Microsoft Patch for Old Flaw Reveals New Kernel Address Leak Vulnerability in Windows 11/Server 2022 24H2
In the intricate world of cybersecurity, a fix for one vulnerability can, at times, inadvertently introduce another. Such is the paradoxical nature of software development and security patching, a reality vividly illustrated by a recent discovery in Microsoft’s latest Windows iterations. A newly identified kernel address leak vulnerability, designated as CVE-2025-53136, has surfaced in Windows 11 (version 24H2) and Windows Server 2022 (version 24H2). What makes this particular flaw noteworthy is its origin: it was seemingly introduced by a Microsoft patch intended to address a different, older security issue, CVE-2024-43511. This situation raises important questions about the continuous cat-and-mouse game between developers and attackers, and the constant need for vigilant security auditing.
The Paradox of Patching: CVE-2025-53136 Unveiled
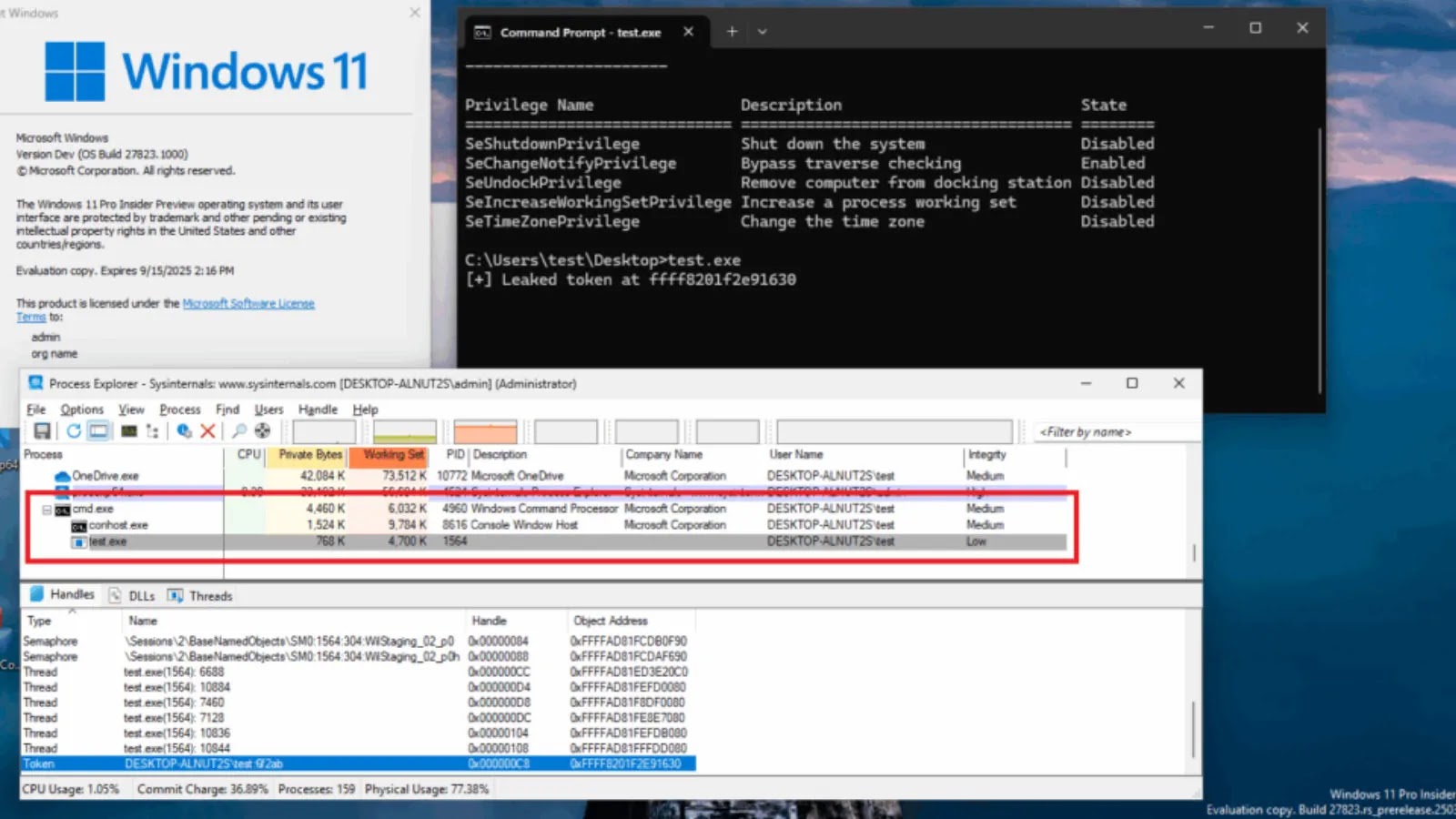
The core of this new concern lies in a kernel address leak identified as CVE-2025-53136. This vulnerability impacts the most current versions of Microsoft’s operating systems, specifically Windows 11 24H2 and Windows Server 2022 24H2. According to security researchers at Crowdfense, the irony is particularly sharp: this new vulnerability emerged as a consequence of a patch designed to rectify CVE-2024-43511. This highlights the inherent complexities of low-level system changes, where even well-intentioned fixes can have unintended security implications.
