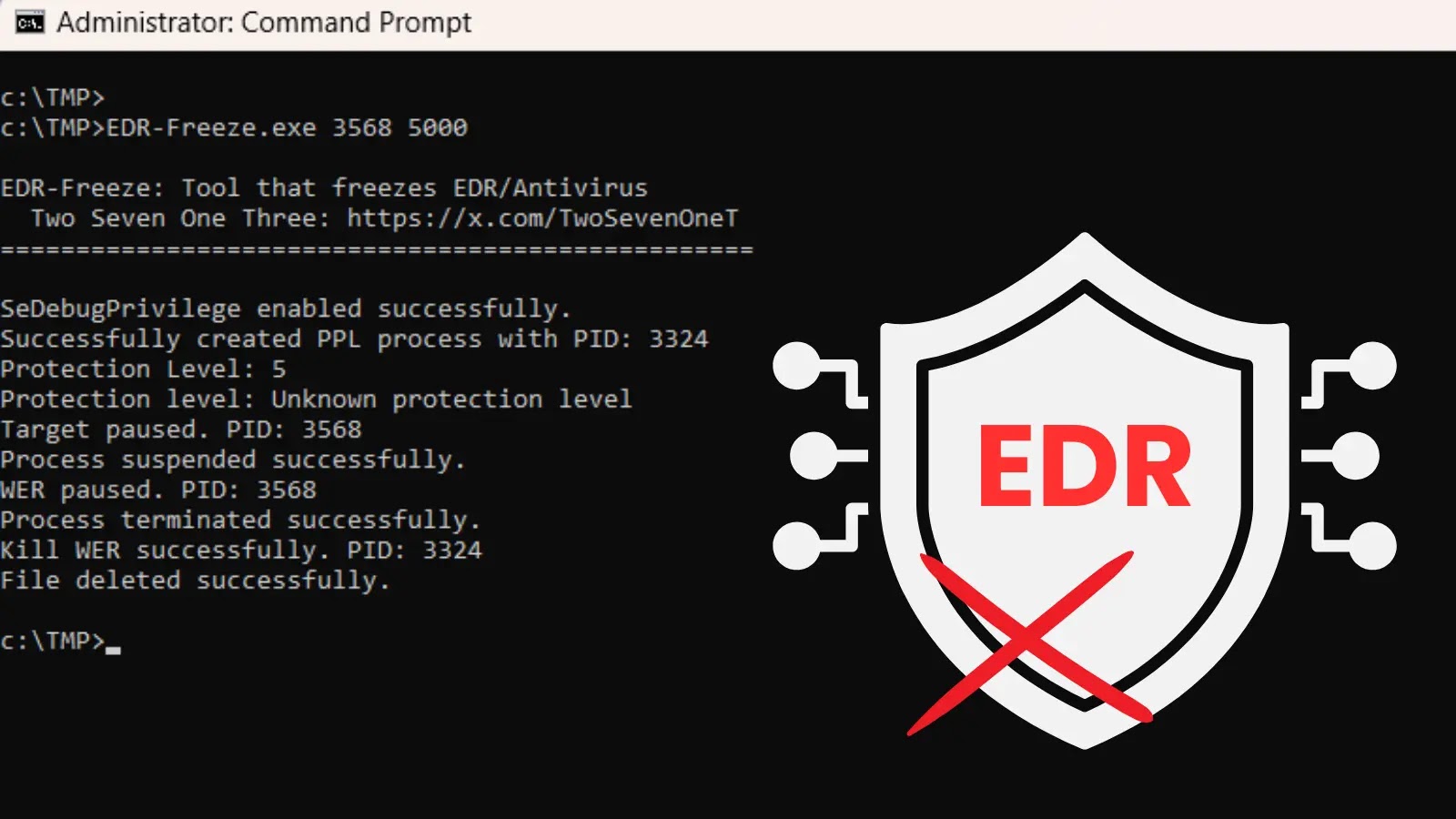
New EDR-Freeze Tool That Puts EDRs and Antivirus Into A Coma State
The Silent Assassin: EDR-Freeze Puts Security Tools into a Coma
Endpoint Detection and Response (EDR) solutions and traditional antivirus programs are the frontline defenders of modern digital environments. They tirelessly monitor for malicious activity, acting as the digital immune system for countless organizations. But what happens when these crucial defenses are, quite literally, put to sleep? A new proof-of-concept tool, dubbed EDR-Freeze, has emerged, demonstrating an alarming capability: rendering EDR and antivirus solutions inert, effectively placing them into a suspended “coma” state. This development signals a concerning shift in attacker tactics, offering a stealthier alternative to previous bypass methods and demanding immediate attention from cybersecurity professionals.
