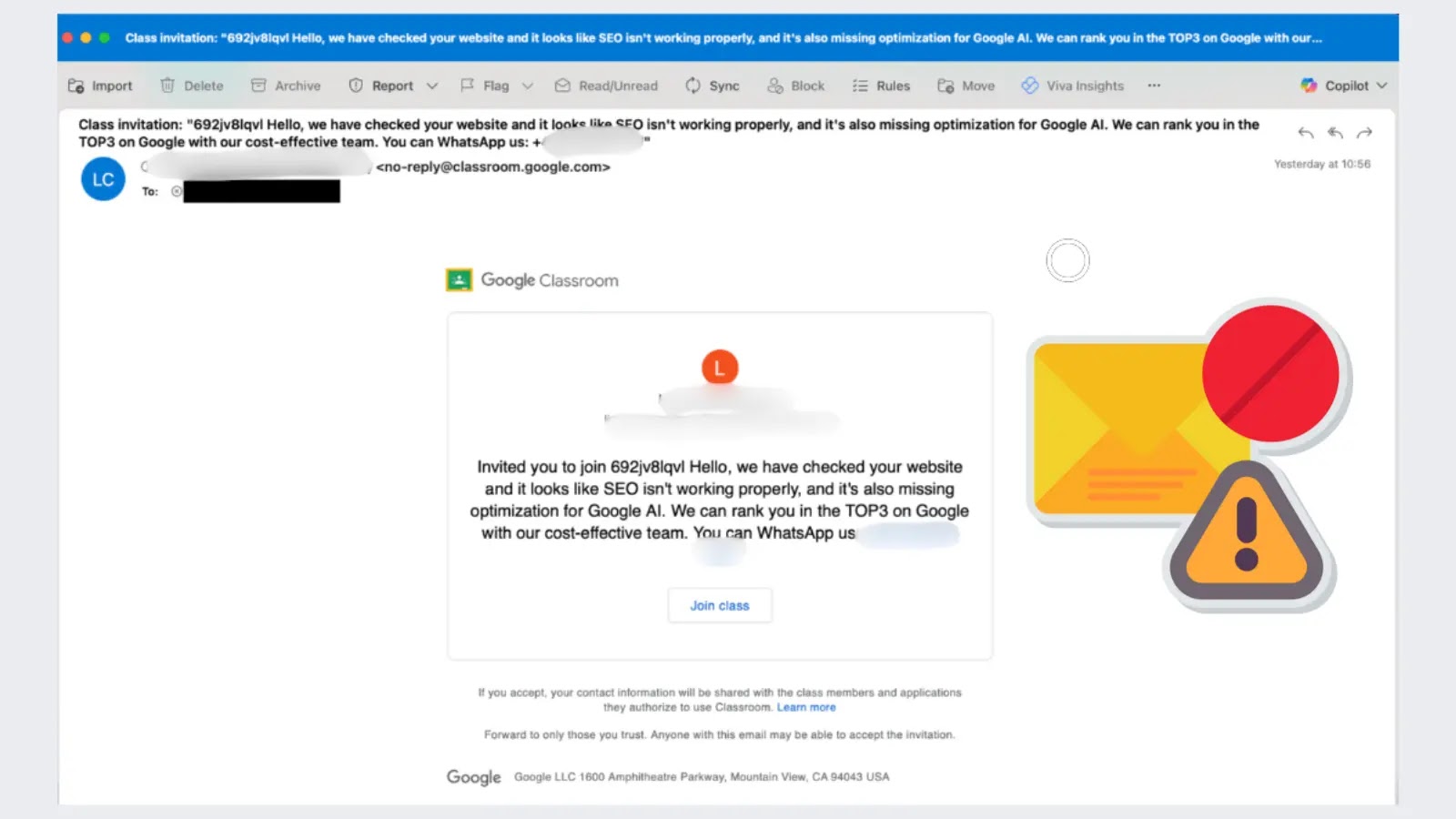
Hackers Leverage Google Classroom for 115,000+ Phishing Emails Targeting 13,500+ Organizations
The digital threat landscape is perpetually shifting, with threat actors continuously innovating their tactics to circumvent established security measures. A recent, deeply concerning development underscores this evolution: hackers have weaponized a platform trusted by millions worldwide – Google Classroom – to unleash a massive phishing campaign. This isn’t merely an isolated incident; it signifies a dangerous sidestepping of traditional email security filters by exploiting the inherent trust in legitimate services. Understanding the mechanics and implications of this attack is paramount for any organization serious about its cybersecurity posture.
The Anatomy of the Attack: Google Classroom Abused
In a sophisticated operation uncovered by Check Point, threat actors leveraged Google Classroom to distribute over 115,000 malicious phishing emails. This large-scale campaign targeted more than 13,500 organizations globally, indicating a broad, indiscriminate approach designed for maximum reach. The sheer volume and target breadth highlight the significant risk posed when legitimate services are co-opted for nefarious purposes.
