New ‘Win-DoS’ Zero-Click Vulnerabilities Turns Windows Server/Endpoint, Domain Controllers Into DDoS Botnet
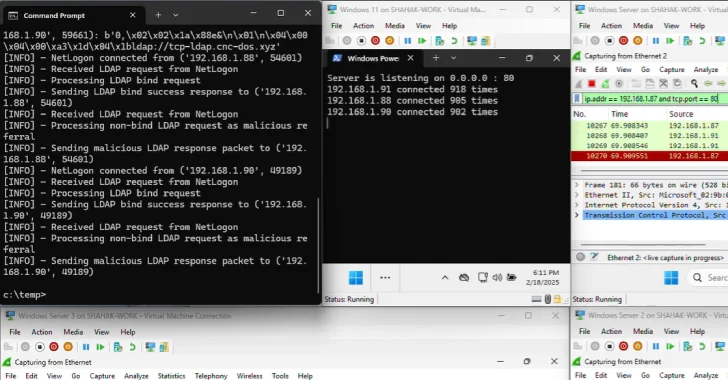
A disturbing new threat has emerged from the DEF CON 33 security conference, casting a long shadow over Windows environments globally. Researchers Yair and Shahak Morag of SafeBreach Labs have unveiled a new class of denial-of-service (DoS) attacks, ominously dubbed the “Win-DoS Epidemic.” This groundbreaking research details four novel Windows DoS vulnerabilities and, most critically, a zero-click distributed denial-of-service (DDoS) flaw. This means that merely having a vulnerable system connected to a network could transform it into a potent weapon in a DDoS botnet, without any user interaction required. The implications for Windows servers, endpoints, and especially domain controllers are severe, demanding immediate attention from IT professionals and security analysts.
The Win-DoS Epidemic: A New Frontier in DDoS
The concept of DoS attacks is not new, but the “Win-DoS Epidemic” introduces a terrifying evolution. Traditional DoS often relies on overwhelming a target with traffic. These new vulnerabilities exploit weaknesses within Windows itself, turning legitimate system functions into attack vectors. Imagine your critical Windows Server or Domain Controller, the very heart of your network, inadvertently participating in a crippling DDoS attack against another entity, or even against its own infrastructure.
The research revealed four distinct DoS vulnerabilities, culminating in one particularly insidious zero-click DDoS flaw. While specific CVE numbers are anticipated to be published following the DEF CON presentation, the zero-click nature of this particular vulnerability is what makes it a game-changer. It eliminates the need for social engineering, malicious links, or compromised files – the hallmarks of many modern attacks. Instead, the mere presence of an unpatched system on a network could be enough for it to become a weaponized node.
Understanding Zero-Click Vulnerabilities
Zero-click vulnerabilities represent the pinnacle of stealth and efficacy from an attacker’s perspective. These flaws allow an attacker to compromise a device or initiate harmful actions without requiring any interaction from the victim. Contrast this with typical phishing attacks, which rely on a user clicking a link or opening an attachment. In the context of the discovered Win-DoS flaws, this means:
- No User Interaction: Victims do not need to open a malicious email, visit a compromised website, or click a suspicious link.
- Remote Exploitation: Exploitation can often occur remotely, across networks, without direct physical access to the affected machine.
- Rapid Proliferation: The lack of user interaction greatly accelerates an attacker’s ability to compromise numerous systems and build a large botnet quickly.
This dramatically lowers the bar for attackers, making mass exploitation a far more achievable goal. Domain controllers, being central to network operations and identity management, present an especially lucrative target due to their constant network presence and critical role.
Impact on Windows Server, Endpoints, and Domain Controllers
The ramifications of these Win-DoS vulnerabilities are profound, affecting the entire spectrum of Windows environments:
- Windows Servers: Critical applications, databases, and services running on Windows Servers could be disrupted, leading to downtime, data inaccessibility, and significant operational losses. A server turned DDoS bot could also exhaust its own resources, rendering it useless for legitimate operations.
