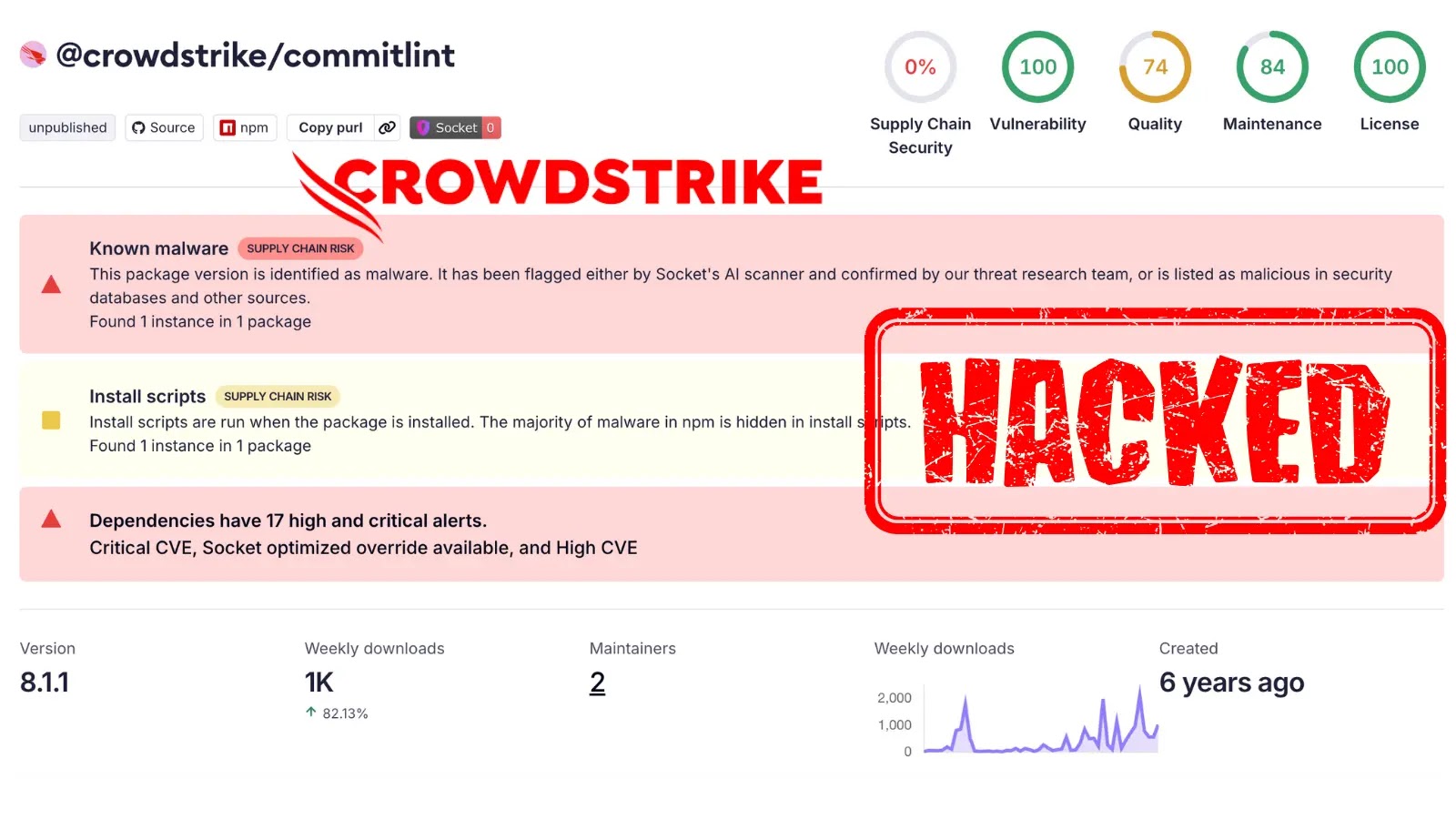
CrowdStrike npm Packages Compromised in Ongoing Supply Chain Attack
The digital supply chain, a critical lifeline for modern software development, has once again been targeted. A recent campaign, dubbed the “Shai-Halud attack,” has successfully compromised multiple npm packages published by cybersecurity giant CrowdStrike. This incident serves as a stark reminder of the persistent and evolving threat landscape within the open-source ecosystem, particularly for organizations reliant on third-party libraries and components.
