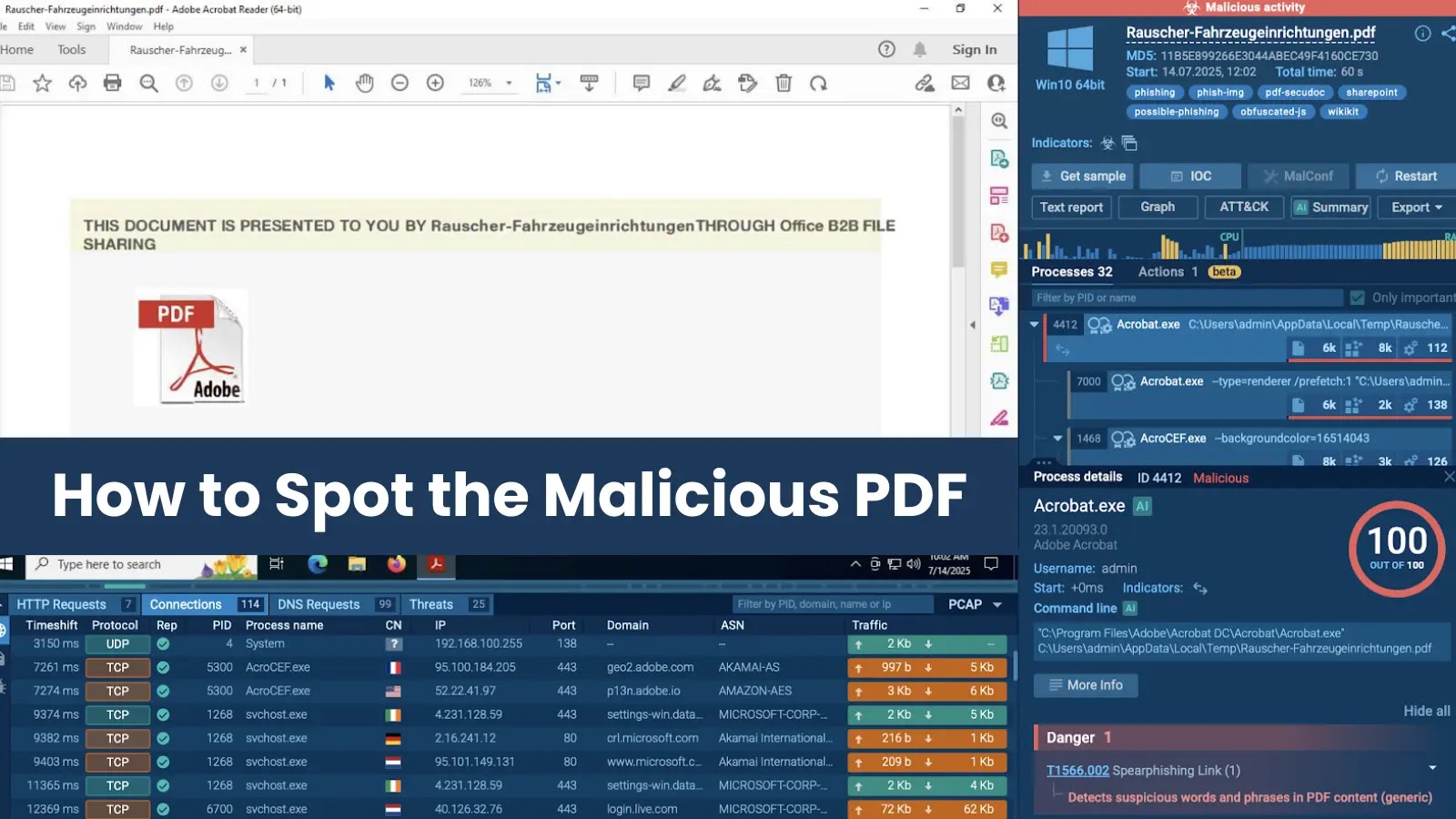
Attackers Are Abusing Malicious PDFs: Here’s How to Spot Them Early
The digital landscape is a minefield, and attackers are constantly evolving their tactics. While many organizations focus on perimeter defenses and email security, a stealthier threat is gaining traction: malicious PDFs. These aren’t your typical phishing links; instead, threat actors are weaponizing seemingly innocuous documents, turning everyday files into potent vectors for credential theft, malware delivery, and data compromise.
