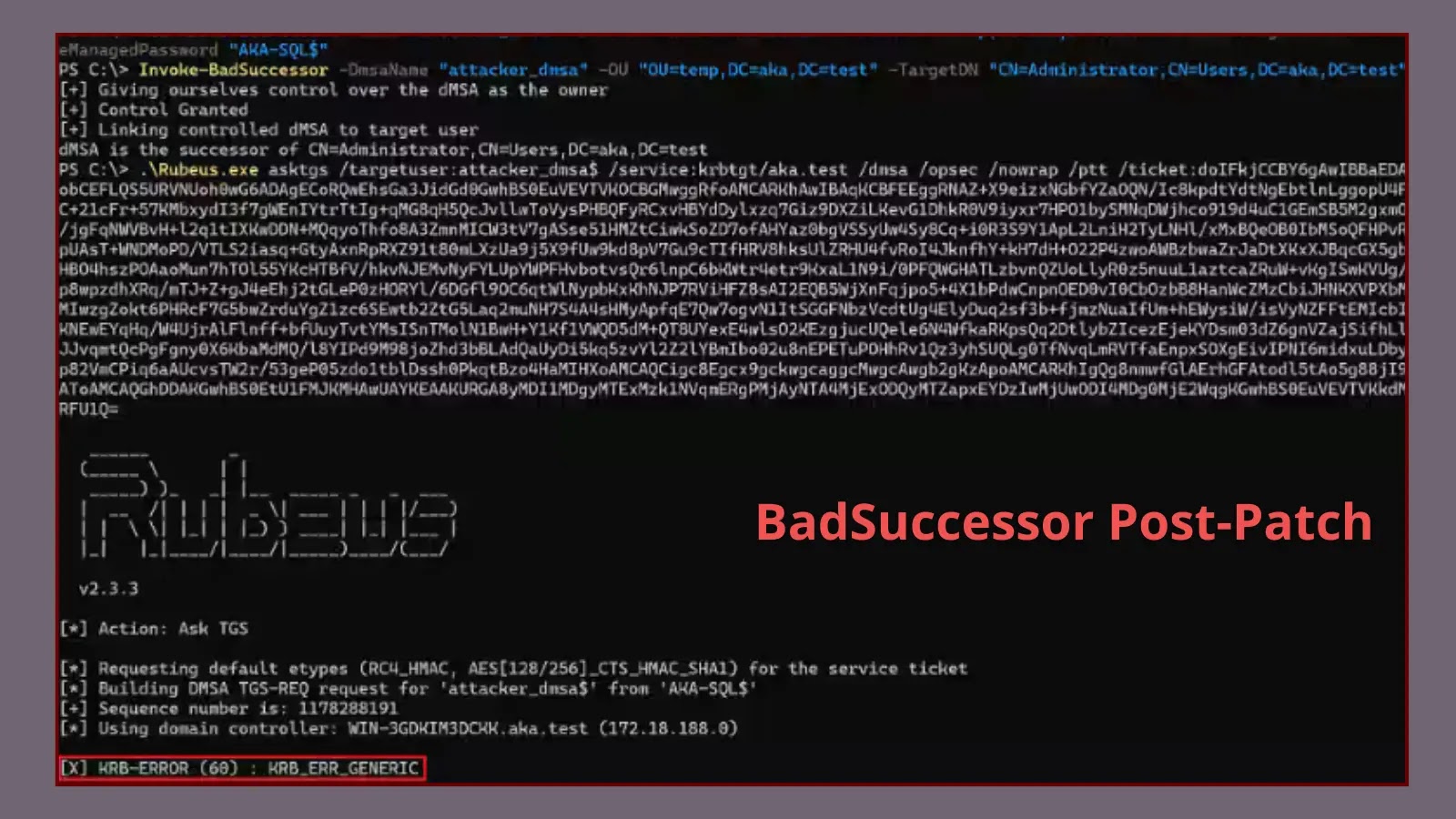
BadSuccessor Post-Patch: Leveraging dMSAs for Credential Acquisition and Lateral Movement in Active Directory
BadSuccessor Post-Patch: Persistent Credential Acquisition and Lateral Movement in Active Directory
The cybersecurity landscape demands constant vigilance. While vendors strive to patch vulnerabilities swiftly, sophisticated threat actors evolve, often finding new ways to exploit underlying mechanics. A prime example is the recent BadSuccessor vulnerability (tracked as CVE-2025-53779), for which Microsoft released a patch. Though the direct path to Domain Admin escalation has been closed, crucial revelations indicate that the fundamental technique for credential acquisition and lateral movement, particularly involving delegated Managed Service Accounts (dMSAs), remains a significant concern for Active Directory environments.
Understanding the Post-Patch Landscape of BadSuccessor
The initial fanfare around the BadSuccessor patch was understandable. It effectively severed a direct, high-impact privilege escalation route, preventing easy Domain Admin compromise stemming from one-sided delegated Managed Service Account links. However, security researchers quickly pointed out that the patch primarily addressed a specific manifestation of exploitation, not the core underlying method. This means that while immediate “easy button” Domain Admin escalation is mitigated, the mechanics for credential theft and subsequent lateral movement using dMSAs are still viable for determined attackers.
Threat actors can still leverage the fundamental principles of dMSAs to achieve their objectives. This often involves chaining different attack techniques, exploiting misconfigurations, or targeting other weak links within an Active Directory infrastructure to gain a foothold that allows them to then exploit dMSA-related weaknesses for credential harvesting.
