BitlockMove Tool Enables Lateral Movement via Bitlocker DCOM & COM Hijacking
BitlockMove: A New Frontier in Lateral Movement via BitLocker DCOM & COM Hijacking
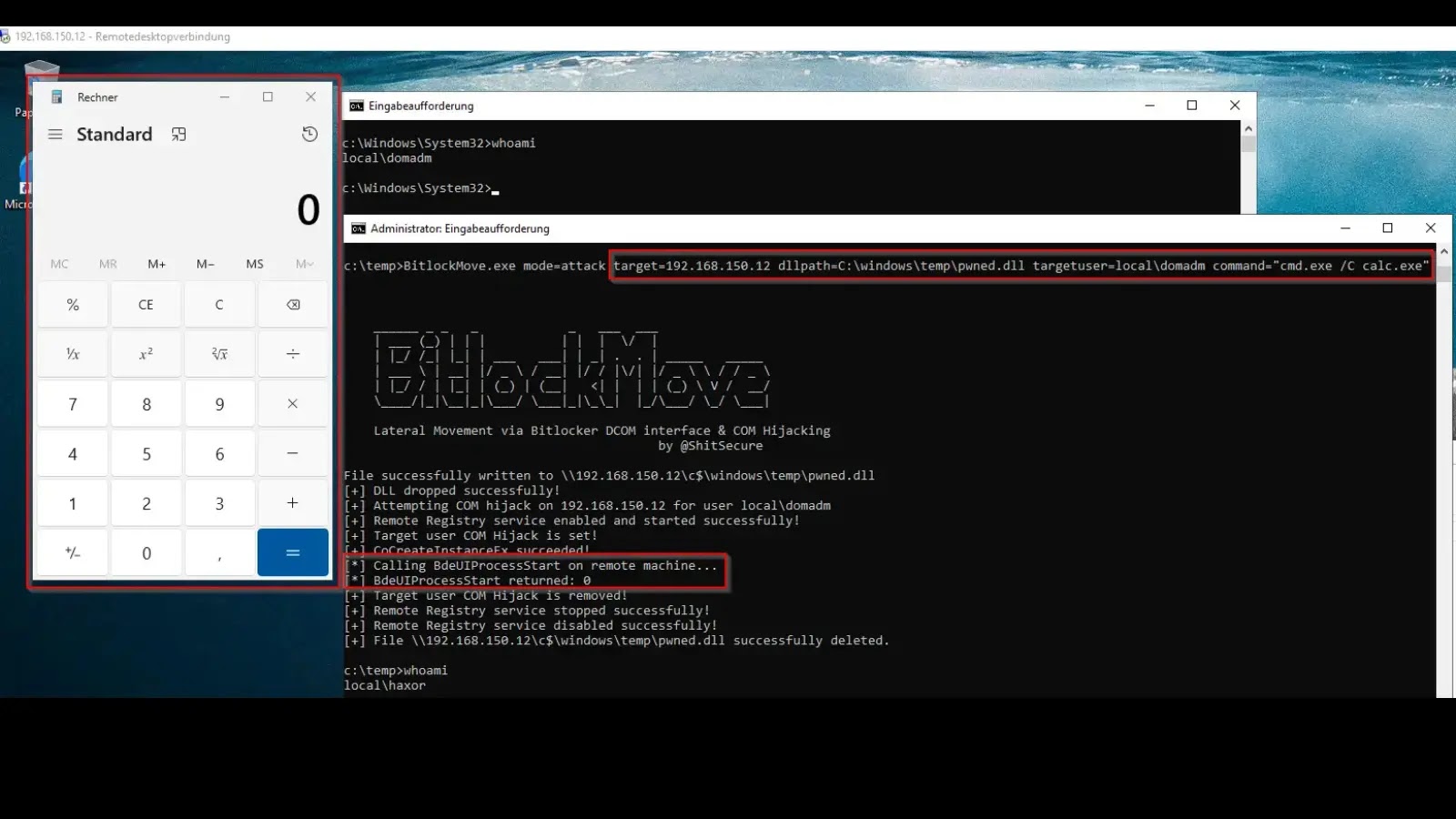
The landscape of enterprise security is constantly challenged by novel attack methodologies. A significant new development has emerged with the release of a proof-of-concept (PoC) tool named BitlockMove. This tool demonstrates a sophisticated lateral movement technique that weaponizes Microsoft’s BitLocker Distributed Component Object Model (DCOM) interfaces and leverages COM hijacking. Unveiled by security researcher Fabian Mosch of r-tec Cyber Security, BitlockMove provides attackers with a powerful vector to execute arbitrary code on remote systems within the context of an already logged-on user.
Understanding the Threat: BitLocker DCOM and COM Hijacking
Lateral movement is a critical phase in many advanced persistent threats (APTs). Once an attacker gains initial access to one system, their objective often shifts to expanding their foothold and reaching high-value targets within the network. BitlockMove exploits vulnerabilities in how BitLocker interacts with DCOM and the broader COM infrastructure, offering a stealthy path for this expansion.
- Distributed Component Object Model (DCOM): DCOM is a proprietary Microsoft technology that allows software components to communicate directly over network connections. It extends COM to support objects distributed across a network, enabling applications to interact with remote services. Properly secured DCOM is essential for a robust network.