Understanding Kernel Address Leaks and Their Impact
A kernel address leak is a critical type of information disclosure vulnerability. In essence, it allows an attacker to gain knowledge about the memory layout of the operating system kernel. While an address leak by itself doesn’t directly grant control over a system, it is often a crucial prerequisite for launching more sophisticated attacks, particularly those involving privilege escalation. By understanding where key kernel structures reside in memory, attackers can bypass security mechanisms like Address Space Layout Randomization (ASLR), making it significantly easier to craft exploits for other vulnerabilities. Essentially, it removes a層 of defense, paving the way for more severe compromises.
Subverting Security Enhancements
The discovery of CVE-2025-53136 is particularly troubling because it undermines recent security enhancements in Windows. Microsoft consistently implements new protections to harden their operating systems against advanced threats. When a new vulnerability, especially one related to memory disclosure, negates the effectiveness of these protections, it represents a step backward in the overall security posture. For IT professionals and security analysts, this means that the latest updates, while necessary, may also introduce new, albeit subtle, attack vectors that require careful attention.
Remediation Actions and Best Practices
Given the nature of kernel address leaks as potential stepping stones for more severe attacks, prompt action is crucial. While a direct patch for CVE-2025-53136 is not yet available, organizations can adopt several best practices to mitigate associated risks and bolster their overall security defenses:
- Monitor for Official Patches: IT teams should diligently monitor Microsoft’s official security advisories and update channels for an official patch addressing CVE-2025-53136. Prompt deployment of future security updates is paramount.
- Implement Least Privilege: Enforce the principle of least privilege across all user accounts and system processes. Limiting the capabilities of user accounts can significantly reduce the impact of any successful exploit, even if an address leak is leveraged.
- Deploy Advanced Endpoint Detection and Response (EDR): EDR solutions can help detect anomalous behavior that might indicate an attack attempting to exploit vulnerabilities, even those that don’t yet have direct patches.
- Network Segmentation: Isolate critical systems and sensitive data using network segmentation. This limits an attacker’s lateral movement capabilities even if they manage to compromise an endpoint.
- Regular Security Audits: Conduct frequent internal and external security audits and penetration testing to identify and address weaknesses before they can be exploited.
Relevant Security Tools
| Tool Name | Purpose | Link |
|---|---|---|
| Microsoft Defender for Endpoint | Advanced endpoint detection and response (EDR) capabilities | https://www.microsoft.com/en-us/security/business/threat-protection/microsoft-defender-for-endpoint |
| Sysinternals Suite (Process Monitor, Process Explorer) | Detailed system monitoring and process introspection for anomaly detection | https://learn.microsoft.com/en-us/sysinternals/ |
| Vulnerability Management Solutions (e.g., Tenable.io, Qualys) | Scanning for known vulnerabilities and misconfigurations across systems | https://www.tenable.com/products/tenable-io (Example) |
Continuing Vigilance in Windows Security
The emergence of CVE-2025-53136 serves as a stark reminder of the ongoing challenges in securing complex operating systems. While Microsoft continuously strives to enhance the security of Windows, the iterative nature of development and patching means that new vulnerabilities can, and do, arise. For professionals tasked with maintaining secure environments, this necessitates a proactive stance: staying informed about new threats, implementing layered defenses, and prioritizing the timely application of security updates. The battle for digital security is continuous, demanding constant adaptation and unwavering vigilance.





