New Elastic EDR 0-Day Vulnerability Allows Attackers to Bypass Detection, Execute Malware, and Cause BSOD
A disturbing new zero-day vulnerability in Elastic EDR’s core components has surfaced, posing a significant threat to organizational security postures. This critical flaw allows attackers to bypass detection mechanisms, execute arbitrary malware, and even induce a Blue Screen of Death (BSOD), effectively turning a key defensive tool against its users. For security teams relying on Elastic EDR, understanding the implications and immediate actions required is paramount.
The Elastic EDR 0-Day Vulnerability: A Deep Dive
As reported by Ashes Cybersecurity, this newly identified vulnerability lies within a fundamental part of Elastic’s Endpoint Detection and Response solution. EDR systems are designed to be the eyes and ears on endpoints, offering deep visibility into potential threats and preventing malicious activity. The discovery that a flaw in such a system can be exploited to facilitate attacks, rather than prevent them, highlights a severe security gap.
The core issue stems from how the EDR solution processes certain operations, allowing an attacker to manipulate its behavior. This manipulation enables three critical outcomes for an adversary:
- Bypass Detection: Malicious activities, even those typically flagged by EDR, can proceed unnoticed. This creates a stealthy pathway for attackers to establish persistence or exfiltrate data without triggering alerts.
- Execute Malware: With detection mechanisms circumvented, attackers can execute arbitrary code on the endpoint. This means ransomware, spyware, or other destructive payloads can be deployed and run with elevated privileges.
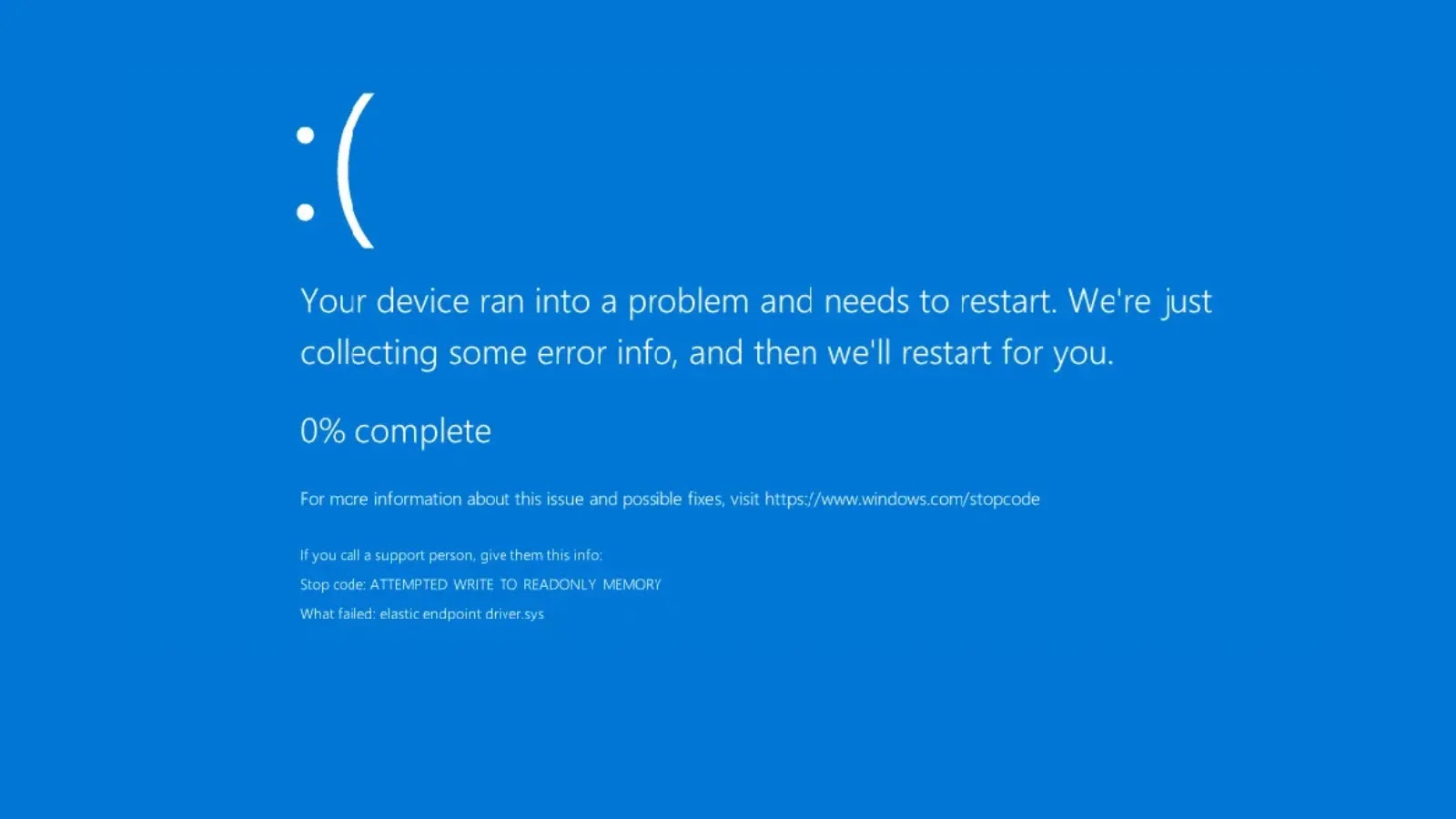
- Cause BSOD: Beyond just malware execution, the vulnerability can be leveraged to trigger a system crash (Blue Screen of Death). While a BSOD might seem less severe than data theft, it indicates a critical system instability that can lead to denial of service, data corruption, and significant operational disruption. It also suggests a low-level control over the system, paving the way for more sophisticated attacks.