The Deceptive Nature of Malicious PDFs
For too long, the common perception of phishing attacks revolved around suspicious links in emails. However, the sophisticated threat actor has moved beyond such easily identifiable indicators. Today, they are hiding their intent within files employees inherently trust: Portable Document Format (PDF) files. On the surface, these documents appear legitimate – an invoice, a contract, a sensitive report. Their very familiarity breeds a false sense of security, making them incredibly effective in bypassing traditional detection mechanisms and user scrutiny.
Once opened, these malicious PDFs can trigger a multitude of hidden actions. This might include executing embedded scripts, quietly redirecting users to convincing, yet fake, login pages designed to harvest credentials, or initiating the silent download of malware. The danger is amplified by their convincing appearance and the widespread reliance on PDFs for legitimate business operations. This makes it challenging for even vigilant users to discern legitimate documents from malicious ones before it’s too late.
Advanced Attack Vectors Exploiting PDFs
Attackers leverage various techniques to embed malicious functionality within PDFs, exploiting inherent PDF features and common vulnerabilities. These techniques are designed to bypass security controls and trick users into exposing their systems or credentials.
- Embedded Scripts: PDFs support embedded JavaScript. Attackers can leverage this to execute malicious code when the document is opened, initiating downloads, redirecting to phishing sites, or even interacting with local file systems. For example, a script could attempt to exploit vulnerabilities in PDF readers.
- Phishing Redirections: Malicious PDFs can contain links that, when clicked, redirect users to sophisticated phishing pages. These pages are often meticulously crafted to mimic legitimate services (e.g., cloud storage, online banking, organizational portals) and harvest login credentials. The user, believing they are interacting with a trusted service, willingly inputs their sensitive information.
- Quiet Credential Theft: Beyond overt phishing pages, some advanced techniques allow for silent credential theft. This could involve exploiting vulnerabilities that automatically send credentials to an attacker’s server when a specific action is performed within the PDF, or by leveraging social engineering tactics within the document itself to prompt users for credentials.
- Exploiting PDF Renderer Vulnerabilities: Historically, vulnerabilities in PDF rendering engines (like Adobe Acrobat Reader or other third-party viewers) have been a major avenue for attack. Exploits such as CVE-2023-29367 or CVE-2023-38202 highlight how critical flaws in the way PDF viewers process certain elements can lead to arbitrary code execution simply by opening a crafted PDF.
- Embedded Files and Payloads: PDFs can contain embedded files, including executables or other malicious documents. An attacker might embed a ZIP file containing malware, relying on social engineering to convince the user to open it.
Spotting Malicious PDFs Early: Key Indicators
Identifying a malicious PDF requires a combination of technical awareness and careful observation. Training employees to recognize these subtle cues is paramount in preventing breaches.
- Unexpected or Unsolicited Documents: Always be wary of PDFs received from unknown senders, or even known senders if the document is unexpected or out of context. A sudden “invoice” or “contract” that deviates from normal business practices should raise immediate suspicion.
- Generic or Urgency-Driven Subject Lines/Content: Attackers often use generic subject lines (e.g., “Urgent Document,” “Invoice #12345”) or content that conveys a sense of urgency to pressure recipients into opening the file without proper scrutiny.
- Unusual Naming Conventions or File Extensions: While the extension will be .pdf, scrutinize the full file name. Attackers sometimes use double extensions (e.g., “Invoice.pdf.exe” if extensions are hidden) or suspicious characters.
- Requests for Credentials: A legitimate PDF will rarely ask for your login credentials directly within the document or via a link embedded in it. If a PDF prompts you to log into an external service, especially one you’re already logged into, it’s a strong indicator of a phishing attempt. Always verify the URL in your browser’s address bar.