- Component Object Model (COM) Hijacking: COM hijacking involves manipulating the Windows registry to redirect calls for a legitimate COM object to a malicious one. Attackers can register their hostile DLLs or executables to be invoked when a legitimate application attempts to use a specific COM interface. This technique is often used for persistence, privilege escalation, or, as demonstrated here, lateral movement.
BitlockMove capitalizes on the fact that BitLocker, a fundamental security feature for disk encryption, exposes DCOM interfaces that can be manipulated. By combining this with COM hijacking, an attacker can trick a remote system into loading and executing malicious code whenever a legitimate process attempts to interact with BitLocker or related services that rely on the compromised COM object.
How BitlockMove Operates
The BitlockMove PoC tool demonstrates a multi-stage attack flow:
- Initial Foothold: Assumes an attacker already has some level of access to a system within the target network.
- Target Identification: Identifies remote systems where a user is logged on and where vulnerable BitLocker DCOM services are accessible.
- COM Hijacking Preparation: Sets up the necessary registry keys on the target system to facilitate COM hijacking. This typically involves modifying HKEY_CURRENT_USER or HKEY_LOCAL_MACHINE entries to point to a malicious DLL.
- DCOM Call Initiation: Initiates a DCOM call to a BitLocker interface on the remote system. This legitimate call triggers the loading of the hijacked COM object.
- Code Execution: The malicious DLL, now loaded by a legitimate process on the remote machine, executes arbitrary code within the context of the logged-on user’s session. This grants the attacker significant control, potentially allowing for further reconnaissance, data exfiltration, or the deployment of additional malware.
Crucially, this method operates within the session of an already logged-on user. This can make detection more challenging as the executed code often blends in with legitimate user activity.
Remediation Actions and Mitigation Strategies
Defending against advanced lateral movement techniques like those demonstrated by BitlockMove requires a multi-layered security approach. Organizations should focus on proactive measures and robust monitoring.
- Principle of Least Privilege (PoLP): Ensure users and service accounts operate with the absolute minimum privileges required for their tasks. Restricting administrative access significantly limits an attacker’s ability to perform COM hijacking.
- Application Whitelisting: Implement strict application whitelisting policies to prevent the execution of unauthorized executables and DLLs. Tools like Windows Defender Application Control (WDAC) or AppLocker can effectively block malicious COM objects from loading.
- Endpoint Detection and Response (EDR): Deploy and meticulously configure EDR solutions to monitor for anomalous process behavior, registry modifications, and suspicious network connections. Look for unexpected DCOM activity or unusual DLL loads.
- Network Segmentation: Segment your network to limit the blast radius of a successful compromise. Proper segmentation can prevent an attacker from easily moving from one compromised system to critical assets.
- Timely Patching: While BitlockMove exploits a design aspect rather than a specific vulnerability, keeping all systems and software updated with the latest security patches is always crucial. This minimizes other potential entry points.
- Audit and Monitor DCOM Activity: Regularly audit and monitor DCOM activation events. Look for DCOM calls from unusual sources or to unusual BitLocker interfaces.
- Registry Integrity Monitoring: Monitor critical registry keys, especially those related to COM object registration (e.g., HKEY_CLASSES_ROOT\CLSID, HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID), for unauthorized modifications.
Relevant Tools for Detection and Mitigation
Leveraging appropriate cybersecurity tools is essential for detecting and mitigating threats posed by techniques like BitlockMove. Here are some categories and examples:
| Tool Category/Name | Purpose | Link |
|---|---|---|
| Endpoint Detection and Response (EDR) Solutions | Detects and responds to advanced threats, including anomalous process execution, registry changes, and network activity associated with lateral movement. | Varies by Vendor (e.g., Microsoft Defender for Endpoint, CrowdStrike Falcon, SentinelOne) |
| Sysmon | Windows system service and device driver that monitors and logs system activity to the Windows event log. Excellent for tracking process creation, network connections, and registry modifications. | https://learn.microsoft.com/en-us/sysinternals/downloads/sysmon |
| Windows Defender Application Control (WDAC) / AppLocker | Application whitelisting technologies that enforce code integrity policies, preventing unauthorized executables and scripts from running. | https://learn.microsoft.com/en-us/windows/security/application-security/application-control/windows-defender-application-control/wdac-design-guide |
| Group Policy Management Editor | Used to configure and deploy security policies across Windows domains, including settings for DCOM access restrictions and registry key permissions. | Built-in Windows tool |
| PowerShell (for scripting/auditing) | Can be used to audit DCOM permissions, registry key integrity, and active processes for suspicious signs. | Built-in Windows tool |
Conclusion
The emergence of tools like BitlockMove underscores the continuous evolution of attack techniques and the importance of staying ahead of adversaries. By leveraging existing system functionalities such as BitLocker DCOM interfaces and established attack vectors like COM hijacking, attackers can achieve sophisticated lateral movement with potentially low-detectability. Security teams must prioritize strong endpoint security, robust network segmentation, and proactive monitoring to defend against these advanced threats. Understanding these mechanisms is key to building resilient cybersecurity postures.