This vulnerability underscores the critical importance of continuous security research and prompt patching. When a security tool itself becomes an attack vector, the implications are far-reaching, potentially compromising an organization’s entire security framework.
Impact and Severity
The severity of this 0-day vulnerability cannot be overstated. An EDR solution is often the last line of defense at the endpoint level, and its compromise fundamentally weakens an organization’s security posture. The ability for attackers to bypass detection, execute malware, and cause system instability means:
- Increased Risk of Data Breaches: Unchecked malware execution significantly elevates the risk of sensitive data exfiltration or destruction.
- Operational Disruption: BSODs and system instability can lead to costly downtime and damage to business continuity.
- Loss of Trust: A compromise within a security tool erodes confidence in the very systems designed to protect assets.
- Espionage and Sabotage: In advanced persistent threat (APT) scenarios, this vulnerability could be exploited for long-term infiltration, intellectual property theft, or critical infrastructure disruption.
While a specific CVE number for this newly discovered 0-day has not been publicly assigned at the time of this writing, its operational impact is demonstrably critical. Security teams should monitor official channels, including the CVE database, for its eventual publication and associated details.
Remediation Actions and Mitigations
Given the nature of a 0-day vulnerability, immediate and proactive measures are essential. Organizations utilizing Elastic EDR must prioritize the following steps:
- Monitor Vendor Advisories: Continuously check Elastic’s official security advisories and update channels for patches or workarounds. As a 0-day, a patch is the ultimate solution.
- Isolate Susceptible Systems: If patches are not immediately available, consider isolating or segmenting critical systems where Elastic EDR is deployed, especially those with high-value data or critical operations.
- Implement Defense-in-Depth: While EDR is crucial, it’s never the sole defense. Ensure other security layers are robust:
- Network Segmentation: Limit lateral movement within the network, even if an endpoint is compromised.
- Least Privilege Principle: Ensure users and applications operate with the minimum necessary permissions.
- Regular Backups: Maintain comprehensive and tested backups to facilitate recovery from ransomware or data corruption.
- Endpoint Hardening: Implement strict security configurations on all endpoints, independent of EDR.
- Enhanced Anomaly Detection: While the EDR’s detection might be bypassed, other monitoring tools might still catch anomalous behavior. Focus on unusual network traffic, process executions, or user activity patterns.
- Incident Response Plan Activation: Review and potentially activate elements of your incident response plan. Prepare for potential compromises, even if no active exploitation is detected yet.
- Security Awareness Training: Reinforce user awareness about phishing and social engineering, as these are common initial access vectors that could precede the exploitation of such a vulnerability.
Relevant Tools for Analysis and Mitigation
While direct mitigation for a 0-day often relies on vendor patches, several tools can aid in detection of post-exploitation activity, general endpoint hardening, and network monitoring.
| Tool Name | Purpose | Link |
|---|---|---|
| Sysinternals Suite (Process Monitor, Autoruns) | Detailed process monitoring, auto-start program analysis to detect persistence. | https://learn.microsoft.com/en-us/sysinternals/ |
| Wireshark | Network protocol analyzer for detecting anomalous outbound connections or C2 traffic. | https://www.wireshark.org/ |
| Elastic Security (SIEM component) | Centralized log management and security information and event management; can correlate data from other sources to detect suspicious activity bypassing EDR. | https://www.elastic.co/security/ |
| Nessus / OpenVAS | Vulnerability scanning for general system weaknesses that attackers might chain with an EDR bypass. | https://www.tenable.com/products/nessus https://www.greenbone.net/en/community-edition/ |
| Firewalls (Next-Gen) | Network-level anomaly detection, intrusion prevention, and access control. | (Vendor Specific; e.g., Palo Alto Networks, Fortinet) |
Conclusion
The discovery of a 0-day vulnerability in Elastic EDR that allows bypass of detection, malware execution, and BSOD attacks is a serious development for cybersecurity professionals. It highlights the inherent risks even in defensive tools and the dynamic nature of the threat landscape. While waiting for an official patch from Elastic, organizations must implement robust defense-in-depth strategies, enhance their monitoring capabilities, and remain vigilant against potential exploitation. Prompt action and continuous awareness are critical to mitigating the risks posed by such high-impact flaws.





