Rules-as-Code The Future of Automated Cybersecurity Compliance.
AI Automate Cybersecurity Compliance: AI-Powered Automation
In an era where digital transformation is the backbone of business innovation, ensuring robust cybersecurity compliance is crucial to mitigating security risks. As organizations increasingly rely on digital infrastructure, the risks associated with cybersecurity threats continue to escalate. AI-powered automation emerges as a formidable ally in this landscape, streamlining compliance processes and enhancing security postures. By automating compliance tasks, businesses can efficiently manage regulatory requirements, safeguard critical infrastructure, and bolster their defenses against potential data breaches and cyber threats. Teamwin Global Technologica is at the forefront of this evolution, empowering clients with reliable solutions to secure their enterprises and ensure future success.
Understanding Cybersecurity Compliance
Definition and Importance of Compliance
Cybersecurity compliance entails adhering to a set of security standards and regulatory requirements designed to protect information systems and data. This compliance is not merely a checkbox exercise but a strategic necessity that fortifies an organization’s security posture. By integrating best practices and automated enforcement mechanisms, companies can safeguard their digital assets, mitigate vulnerabilities, and reduce the risk of data breaches while enhancing their overall cybersecurity policy. Compliance is crucial for maintaining customer trust and ensuring the integrity of business operations. Teamwin Global Technologica assures your infrastructure is secure and compliant, providing peace of mind and protection against evolving threats.
Overview of Cybersecurity Regulations
Cybersecurity regulations are frameworks established to guide organizations in implementing security measures and policies that protect sensitive data and information systems. These regulations, such as GDPR, HIPAA, and PCI-DSS, set the compliance standards for various industries, aiming to prevent data breaches and cyber risks. Compliance automation through AI-powered tools enables businesses to seamlessly integrate these regulations into their security protocols, ensuring continuous compliance and reducing the complexity of manual audits. As experts in cybersecurity and compliance, Teamwin Global Technologica helps navigate these regulatory landscapes, safeguarding your enterprise and ensuring tomorrow’s success.
The Impact of the Threat Landscape on Compliance
The ever-evolving threat landscape poses significant challenges to maintaining cybersecurity compliance. As cyber threats become more sophisticated, organizations must adapt their security measures and compliance strategies to mitigate these risks. The integration of AI in compliance checks allows for proactive threat detection and incident response, ensuring that security controls are consistently aligned with current vulnerabilities. By automating compliance processes, businesses can swiftly adjust to new threats, maintain robust cybersecurity postures, and protect their supply chains from emerging cybersecurity risks. Teamwin Global Technologica fortifies your business against potential threats, empowering you with vigilant monitoring and swift response strategies to maintain compliance and security.
AI-Powered Automation in Cybersecurity
What is AI and How Does it Enhance Compliance?
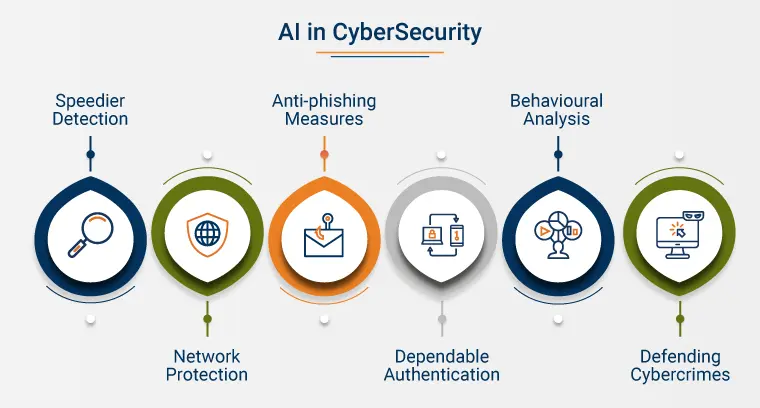
Artificial Intelligence (AI) refers to the simulation of human intelligence processes by machines, particularly computer systems, which can play a crucial role in enhancing cyber defense. In the realm of cybersecurity compliance, AI serves as a transformative force capable of enhancing compliance efforts through advanced data analysis, threat detection, and automated policy enforcement. By leveraging AI, security teams can automatically monitor compliance management requirements in real time, ensuring that security controls are aligned with the latest regulatory standards set by the national institute of standards. This integration not only strengthens an organization’s security posture but also streamlines the process of identifying and addressing vulnerabilities, thereby reducing the risk of data breaches and non-compliance.
Benefits of Automating Compliance Processes
Automating compliance processes offers numerous advantages, making it an essential strategy for modern organizations. There are several key benefits to implementing compliance automation:
- It reduces the complexity and time associated with manual audits, allowing businesses to focus on core operations while maintaining continuous compliance.
- It enhances data security by implementing policy as code, ensuring that security rules are consistently applied across the infrastructure.
This automated enforcement mitigates cyber threats and strengthens critical infrastructure, providing a robust defense against potential vulnerabilities. By integrating automated systems, organizations also achieve improved risk management, safeguarding their supply chains and fortifying their defenses against evolving cyber risks.