- Windows Endpoints: While individual workstations might have less direct impact on a large-scale DDoS attack than a server, a compromised endpoint still contributes to the botnet’s aggregate power. Furthermore, an exploited endpoint could be a stepping stone for further internal network compromise.
- Domain Controllers: This is arguably the most critical target. Domain Controllers are the backbone of Active Directory, managing user authentication, permissions, and network resources. If a Domain Controller becomes a DDoS bot, it faces not only resource exhaustion but also potential service disruption for the entire domain, leading to widespread authentication failures and network paralysis. Their constant uptime requirement makes them prime targets for botnet conscription.
Such attacks can result in significant financial losses due to service disruption, reputational damage, and the costs associated with incident response and recovery. A DDoS botnet composed of internal systems also complicates network forensics and incident response, as the source of the attack appears to originate from within a trusted environment.
Remediation Actions
While specific patches for these newly disclosed vulnerabilities are still pending and will likely be released by Microsoft, proactive measures are paramount. As a cybersecurity professional, immediate actions should focus on reducing your attack surface and improving your resilience:
- Stay Informed: Closely monitor official advisories from Microsoft and reputable cybersecurity news outlets (like the source of this article) for the release of patch information, specific CVEs, and detailed mitigation strategies. Expect CVE numbers to be assigned soon after public disclosure.
- Patch Management: Implement a robust and accelerated patch management program. Ensure all Windows operating systems (servers and endpoints) are kept up-to-date with the latest security updates. Prioritize updates for Domain Controllers.
- Network Segmentation: Isolate critical assets like Domain Controllers and sensitive servers from less trusted network segments. This limits the lateral movement of an attacker, even if an initial compromise occurs.
- Security Baselines: Enforce strong security configurations and baselines on all Windows systems, disabling unnecessary services, ports, and protocols.
- Traffic Monitoring: Deploy network intrusion detection/prevention systems (IDS/IPS) and actively monitor network traffic for anomalous patterns indicative of DDoS activity or command-and-control (C2) communications from potential botnet participation.
- DDoS Mitigation Services: Consider external DDoS mitigation services for critical internet-facing assets. While these vulnerabilities leverage internal system weaknesses, external services can help absorb large-scale attacks.
- Endpoint Detection and Response (EDR)/Extended Detection and Response (XDR): Leverage EDR/XDR solutions to gain deeper visibility into endpoint activity, detect unusual process behavior, and identify potential exploitation attempts.
Tools for Detection and Mitigation
Several categories of tools are essential for detecting, analyzing, and mitigating the risks posed by vulnerabilities like the Win-DoS Epidemic:
| Tool Name | Purpose | Link |
|---|---|---|
| Microsoft Defender for Endpoint | Advanced EDR for threat detection, investigation, and response. | https://www.microsoft.com/en-us/security/business/threat-protection/microsoft-defender-for-endpoint |
| Wireshark | Network protocol analyzer for deep packet inspection and anomaly detection. | https://www.wireshark.org/ |
| Snort / Suricata | Open-source IDS/IPS for real-time traffic analysis and signature-based threat detection. | https://www.snort.org/
https://suricata.io/ |
| Nessus / OpenVAS | Vulnerability scanners to identify unpatched systems and misconfigurations. | https://www.tenable.com/products/nessus
http://www.openvas.org/ |
| NetFlow/IPFIX Collectors | Collect, analyze, and visualize network flow data for traffic monitoring and anomaly detection. | Various commercial/open-source solutions (e.g., SolarWinds NetFlow Traffic Analyzer, ELK Stack with Flow-based data) |
Conclusion
The “Win-DoS Epidemic” revelations from DEF CON 33 serve as a stark reminder of the persistent and evolving nature of cybersecurity threats. The emergence of zero-click DDoS vulnerabilities targeting core Windows infrastructure like Domain Controllers represents a significant escalation in the threat landscape. Proactive patch management, robust network segmentation, continuous monitoring, and the strategic deployment of security tools are no longer merely best practices—they are indispensable defense mechanisms. Organizations must prioritize understanding and mitigating these new threats to safeguard their critical assets and maintain operational integrity in an increasingly hostile digital environment.