The Role of Delegated Managed Service Accounts (dMSAs) in Post-Patch Exploitation
Managed Service Accounts (MSAs), and their evolution into Group Managed Service Accounts (gMSAs) and finally delegated MSAs (dMSAs), are designed to simplify service principal name (SPN) management and credential security for services. Their power lies in their ability to delegate credential management and authentication to specific hosts or users.
Post-patch, the risk associated with dMSAs shifts from direct privilege escalation to their potential for facilitating credential acquisition and lateral movement. Attackers aim to either:
- Identify and compromise systems authorized to retrieve dMSA credentials: If an attacker gains control over a server or workstation that has been delegated the ability to retrieve the password for a dMSA, they can effectively obtain the credential and impersonate the service.
- Manipulate dMSA delegations: In scenarios where an attacker has sufficient privileges (e.g., control over a privileged account or a misconfigured administrative group), they might attempt to alter dMSA delegations to grant themselves or a compromised host the ability to retrieve credentials.
- Leverage existing dMSA access for further reconnaissance: Even without directly obtaining the dMSA credential, knowledge of dMSA configurations and their associated service principal names (SPNs) can provide valuable information for mapping a network and identifying lucrative targets.
This subtle but critical distinction means that Active Directory administrators must now focus on broad hardening strategies rather than just relying on a single patch to safeguard against BadSuccessor-related techniques.
Credential Acquisition Tactics Post-Patch
Attackers are always looking for the path of least resistance. With the direct BadSuccessor path closed, their focus shifts to indirect methods for credential acquisition related to dMSAs:
- Host Compromise: A primary method involves compromising a host (server or workstation) that has legitimately been delegated the ability to retrieve a dMSA’s password. Once control over such a host is established, various tools can be used to extract the dMSA credential from memory or disk.
- Active Directory Misconfigurations: Weaknesses in Active Directory permissions, such as overly permissive delegations or service accounts with excessive rights, can be exploited. An attacker might manipulate these to gain the ability to request dMSA credentials.
- Kerberoasting/AS-REPing: While not directly tied to dMSAs, these techniques are often precursors or complementary. If an attacker gains a user account, they might use Kerberoasting against services where dMSAs are used as the service account, indirectly leading to insights or access that can be pivoted to dMSA exploitation.
- Lateral Movement using Acquired Credentials: Once a dMSA credential is acquired, it can be used to authenticate to services that rely on that MSA, potentially granting access to sensitive data, applications, or even other systems, leading to further lateral movement within the network.
Remediation Actions and Proactive Defense
Mitigating the post-patch risks of BadSuccessor-related attacks requires a multi-faceted approach focusing on Active Directory hygiene and robust security practices.
- Principle of Least Privilege Applied to dMSAs: Ensure that dMSA delegations are as restrictive as possible. Only the absolute minimum number of hosts or users should be authorized to retrieve dMSA credentials. Regularly review and audit these delegations.
- Regular Auditing of dMSA Configurations: Implement a robust auditing strategy for dMSA creation, modification, and access. Monitor for unusual retrieval requests or changes to delegation permissions.
- Endpoint Detection and Response (EDR) Implementation: Deploy EDR solutions across all endpoints and servers to detect suspicious activities indicative of host compromise or credential dumping attempts, even if a dMSA is the target.
- Network Segmentation: Isolate systems that host critical services utilizing dMSAs. Network segmentation can severely restrict an attacker’s ability to move laterally even if a single host is compromised.
- Identity and Access Management (IAM) Hardening: Strengthen overall IAM practices. Enforce strong, unique passwords for all accounts, implement multi-factor authentication (MFA) everywhere possible, and regularly review user and group permissions.
- Patch Management: Maintain a rigorous patch management program for all operating systems, applications, and Active Directory components beyond just the BadSuccessor patch.
- Security Awareness Training: Educate users and IT staff about social engineering techniques and the importance of reporting suspicious activity, as initial Footholds often come from human error.
Tools for Detection and Mitigation
Leveraging the right tools is crucial for identifying potential vulnerabilities, monitoring for suspicious activity, and responding effectively.
| Tool Name | Purpose | Link |
|---|---|---|
| BloodHound | Active Directory enumeration and attack path visualization, excellent for identifying potential lateral movement paths and misconfigurations. | https://bloodhound.readthedocs.io/en/latest/ |
| ADRecon | Active Directory security assessment script for gathering configuration data and identifying weaknesses. | https://github.com/sensepost/ADRecon |
| PingCastle | Active Directory security assessment and risk analysis tool. | https://www.pingcastle.com/ |
| Mimikatz | Post-exploitation tool for credential dumping (useful for testing host compromise scenarios in a controlled environment). | https://github.com/gentilkiwi/mimikatz |
| Microsoft Defender for Identity | Behavioral analytics for Active Directory, helping detect suspicious activities and attacks targeting identities. | https://www.microsoft.com/security/business/microsoft-365-defender/identity |
Conclusion
The post-patch reality of BadSuccessor highlights a critical truth in cybersecurity: a single patch, no matter how impactful, is rarely the panacea. While Direct Domain Admin escalation through the original BadSuccessor vector is mitigated, the underlying techniques involving dMSAs are still viable for credential acquisition and lateral movement within Active Directory. Robust Active Directory hygiene, adherence to the principle of least privilege for dMSAs, continuous monitoring, and the strategic deployment of security tools are essential to protect against the persistent risk posed by sophisticated attackers exploiting these fundamental mechanics. Proactive defense, rather than reactive patching alone, is the only sustainable path to Active Directory security.