Case Studies of AI in Cybersecurity Compliance
Numerous case studies highlight the success of AI in transforming cybersecurity compliance. Here are some notable examples:
- A leading financial institution integrated AI-powered tools to automate compliance checks, resulting in a 40% reduction in manual audit times and a significant decrease in compliance-related incidents.
- Another example involves a healthcare provider that utilized AI to enhance its data security, enabling real-time threat detection and incident response. This proactive approach not only ensured compliance with stringent regulatory requirements like HIPAA but also safeguarded sensitive patient data.
Such cases underscore the potential of AI to revolutionize compliance processes, empowering organizations to maintain robust security and compliance standards.
Implementing Compliance Automation
Strategies for Automating Compliance Checks
In the evolving landscape of cybersecurity, implementing strategies for automating compliance checks is crucial for maintaining robust security postures. Automation of compliance processes allows organizations to seamlessly integrate cybersecurity compliance into their operations, ensuring that compliance requirements are consistently met without the burden of manual interventions. These strategies involve the use of AI-powered tools to continuously monitor security controls and policies, identifying vulnerabilities and cyber threats promptly, thus improving cyber defense. By automating compliance checks, organizations not only streamline their audit processes but also enhance data security, reducing the risk of data breaches and ensuring that their critical infrastructure remains secure and compliant with the latest cybersecurity regulations.
Compliance as Code: A Modern Approach
Compliance as code represents a groundbreaking approach to modern cybersecurity compliance, transforming how organizations enforce security standards. By treating compliance policies as code, businesses can automate the enforcement of compliance requirements across their infrastructure, ensuring consistency and accuracy. This approach allows for real-time updates to reflect the latest regulatory requirements, significantly reducing the risk of non-compliance. Compliance as code also enhances risk management by providing a clear and auditable trail of compliance activities. By integrating compliance as code into their security frameworks, organizations fortify their defenses against cyber threats, ensuring that security and compliance are effectively managed and aligned with best practices.
Integrating Policy as Code into Security Practices
The integration of policy as code into security practices is a strategic advancement in the realm of cybersecurity. This methodology allows organizations to automate the implementation and enforcement of security policies, ensuring that security measures are consistently applied across all systems. By leveraging policy as code, businesses can proactively manage cyber risks, swiftly adapt to changing threat landscapes, and maintain continuous compliance with cybersecurity standards. This integration not only simplifies the management of security controls but also enhances the resilience of information security infrastructures. With policy as code, organizations can efficiently safeguard their supply chains and critical infrastructure, empowering them to anticipate and mitigate potential vulnerabilities before they impact their operations.
Infrastructure as Code and Security Compliance
How Infrastructure as Code Supports Compliance
Infrastructure as Code (IaC) is revolutionizing the way organizations approach security compliance by providing a framework that integrates compliance requirements directly into the development and deployment processes. With IaC, security policies and compliance standards are codified, ensuring automated enforcement across all environments. This approach not only streamlines compliance checks but also enhances the accuracy of security measures, reducing the risk of human error. By embedding compliance into the very fabric of software development, organizations can achieve continuous compliance, fortifying their security posture against evolving cyber threats and ensuring that their critical infrastructure remains resilient and secure.
Best Practices for Security as Code
Implementing security as code requires adherence to best practices that ensure robust cybersecurity compliance. Organizations should integrate policy as code to automate the enforcement of security controls, thereby maintaining consistency and minimizing vulnerabilities. Regular audits and compliance checks are essential to identify potential risks and align security measures with the latest regulatory requirements. Additionally, fostering a culture of continuous improvement and collaboration among security teams can enhance incident response capabilities and fortify defenses against cyber risks. By adopting these best practices, organizations can safeguard their supply chains, protect critical data, and ensure that their security frameworks are both resilient and agile.
Challenges in Implementing Infrastructure as Code
While Infrastructure as Code offers significant benefits for cybersecurity compliance, its implementation is not without challenges related to security risk. Organizations may face difficulties in aligning IaC practices with existing security policies and regulatory requirements. Additionally, the complexity of automating compliance across diverse environments can pose significant obstacles. Ensuring seamless integration of IaC with existing cybersecurity frameworks requires careful planning and expertise. Overcoming these challenges demands a commitment to continuous learning and adaptation, empowering security teams to effectively manage cyber risks and maintain the integrity of their information security infrastructures. By addressing these challenges, organizations can unlock the full potential of IaC, ensuring robust compliance and security.
The Future of Cybersecurity Compliance
Emerging Trends in Compliance Automation
The landscape of cybersecurity compliance is rapidly evolving, with emerging trends in compliance automation paving the way for more efficient and robust security measures. Organizations are increasingly leveraging AI and machine learning to automate compliance processes, enabling real-time monitoring and swift adaptation to changing regulatory landscapes. Here are some key practices being adopted in the realm of cloud security:
- The integration of automated enforcement mechanisms is becoming a standard practice, ensuring continuous compliance and reducing the complexity of manual audits.
