Why Network Segmentation is Critical For Cybersecurity.
Network Segmentation in Cybersecurity: What You Need to Know
In today’s interconnected world, where data breaches and cyber threats are ever-evolving, implementing effective network segmentation strategies is essential. network segmentation stands as a vital strategy to protect your organization’s digital assets. This comprehensive guide, presented by Teamwin Global Technologica, aims to elucidate the intricacies of network segmentation in cybersecurity. We are committed to empowering your enterprise by enhancing network performance and fortifying defenses against potential security breaches using network segmentation benefits. Dive into this essential knowledge to safeguard your organization’s integrity and ensure its success for tomorrow.
Understanding Network Segmentation
Definition of Network Segmentation
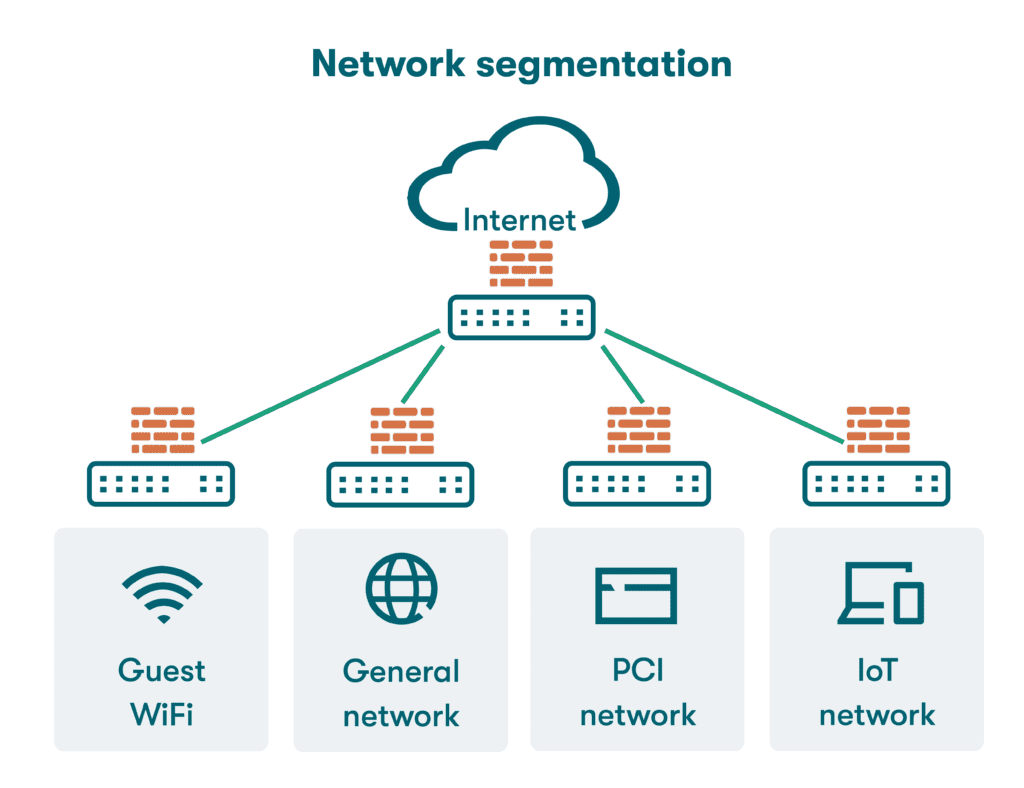
Network segmentation is a strategic approach to dividing a computer network into smaller, more manageable segments or zones. This technique enhances network security by establishing network boundaries and controlling the flow of network traffic. By segmenting a network, organizations can implement robust security policies that limit access to sensitive data and systems, thereby protecting the network perimeter. The segmentation can be achieved through various methods, including:
| Method is a critical component of network security that enhances protection within the network. | Description |
|---|---|
| Physical Segmentation | Using separate hardware |
| Logical Segmentation | Creating virtual local area networks (VLANs) within a single physical infrastructure helps in managing larger networks more effectively. |
Importance of Network Segmentation in Cybersecurity
In the realm of cybersecurity, network segmentation is crucial for maintaining a strong security posture. By isolating different parts of the network, organizations can prevent unauthorized access and mitigate the impact of potential cyber threats. This layer of security ensures that even if one segment is compromised, the entire network remains protected. With the rise of zero trust network models, segmentation strategies have become indispensable, reinforcing network boundaries and enhancing data security by limiting access to critical resources to only those who truly require it.
