New MITM6 + NTLM Relay Attack Let Attackers Escalate Privileges and Compromise Entire Domain
Unmasking the MITM6 + NTLM Relay Attack: A Path to Domain Admin in Minutes
The digital landscape is a constant battleground, and threat actors relentlessly innovate to bypass defenses. A sophisticated new attack chain, dubbed MITM6 + NTLM Relay, has emerged, demonstrating an alarming efficiency in escalating privileges and compromising entire Active Directory domains. This isn’t a complex, multi-day operation; it’s a rapid assault that can achieve Domain Admin privileges in mere minutes once an attacker gains initial network access.
Understanding this attack is critical for any organization relying on Windows-based infrastructure. It exposes a dangerous confluence of default Windows configurations and Active Directory behaviors that, when exploited, create a direct path to full domain compromise.
The Anatomy of the Attack: MITM6 and NTLM Relay Explained
This potent attack leverages two primary techniques in concert:
- MITM6 (Man-in-the-Middle for IPv6): This initial phase exploits a fundamental aspect of Windows’ network configuration: its default tendency to prefer IPv6 over IPv4, even when an IPv6 network isn’t explicitly configured. An attacker can broadcast a rogue IPv6 router advertisement, effectively making themselves the default IPv6 router for vulnerable Windows machines. This allows them to intercept and manipulate IPv6 traffic.
- NTLM Relay: Once the attacker’s machine is acting as a man-in-the-middle, they can intercept NTLM authentication requests (often generated by legitimate system services or user actions) directed at domain controllers or other network resources. Instead of forwarding these requests directly, the attacker “relays” them to a target server (e.g., a domain controller) while substituting their own credentials with those of the intercepted victim. If successful, the attacker can authenticate as the victim without ever knowing their password hash.
The Path to Domain Dominance: How It Unfolds
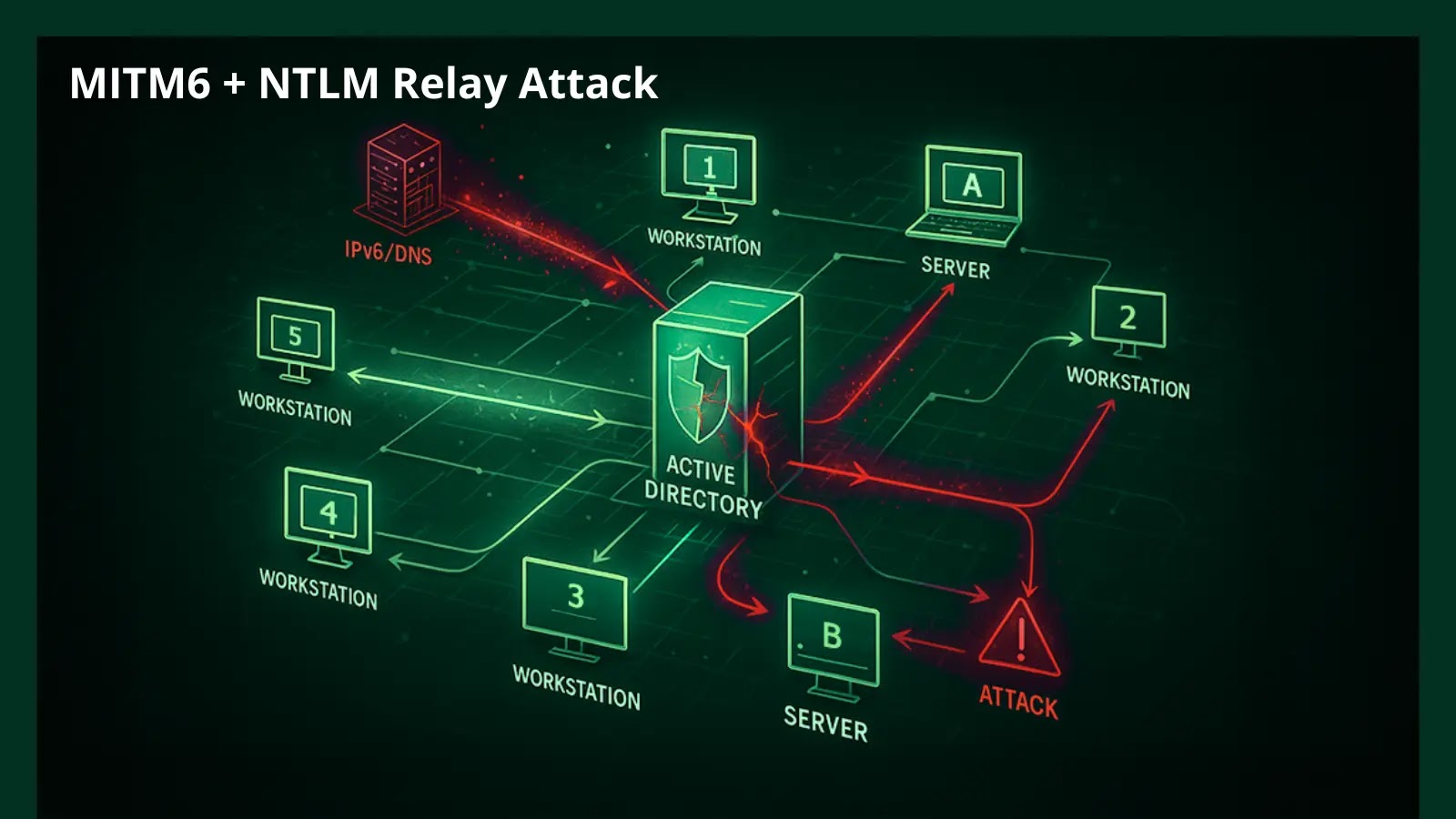
The MITM6 + NTLM Relay attack chain unfolds with chilling efficiency:
- Initial Network Access: The attacker gains a foothold within the target network (e.g., via a compromised workstation, Wi-Fi breach, or insider threat).
