Advertisements: Always be skeptical of ads, especially those promising high returns or requiring immediate action. Verify the legitimacy of the advertiser and the destination URL before clicking.
- Official Sources Only: Download cryptocurrency trading applications ONLY from official, verified app stores (Google Play, Apple App Store) or directly from the legitimate company’s official website, accessed via direct typing of the URL or secure bookmarks. Never rely on links from ads or unsolicited emails.
- Recognize Phishing/Spoofing: Train users to identify signs of spoofed websites, such as subtle URL misspellings, poor grammar, unusual branding, or requests for excessive permissions.
- Technical Controls:
- Robust Antivirus/Endpoint Detection & Response (EDR): Implement and maintain up-to-date antivirus and EDR solutions across all endpoints. These tools can help detect and block known malware signatures and suspicious behaviors.
- Web Filtering and DNS Security: Deploy web filtering solutions and DNS security services to block access to known malicious domains and counterfeit websites.
- Browser Security Extensions: Encourage or enforce the use of browser security extensions that warn users about phishing sites or potentially malicious downloads.
- Email Security Gateways: While this campaign primarily uses Facebook ads, robust email security gateways are still essential for general threat prevention, filtering out malicious links and attachments.
- Principle of Least Privilege: Limit user permissions to prevent widespread damage if an account is compromised.
- Proactive Security Measures:
- Multi-Factor Authentication (MFA): Implement MFA on all critical accounts, especially for cryptocurrency exchanges, email, and financial services. This adds a crucial layer of security, even if credentials are stolen.
- Regular Backups: Maintain regular, secure backups of critical data, isolated from the network, to aid in recovery in case of a successful attack.
- Security Awareness Training: Conduct regular, engaging security awareness training for all employees, emphasizing the latest social engineering tactics and safe online behaviors.
- Threat Intelligence Feeds: Subscribe to and integrate threat intelligence feeds to stay updated on emerging threats, TTPs (Tactics, Techniques, and Procedures), and indicators of compromise (IoCs) related to campaigns like JSCEAL.
Tools for Detection and Mitigation
The following tools can assist in detecting, preventing, and mitigating the risks associated with malware campaigns like JSCEAL:
| Tool Name | Purpose | Link |
|---|---|---|
| Endpoint Detection & Response (EDR) Solutions | Behavioral analysis, threat detection, and incident response at the endpoint level. Examples include CrowdStrike Falcon, SentinelOne, Microsoft Defender for Endpoint. | (Vendor specific links) |
| Web Application Firewall (WAF) | Protects web applications from various attacks, including those involving malicious redirects and potentially blocking access to known malicious sites. | (Vendor specific links) |
| DNS Filtering Services | Blocks access to malicious domains at the DNS level, preventing users from reaching phishing or malware distribution sites. Examples include Cisco Umbrella, Cloudflare DNS. | Cisco Umbrella |
| Threat Intelligence Platforms (TIPs) | Aggregates and analyzes threat data, providing indicators of compromise (IoCs) and context for emerging threats. Examples include MISP, Recorded Future. | MISP |
| Security Awareness Training Platforms | Educates users about phishing, social engineering, and safe online practices. Examples include KnowBe4, SANS Security Awareness. | KnowBe4 |
Conclusion: Stay Vigilant, Stay Secure
The proliferation of JSCEAL malware via deceptive Facebook advertisements and fake cryptocurrency trading apps underscores the sophistication of modern cyber threats. Attackers are constantly evolving their methods, blending technical prowess with cunning social engineering to exploit human trust and digital enthusiasm. For organizations and individuals alike, the lesson is clear: a proactive, informed, and defense-in-depth approach is no longer optional but essential.
Verifying sources, scrutinizing online advertisements, and empowering users with critical security awareness are fundamental safeguards against these insidious campaigns. By understanding the mechanisms behind attacks like JSCEAL, we can collectively build a more resilient and secure digital environment, protecting valuable credentials and cryptocurrency assets from the reach of malicious actors.