The campaign unfolded in five distinct waves between August 6 and August 12, 2025. This coordinated, multi-stage delivery allowed the attackers to maximize their impact and potentially adapt their tactics based on initial responses. The core innovation lay in disguising phishing attempts as legitimate notifications from Google Classroom, exploiting the platform’s trusted domain and email delivery mechanisms. This tactic allowed the malicious emails to bypass security solutions that might typically flag suspicious senders or content, as the source was, technically, Google itself.
Why Google Classroom? The Trust Exploitation Vector
The choice of Google Classroom as an attack vector is no accident. Educational platforms, like Google Workspace for Education, are inherently trusted environments. Users, particularly students, teachers, and administrators, are accustomed to receiving notifications, assignments, and updates directly from these platforms. This ingrained trust is precisely what the attackers exploited.
- Bypass Security Filters: Emails originating from Google’s legitimate domains (e.g., classroom.google.com) are generally whitelisted or given a higher trust score by email security gateways. This enabled the phishing emails to land directly in inboxes, often bypassing spam folders and advanced threat protection layers.
- Familiarity and Credibility: The visual appearance and sender information of these phishing emails mimicked genuine Google Classroom notifications, making them highly convincing to unsuspecting recipients. Users are less likely to scrutinize emails from platforms they use daily.
- Scalability: Google Classroom’s notification system provides a ready-made, scalable infrastructure for mass communication. This allowed the threat actors to distribute a vast number of malicious emails with relative ease.
The Phishing Payload: What Were They After?
While the exact nature of the phishing payload isn’t detailed in the provided source, it’s highly probable that these campaigns sought to achieve common phishing objectives:
- Credential Theft: Luring users to fake login pages designed to capture usernames and passwords for various services (email, financial, corporate networks).
- Malware Delivery: Tricking users into downloading malicious attachments or clicking links that initiate drive-by downloads of malware (e.g., ransomware, info stealers).
- Financial Fraud: Impersonating legitimate entities to solicit fraudulent payments or capture sensitive financial information.
- Account Takeover: Gaining access to Google accounts, which can then be used for further internal phishing, data exfiltration, or accessing other linked services.
Remediation Actions and Proactive Defense
Organizations must adopt a multi-layered defense strategy to mitigate the risks posed by such sophisticated phishing attacks. This particular incident highlights the need to move beyond traditional perimeter defenses and focus on user education and endpoint security.
- Enhanced Email Security (Beyond Whitelisting):
- Implement advanced email security solutions that perform deep content inspection, even for emails from trusted domains.
- Utilize DMARC, DKIM, and SPF records effectively to prevent email spoofing, but understand their limitations when legitimate services are abused.
- Robust User Awareness Training:
- Conduct regular, interactive training sessions on identifying phishing attempts, even those from seemingly legitimate sources.
- Educate users about the dangers of unsolicited links and attachments, and the importance of verifying sender legitimacy through alternative communication channels.
- Train users to look for subtle anomalies in URLs, grammar, and tone, even in familiar interfaces.
- Multi-Factor Authentication (MFA):
- Enforce MFA across all critical accounts, especially for Google services. MFA significantly reduces the risk of account compromise, even if credentials are stolen.
- This is a critical control against CVE-2023-38831, which could be related to credential compromise.
- Endpoint Detection and Response (EDR):
- Deploy EDR solutions to monitor endpoints for suspicious activity, even if a user falls victim to a phishing attempt. This can detect and prevent malware execution or data exfiltration.
- Network Segmentation and Least Privilege:
- Segment networks to limit the lateral movement of attackers if a compromise occurs.
- Implement the principle of least privilege, ensuring users and applications only have access to resources absolutely necessary for their function.
- Incident Response Plan:
- Have a well-documented and regularly tested incident response plan in place to quickly detect, contain, and remediate successful phishing attacks.
Relevant Tools for Detection and Mitigation
| Tool Name | Purpose | Link |
|---|---|---|
| Proofpoint Email Protection | Advanced email security, URL rewriting, attachment sandboxing. | https://www.proofpoint.com/us/products/email-protection |
| KnowBe4 Security Awareness Training | User training, simulated phishing campaigns, security culture assessment. | https://www.knowbe4.com/ |
| Okta Adaptive MFA | Multi-Factor Authentication, adaptive policies, single sign-on. | https://www.okta.com/products/multi-factor-authentication/ |
| CrowdStrike Falcon Insight | Endpoint Detection and Response (EDR), threat hunting, managed detection. | https://www.crowdstrike.com/products/endpoint-security/falcon-insight-xdr/ |
Conclusion: Adapting to the Evolving Threat Landscape
The Google Classroom phishing campaign serves as a stark reminder that cyber threats are constantly evolving. Attackers will relentlessly seek novel ways to exploit trust and bypass security controls. Organizations can no longer rely solely on perimeter defenses; a comprehensive security strategy must include robust user education, multi-factor authentication, advanced threat detection capabilities, and a proactive incident response framework. Staying informed about the latest attack vectors and adapting defense mechanisms accordingly are critical for maintaining a resilient cybersecurity posture in the face of increasingly sophisticated threats.