- Rogue IPv6 Router Advertisement: Using tools like mitm6, the attacker broadcasts a deceptive IPv6 router advertisement. Windows machines, by default, will auto-configure an IPv6 address and prefer this rogue router, effectively diverting their IPv6 traffic through the attacker’s machine.
- NTLM Authentication Interception: As Windows machines attempt to authenticate with domain resources (e.g., SMB shares, LDAP, etc.), their NTLM authentication requests are routed through the attacker’s system.
- NTLM Relay to Domain Controller: The attacker intercepts these NTLM requests. They then use tools like ntlmrelayx.py (part of the Impacket toolkit) to relay these intercepted NTLM authentications to the domain controller.
- Machine Account Creation & Escalation: A critical aspect of this attack is abusing Active Directory’s default setting that allows any authenticated user (even a relayed machine account) to create up to 10 new machine accounts in the domain. The attacker relays the NTLM authentication of a legitimate machine account to the domain controller and uses this relayed authentication to create a new, controlled machine account.
- Kerberos Delegation Abuse (RBCD): With control over a newly created machine account, the attacker can then configure Resource-Based Constrained Delegation (RBCD) for this new account, allowing it to impersonate arbitrary users (including Domain Admins) on specific services running on the domain controller. This is often the final step to attaining full Domain Admin privileges.
Key Takeaways for Security Professionals
This attack highlights several critical vulnerabilities and misconfigurations:
- The pervasive nature of default Windows IPv6 auto-configuration.
- Active Directory’s generous default an “authenticated user” quota for machine account creation.
- The inherent risks associated with NTLM authentication, especially when not properly secured.
Remediation Actions: Fortifying Your Active Directory
Mitigating the MITM6 + NTLM Relay attack requires a multi-layered approach, addressing both technical configurations and security best practices:
- Disable IPv6 Where Not Required: While IPv6 is the future, if it’s not actively used or managed in your environment, disable it on all endpoints and servers. This is the most direct way to prevent the MITM6 component.
- Block Rogue Router Advertisements: Implement 네트워크 access control lists (ACLs) or enterprise-grade network intrusion prevention systems (NIPS) to detect and block unsolicited IPv6 router advertisements.
- Disable NTLM Where Possible: Prioritize Kerberos authentication and disable NTLM authentication on domain controllers and sensitive servers where feasible. This is a broader, long-term security goal.
- Restrict Machine Account Creation: Modify the default Active Directory permissions to restrict which users or groups can create computer objects. Reduce the
ms-DS-MachineAccountQuotaattribute from its default of 10. Implement this with caution and thorough testing, as it can impact legitimate machine provisioning. More details on CVEs related to machine account abuse for RBCD can be found, for example, on CVE-2021-42278 and CVE-2021-42287, although the NTLM relay aspect is distinct. - Implement EDR/MDR Solutions: Endpoint Detection and Response (EDR) and Managed Detection and Response (MDR) solutions can help detect suspicious network traffic patterns, NTLM relay attempts, and anomalous Kerberos ticket requests characteristic of this attack.
- Monitor Active Directory Logs: Regularly audit Active Directory for new computer account creations, suspicious authentication attempts, and changes to delegation settings.
- Network Segmentation: Segment your network to limit the blast radius of a compromised machine and restrict the ability of attackers to broadcast rogue router advertisements across critical network segments.
Tools for Detection and Mitigation
Several tools are instrumental in understanding, detecting, and mitigating this class of attacks:
| Tool Name | Purpose | Link |
|---|---|---|
| mitm6 | Simulates the rogue IPv6 router advertisement for testing. | https://github.com/fox-it/mitm6 |
| ntlmrelayx.py (Impacket) | Facilitates NTLM relay attacks for testing and understanding. | https://github.com/SecureAuthCorp/impacket/blob/master/examples/ntlmrelayx.py |
| BloodHound | Maps Active Directory attack paths, including delegation abuses. | https://bloodhoundenterprise.io/ |
| Sysmon | Advanced system monitoring for Windows, useful for detecting suspicious process execution and network activity related to such attacks. | https://learn.microsoft.com/en-us/sysinternals/downloads/sysmon |
Conclusion: Proactive Defense is Paramount
The MITM6 + NTLM Relay attack is a potent reminder that seemingly innocuous default configurations, when chained together, can lead to severe security breaches. It underscores the critical need for organizations to move beyond basic perimeter defenses and adopt a proactive, in-depth defense strategy. Regularly reviewing Active Directory configurations, understanding network protocols, and implementing robust monitoring and response capabilities are no longer optional; they are essential for safeguarding your most critical assets.