How Network Segmentation Improves Network Performance
Beyond enhancing security, network segmentation significantly improves network performance. By organizing a network into smaller segments, it reduces network congestion and optimizes the flow of data. This ensures that network traffic is efficiently managed, preventing bottlenecks that can slow down the entire network. In modern network architectures, segmentation policies play a pivotal role in streamlining operations and enhancing the overall efficiency of IT infrastructure. As a result, organizations not only safeguard their data but also enjoy a more responsive and reliable network environment.
Benefits of Network Segmentation
Enhanced Network Security
As a cornerstone of cybersecurity, Network segmentation offers a formidable layer of security that is crucial in today’s threat-laden digital environment, enhancing overall security.. Teamwin Global Technologica, known for its advanced security technologies, excels in implementing robust cybersecurity measures that ensure your enterprise’s safety. By segmenting your network, you establish clear network boundaries that prevent unauthorized access and limit the spread of potential threats inside the network. With specialized strategies in advanced cybersecurity and threat detection, we empower your organization to maintain a secure and resilient security posture.
Isolation of Network Breaches
One of the significant benefits of network segmentation is its ability to protect the network perimeter. isolate network breaches effectively. By dividing a network into smaller, distinct segments, any breach that occurs is confined to a specific part of the network, minimizing the risk of it spreading across the entire network. This strategic isolation not only protects sensitive data but also ensures that the functionality of the rest of the network remains uncompromised. Segmentation strategies are thus pivotal in maintaining the integrity of your network infrastructure and enhancing overall security.
Improved Data Security and Compliance
Network segmentation plays a vital role in enhancing data security and ensuring compliance with regulatory standards within the network. Teamwin Global Technologica provides comprehensive solutions that safeguard enterprise data and intellectual property through effective network addressing. Our Cloud Security & Regulatory Assurance services are designed to meet necessary compliance standards, offering peace of mind that your data is protected and compliant. By implementing data protection measures through IT Security & Firewalls, we ensure that your organization not only meets but exceeds industry requirements, reinforcing trust and reliability in your operations.
Types of Network Segmentation
Physical Segmentation
Physical segmentation involves the use of separate hardware devices to create distinct network segments, ensuring robust network security. This method physically isolates parts of the network to prevent unauthorized access. By implementing physical barriers, organizations can enforce stringent security policies and establish clear network boundaries.
| Segmented Network Parts | Purpose |
|---|---|
| Sensitive data centers | Prevent unauthorized access inside the network perimeter. |
| Critical infrastructure within a flat network can be particularly vulnerable to attacks. | Enhance data security and performance using network segmentation strategies that break a large network into smaller subnetworks. |
This traditional segmentation approach is particularly effective in safeguarding sensitive areas of the network.
Logical Segmentation
Logical segmentation, often achieved through the creation of virtual local area networks (VLANs), allows organizations to divide their network into smaller, manageable segments without the need for additional hardware. This strategy is integral in modern network architectures, enabling the implementation of flexible and dynamic security policies. By logically segmenting the network, businesses can control network traffic and minimize network congestion, ensuring efficient data flow and improved network performance inside the network perimeter. This approach supports the zero trust network model by isolating network zones and protecting the internal network from potential threats.