- Businesses can anticipate a future where compliance is seamlessly integrated into their operations, safeguarding their enterprises against cyber threats and ensuring peace of mind.
The Role of AI in Shaping Future Cybersecurity Laws
Artificial Intelligence is playing a pivotal role in shaping the future of cybersecurity laws and regulations. As AI technologies become more sophisticated, they offer new capabilities for monitoring and enforcing compliance standards. Policymakers are recognizing the potential of AI to enhance cybersecurity strategies, leading to the development of regulations that encourage the integration of AI in compliance frameworks. This shift not only strengthens security postures but also provides a foundation for more adaptive and resilient regulatory environments. By embracing AI, organizations can anticipate and mitigate cyber risks, ensuring that their security measures remain aligned with both current and future compliance requirements.
Preparing for the Future: Managing Cyber Risk
In an era of increasing cyber threats, preparing for the future requires a proactive approach to managing cyber risk. Organizations must implement comprehensive risk management strategies that integrate compliance automation and advanced security measures. By leveraging AI and infrastructure as code, companies can enhance their incident response capabilities, ensuring swift and effective action against potential vulnerabilities. Continuous monitoring and adaptation are crucial to maintaining a resilient cybersecurity posture, protecting critical infrastructure, and safeguarding sensitive data in the face of evolving cybersecurity risks. As the threat landscape evolves, organizations that prioritize these strategies will be well-equipped to navigate the complexities of cybersecurity compliance and secure their enterprises for the future.
5 Surprising Facts about Rules-as-Code and the Future of Automated Cybersecurity Compliance
- Rules-as-Code transforms traditional regulatory frameworks into executable code, enabling real-time compliance monitoring.
- This approach significantly reduces the time and cost associated with compliance audits by automating the verification process.
- Organizations that implement Rules-as-Code can achieve a higher level of accuracy in compliance reporting, minimizing human error.
- Rules-as-Code facilitates better collaboration between legal, compliance, and IT departments by providing a clear and executable representation of regulations.
- The adoption of Rules-as-Code is expected to grow rapidly, with predictions indicating a 50% increase in use among organizations by 2025.
What is rules-as-code in the context of cybersecurity compliance?
Rules-as-code refers to the practice of translating regulatory compliance requirements into executable code. This approach allows organizations to implement automated tools that ensure their cybersecurity measures align with the necessary policy compliance. By utilizing rules-as-code, businesses can streamline their compliance processes and enhance their overall cybersecurity posture.
How can organizations achieve compliance using automated tools?
Organizations can achieve compliance by employing automated tools that monitor and enforce cybersecurity measures according to predefined rules. These tools help with compliance verification by continuously assessing the compliance status and ensuring that security requirements are met. This proactive compliance approach minimizes the risk of security breaches and enhances the organization’s cybersecurity maturity model certification.
What are the benefits of compliance automation for cybersecurity?
Compliance automation provides several benefits, including increased efficiency in managing security operations, reduced manual errors, and improved accuracy in compliance checks. By automating the compliance process, organizations can focus on more strategic cybersecurity risk management activities, allowing cybersecurity professionals to concentrate on preventing potential threats rather than merely reacting to them.
How does infrastructure as code relate to cybersecurity compliance?
Infrastructure as code (IaC) allows organizations to manage their IT infrastructure through code, facilitating automated compliance checks against security and compliance standards. This method ensures that all infrastructure changes adhere to regulatory compliance, helping organizations maintain their compliance posture and reduce the risk of non-compliance penalties.
What role do AI tools play in enhancing cybersecurity compliance?
AI tools play a crucial role in enhancing cybersecurity compliance by providing advanced analytics and insights into potential vulnerabilities. These tools can automate the monitoring of compliance requirements, thereby improving the organization’s ability to adapt to evolving cybersecurity laws and regulations. By leveraging AI, organizations can proactively identify and mitigate compliance risks before they escalate into security breaches.
What are the key components of an effective compliance solution?
An effective compliance solution should include comprehensive compliance tools, methods and processes for monitoring regulatory compliance, and ongoing compliance management capabilities. Additionally, it should enable organizations to assess their compliance status continuously and adapt to changes in security requirements, ensuring that they maintain a robust cybersecurity framework.
How can organizations ensure ongoing compliance in cybersecurity?
Organizations can ensure ongoing compliance by integrating compliance automation into their cybersecurity strategy. This involves using automated tools to continuously monitor compliance status, conduct regular compliance checks, and update security measures as needed. By establishing a culture of proactive compliance, organizations can effectively manage their cybersecurity risks and adapt to new regulatory compliance demands.
What are the future research directions in cybersecurity compliance automation?
Future research directions in cybersecurity compliance automation may focus on enhancing the capabilities of automation tools, integrating AI and machine learning for better predictive analytics, and developing frameworks for policy as code. Additionally, exploring the intersection of cloud security and compliance automation will be critical as organizations increasingly migrate to cloud-based environments.