Understanding EDR-Freeze: A Stealthy New Evasion Technique
Developed by Zero Salarium, EDR-Freeze doesn’t rely on the increasingly common “Bring Your Own Vulnerable Driver” (BYOVD) attacks, which exploit known flaws in legitimate drivers to gain privileged access. Instead, EDR-Freeze leverages a built-in Windows kernel function. This approach is particularly troublesome because it utilizes legitimate operating system functionality, making its actions inherently more difficult for security tools to detect and flag as malicious. By exploiting this function, attackers can effectively pause or suspend critical processes associated with EDR and antivirus agents, silencing their monitoring capabilities without immediate detection.
How EDR-Freeze Operates: The “Coma” State
When EDR-Freeze is deployed, it doesn’t crash or outright disable security software. Instead, it places these applications into a state akin to a deep sleep. During this “coma,” the EDR or antivirus agent is still technically running in memory, but its active monitoring, detection, and response capabilities are suspended. This means that while a malicious payload might be executing, or sensitive data is being exfiltrated, the compromised security solutions remain oblivious, unable to report or block the ongoing threats. This stealth bypass offers attackers a golden window of opportunity, allowing them to operate unimpeded within a compromised system.
The Evolution of Evasion: Beyond BYOVD
For some time, threat actors have favored BYOVD techniques due to their effectiveness in bypassing security controls. These methods exploit vulnerabilities in signed, legitimate kernel drivers to execute malicious code with elevated privileges. While still a significant threat, BYOVD attacks often leave more forensic artifacts, as the vulnerable driver’s execution can be logged or detected. EDR-Freeze, by contrast, operates on a different plane, utilizing inherent Windows system calls. This makes it a potentially harder threat to trace and remediate, as it blends in more seamlessly with normal system operations. This shift indicates a continuous cat-and-mouse game between defenders and attackers, with each new defense prompting a more sophisticated evasion technique.
Remediation Actions and Defensive Strategies
The emergence of EDR-Freeze necessitates a re-evaluation of current defensive postures. Organizations must go beyond traditional signature-based detection and invest in more granular behavioral analysis and system integrity monitoring. Here are key remediation actions:
- Enhanced Process Monitoring: Implement advanced process monitoring to detect unusual suspension or modification of legitimate security agent processes. Focus on deviations from baseline behavior rather than just known malicious signatures.
- Kernel-Level Visibility: Invest in security solutions that provide deep kernel-level visibility, capable of monitoring system calls and kernel functions for suspicious activity, even if those functions are legitimate.
- Integrity Checks for Security Agents: Regularly monitor the integrity and operational status of EDR and antivirus agents. Implement automated checks that can detect if a security process is running but not actively performing its duties (e.g., no recent logs, no active scans, suspended threads).
- Zero-Trust Architecture: Reinforce a Zero-Trust approach. Assume compromise is inevitable and apply least privilege principles to all users and applications. Segment networks and restrict lateral movement to limit the impact of a successful EDR bypass.
- Threat Hunting: Proactively hunt for indicators of compromise (IOCs) that might signify an EDR-Freeze attack, even if EDR alerts are silent. Look for unusual network connections, persistent administrative tool usage, or unexplainable process states.
- Regular Patching and Updates: While EDR-Freeze relies on a built-in Windows function rather than a traditional vulnerability, keeping all systems, including EDR and antivirus software, fully patched and updated is always a fundamental defense.
The Path Forward: Adapting to New Evasion Tactics
The EDR-Freeze tool underscores the critical need for adaptability in cybersecurity. Relying solely on a single layer of defense is no longer sufficient. Attackers are constantly innovating, and their techniques are becoming increasingly subtle. Organizations must foster a multi-layered security strategy, combining robust EDR capabilities with proactive threat hunting, granular system monitoring, and a strong adherence to Zero-Trust principles. The ability to detect and respond to sophisticated evasions like EDR-Freeze will determine the resilience of modern enterprises against persistent and evolving threats.