Virtual Segmentation
Virtual segmentation leverages advanced technologies, such as virtual machines and software-defined networking, to create segmented networks within a single physical infrastructure. This form of segmentation provides a scalable and cost-effective solution for organizations seeking to enhance their network security posture. By adopting virtual segmentation strategies, businesses can dynamically manage network access control and swiftly respond to emerging cyber threats. This approach not only fortifies the network perimeter but also optimizes resource allocation, ensuring seamless network operations and robust security defenses.
Segmentation Strategies
Implementing Network Segmentation
Implementing network segmentation requires a strategic approach that considers both security requirements and protecting the network perimeter. operational efficiency. Organizations must assess their network architecture to identify critical assets and potential vulnerabilities in their internal network or cloud environment. By defining clear segmentation policies, businesses can segment their networks into smaller zones, each with tailored security measures. This process involves collaboration between IT security teams and network administrators to ensure seamless integration and minimal disruption. With effective implementation, network segmentation becomes a powerful tool in the arsenal against cybersecurity threats.
Best Practices for Effective Segmentation
To maximize the benefits of network segmentation, organizations should adhere to best practices that reinforce network security and performance. Regularly reviewing and updating network segmentation strategies is crucial to address evolving threats and technological advancements. Additionally, incorporating comprehensive monitoring and threat detection mechanisms ensures timely identification of potential breaches. Organizations should also prioritize employee training to raise awareness about security protocols and foster a culture of cybersecurity. By following these best practices, businesses can maintain a resilient and secure network environment.
Common Challenges and Solutions
While network segmentation offers numerous benefits, organizations may encounter challenges during its implementation. Complex network infrastructures can complicate the segmentation process, requiring careful planning and coordination. Additionally, maintaining a balance between security and usability can be difficult, as excessive segmentation might hinder operational efficiency. To overcome these challenges, organizations must develop effective segmentation strategies that define clear boundaries within the network. businesses should employ advanced security solutions that provide visibility and control over segmented networks. By adopting a proactive approach, organizations can effectively manage the complexities of segmentation and fortify their defenses against cyber threats.
Network Segmentation Use Cases
Case Study: Enterprise Networks
In enterprise networks, Network segmentation is pivotal in maintaining a robust security posture within a flat network.. Organizations often face challenges related to network congestion and unauthorized access to sensitive areas. By segmenting the network into smaller zones, businesses can implement specific security policies tailored to each segment, optimizing overall security. This strategy not only enhances network security by controlling network traffic but also optimizes network performance, ensuring efficient operations across the entire network. Enterprises that have adopted segmentation strategies report improved data security and a significant reduction in downtime.
Case Study: Cloud Environments
Cloud environments present unique challenges and opportunities for network segmentation. The dynamic nature of cloud infrastructures necessitates agile segmentation policies that can adapt to changing network architecture. By employing logical segmentation through virtual local area networks, cloud service providers can isolate different parts of the network, ensuring data security and compliance with security standards. This approach enhances the reliability and security of cloud services, allowing organizations to leverage the benefits of cloud computing without compromising on security.
Case Study: IoT Devices
The proliferation of IoT devices has introduced new vulnerabilities within network infrastructures. Network segmentation offers a critical layer of security by isolating IoT devices into distinct network zones, thereby preventing security breaches from spreading across the internal network. Segmentation strategies in IoT environments focus on defining network boundaries and controlling network access. This ensures that any compromise remains confined to a specific segment, safeguarding the integrity and performance of the entire network, which is a key aspect of segmentation helps.
5 Surprising Facts About Why Network Segmentation is Critical for Cybersecurity
- Network segmentation can reduce the attack surface by up to 85%, limiting the number of entry points for cybercriminals.
- Organizations that implement network segmentation are 50% less likely to experience data breaches compared to those that do not.
- Proper segmentation can help organizations comply with regulatory requirements, such as PCI DSS, HIPAA, and GDPR, by controlling data access.
- In the event of a breach, network segmentation can help contain the threat, preventing lateral movement within the network and minimizing damage.