Understanding the Shai-Halud Attack and npm Supply Chain Risk
The “Shai-Halud attack” is not a new adversary. This malicious campaign has a history of targeting popular npm packages, demonstrating a clear intent to inject malicious code into widely used software. The compromise of CrowdStrike’s npm packages underscores the attacker’s sophistication and reach, as even leading cybersecurity firms are not immune to these sophisticated supply chain threats.
npm, the world’s largest software registry, is a cornerstone of modern web development. Its sheer size and the interconnectedness of its packages make it an attractive target for attackers. A compromise within this ecosystem can have cascading effects, potentially injecting malware into countless applications downstream. This incident specifically highlights how threat actors exploit trust in widely adopted packages, turning them into vehicles for malicious payload delivery. The attack method appears to leverage similar tactics previously used to compromise the popular tinycolor package, suggesting a consistent and evolving methodology.
Impact on CrowdStrike and the Broader Ecosystem
While the full extent of the impact on CrowdStrike’s internal systems or customers is still being assessed, the immediate concern lies in the potential for malicious code injection into development pipelines. Developers using the compromised CrowdStrike npm packages could unknowingly integrate malware into their applications, leading to data breaches, system compromise, or other serious security incidents. The npm registry acted swiftly to address the compromise, a testament to the community’s commitment to maintaining the integrity of the open-source supply chain.
This incident also raises important questions about the security posture of developer tools and environments. Compromising npm packages is often just one step in a larger attack chain, aiming to establish persistent access or move laterally within targeted organizations. Developers and organizations must recognize that their reliance on open-source components necessitates a sophisticated approach to supply chain security.
Remediation Actions and Best Practices
Addressing supply chain compromises requires immediate action and a proactive security strategy. Organizations and developers impacted by this specific incident, or concerned about similar threats, should take the following steps:
- Audit Dependencies: Immediately audit all project dependencies to identify any usage of the compromised CrowdStrike npm packages. If identified, isolate and remove these dependencies.
- Update npm Packages: Ensure all npm packages are updated to the latest, officially sanctioned versions. Regularly check for security advisories and promptly apply patches.
- Implement Software Composition Analysis (SCA): Utilize SCA tools to automatically scan dependencies for known vulnerabilities, licenses, and potential supply chain risks.
- Incorporate Supply Chain Security Tools: Employ tools specifically designed to detect and prevent supply chain attacks. These can include integrity checks, artifact signing, and behavioral analysis of package installations.
- Enhance Developer Security Awareness: Educate developers on the risks associated with open-source dependencies, the importance of verifying package authenticity, and the dangers of suspicious package versions.
- Monitor npm Registry for Anomalies: Keep abreast of security alerts and advisories from the npm registry and cybersecurity news outlets.
- Implement Multi-Factor Authentication (MFA): Enforce MFA for all npm accounts and development platforms to prevent unauthorized access.
- Use Private npm Registries: For highly sensitive projects, consider using a private npm registry with strict access controls and vulnerability scanning capabilities.
Tools for npm Supply Chain Security
A robust security posture against npm supply chain attacks relies on a combination of practices and specialized tools. Here are some essential tools to consider:
| Tool Name | Purpose | Link |
|---|---|---|
| Snyk | Vulnerability scanning, dependency tracking, license compliance. | https://snyk.io |
| Dependabot | Automated dependency updates and vulnerability alerts (integrated with GitHub). | https://docs.github.com/en/code-security/dependabot/dependabot-security-updates/about-dependabot-security-updates |
| npm audit | Built-in npm command to scan project dependencies for known vulnerabilities. | https://docs.npmjs.com/cli/v9/commands/npm-audit |
| OWASP Dependency-Check | Identifies project dependencies and checks for known, publicly disclosed vulnerabilities. | https://owasp.org/www-project-dependency-check/ |
| Socket | Analyzes real-time package behavior and flags suspicious activities. | https://socket.dev |
Key Takeaways for a Resilient Supply Chain
The compromise of CrowdStrike’s npm packages by the “Shai-Halud attack” reinforces a critical lesson: supply chain security is paramount. Organizations must prioritize robust security practices for their open-source dependencies. This includes proactive vulnerability management, stringent dependency auditing, and the adoption of specialized tools. Continuous monitoring, prompt remediation, and a strong security culture are essential to mitigate the risks inherent in modern software development and to build genuinely resilient software supply chains.