- Interactive Elements in Static Documents: PDFs are generally static documents. If a PDF has unusual interactive elements (e.g., pop-up windows asking to enable content, embedded forms that seem out of place, or requests to “click here to view content”), proceed with extreme caution.
- Excessive Hyperlinks or Obfuscated Links: Hover over any links in the PDF (without clicking!) to see the underlying URL. If the displayed URL doesn’t match the destination you expect, or if it’s a shortened or obfuscated link, it’s highly suspicious.
- Grammatical Errors or Inconsistencies: While not exclusive to PDFs, poor grammar, spelling mistakes, and awkward phrasing can be red flags in any communication, including documents.
Remediation Actions and Proactive Defenses
Mitigating the risk of malicious PDFs requires a multi-layered approach, combining technology, policy, and user education.
- Email Filtering and Sandboxing: Implement robust email security gateways that include advanced threat protection capabilities. Ensure these systems perform deep content inspection of attachments, including PDFs, and utilize sandboxing to execute suspicious files in an isolated environment before they reach user inboxes.
- Endpoint Detection and Response (EDR)/Extended Detection and Response (XDR): Deploy EDR/XDR solutions that can monitor endpoint behavior for suspicious activities, such as unusual process creation initiated by PDF readers, attempts to access sensitive files, or network connections to known malicious domains.
- Regular Software Updates and Patching: Keep all PDF readers (e.g., Adobe Acrobat Reader, Foxit Reader, browser-based PDF viewers) and operating systems updated. Attackers frequently exploit known vulnerabilities like CVE-2023-42479 or CVE-2023-42480 in outdated software.
- User Education and Awareness Training: Conduct regular, hands-on security awareness training for all employees. Emphasize the dangers of unsolicited attachments, how to inspect links, and the importance of verifying sender legitimacy. Teach them the visible indicators of malicious PDFs discussed above.
- Disable JavaScript in PDF Readers (if feasible): While it may reduce some legitimate functionality, disabling JavaScript execution in PDF readers can significantly reduce the attack surface for script-based PDF exploits. Assess the impact on business operations before implementing.
- Implement a Least Privilege Model: Ensure users operate with the minimum necessary privileges. This limits the damage an attacker can inflict even if a malicious PDF is successfully opened.
- Document Sanitization Services: Consider using data sanitization or content disarm and reconstruction (CDR) solutions. These tools analyze documents, remove potentially malicious active content, and then reconstruct a clean, safe version of the file, delivering it to the end-user.
- Block Macros and External Content: Configure PDF readers and related software to block macros and prevent the automatic download of external content where possible.
Relevant Tools for Detection and Mitigation
Leveraging the right tools can significantly enhance an organization’s ability to defend against malicious PDFs.
| Tool Name | Purpose | Link |
|---|---|---|
| Virustotal | Online service for analyzing suspicious files and URLs. Upload a PDF to check for known malicious signatures. | https://www.virustotal.com/ |
| ANY.RUN | Interactive online sandbox for malware analysis, including malicious PDF behavior. | https://any.run/ |
| PeePDF | Python tool for analyzing and obfuscating PDF files. Useful for security researchers. | https://github.com/jesparza/peepdf |
| Adobe Acrobat/Reader (Security Settings) | Built-in security settings allow for disabling JavaScript, managing trusted locations, and Enhanced Security. | Refer to Adobe Support |
| Proofpoint, Mimecast, Microsoft Defender for Office 365 | Leading email security gateways that offer advanced threat protection, sandboxing, and attachment analysis. | Proofpoint Mimecast Microsoft Defender |
Conclusion
The threat landscape is dynamic, and attackers continue to exploit trusted file formats like PDFs to bypass traditional security controls. Organizations must recognize that a substantial portion of phishing attacks now reside within these seemingly innocuous documents. By understanding the vectors, educating employees on the indicators of compromise, and implementing robust technical controls, businesses can significantly reduce their exposure to malicious PDFs. Proactive defense and continuous vigilance are essential to protect against these evolving threats.