- Segmentation not only enhances security but also improves network performance by reducing congestion and optimizing traffic flow.
What is the role of network segmentation in cybersecurity?
Network segmentation plays a crucial role in cybersecurity by establishing distinct network boundaries that prevent unauthorized access and contain potential breaches. By dividing a network into smaller, manageable segments, organizations can implement robust security policies tailored to specific needs. This layer of security is essential in protecting sensitive data and maintaining a strong security posture, especially when dealing with larger networks. Network segmentation in cybersecurity is foundational in defending against evolving cyber threats, ensuring that even if one network segment is compromised, the entire network remains secure and can contain issues laterally within the network.
How does network segmentation affect network performance?
Network segmentation significantly enhances network performance by reducing network congestion and optimizing data flow. By organizing a network into smaller segments, organizations can efficiently manage network traffic, preventing bottlenecks that can slow down operations. Segmentation policies are designed to streamline network performance, ensuring that resources are allocated effectively and that the network operates at peak efficiency. This not only improves the user experience but also supports the reliable and responsive functioning of IT infrastructure.
What are the key benefits of implementing network segmentation?
Implementing network segmentation offers several key benefits, including enhanced network security, improved data security, and better compliance with regulatory standards. By segmenting the network, organizations can isolate potential threats, preventing them from spreading across the entire network.
| Benefits | Details |
|---|---|
| Network Performance | Optimizes network performance, reducing congestion and improving the speed and reliability of network operations inside the network. |
| Security Policies | Ensures that security policies are consistently applied, reinforcing the organization’s security posture and providing peace of mind against cyber threats. |
Why is network segmentation important for cybersecurity?
Network segmentation is critical for cybersecurity as it involves dividing a larger network into smaller subnetworks, making it harder for attackers to reach critical systems. By isolating sensitive data and resources, organizations can significantly enhance their security posture, ensuring that a breach in one segment does not compromise the entire network.
What are the benefits of network segmentation?
Segmentation improves security by limiting lateral movement across the network. This means that even if an attacker gains access to one segment, they cannot easily access other parts of the network. Additionally, segmentation reduces the attack surface and allows for more tailored security policies for different segments.
What types of network segmentation are commonly used?
There are various types of network segmentation, including physical segmentation, logical segmentation, and virtual segmentation. Physical segmentation involves separate hardware for different segments, while logical segmentation uses software to create virtual networks within the existing infrastructure.
How does network segmentation reduce the risk of cyberattacks?
By implementing network segmentation, organizations can create barriers that thwart attackers, making it more difficult for them to move across the network. This strategy for network security helps to contain any potential breaches and minimizes the impact of attacks, protecting critical systems and data.
Can segmentation be used for testing purposes?
Yes, network segments for testing allow organizations to safely evaluate new systems or updates without risking the entire corporate data network. This isolated environment ensures that any vulnerabilities can be identified and addressed without exposure to the broader network.
How does a guest wireless network fit into network segmentation?
A guest wireless network is an example of network segmentation that provides internet access for visitors while isolating them from the corporate data network. This prevents unauthorized access to sensitive information and ensures that guests cannot interact with internal systems.
What strategies can be implemented for effective network segmentation?
Effective segmentation strategies include using firewalls to control traffic between segments, implementing access control lists (ACLs), and employing virtual LANs (VLANs) to separate traffic logically. These measures enhance data security and improve overall network performance.
How does network segmentation improve security against widespread cyberattacks?
Network segmentation helps organizations defend against widespread cyberattacks by limiting the potential damage of a successful breach. When a network is compromised, segmentation ensures that only the affected segment is at risk, protecting other vital areas of the network and reducing the overall impact of the attack.
What is the role of network segmentation in data security?
Network segmentation plays a vital role in data security by controlling access to sensitive information and ensuring that only authorized users can interact with critical systems. By implementing segmentation, organizations can better manage data flow and protect against unauthorized access.