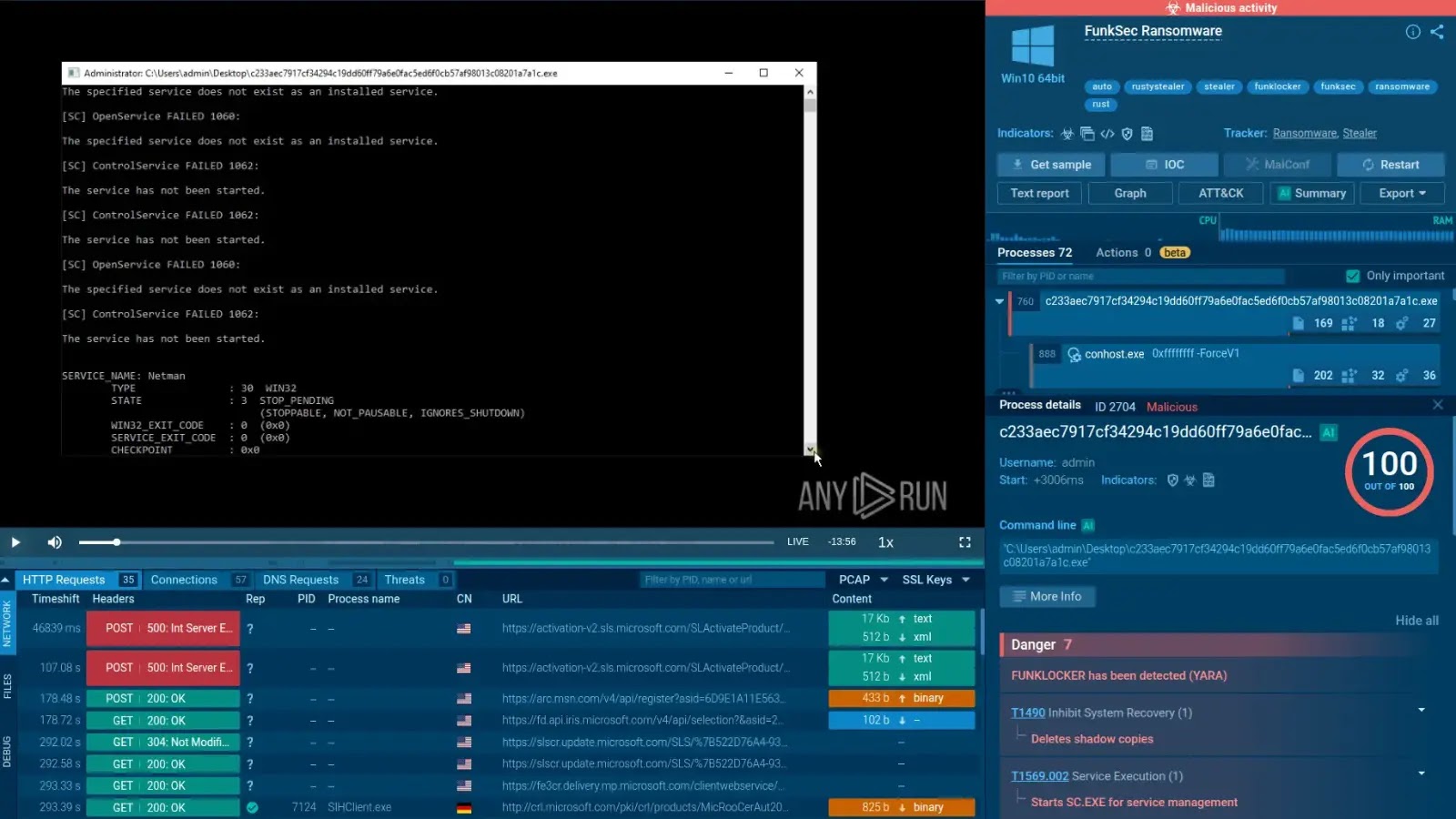
AI-Powered FunkLocker Ransomware Leverages Windows utilities to Disable Defenses
The cybersecurity landscape faces an accelerating threat: AI-powered ransomware. A new strain, dubbed FunkLocker, exemplifies this dangerous evolution, not only by leveraging artificial intelligence to expedite its development but also by exploiting legitimate Windows utilities to dismantle an organization’s defenses and disrupt critical systems. This sophisticated attack vector, attributed to the FunkSec group, underscores a critical shift in how threat actors craft and deploy their malicious payloads.
Understanding FunkLocker: AI-Powered Ransomware
FunkLocker distinguishes itself through its reported use of artificial intelligence in its initial development phases. While the specific AI methodologies remain under investigation, this trend points towards a future where malware generation becomes increasingly automated and adaptable. The implications are profound: faster iteration cycles for ransomware, more effective evasion techniques, and a lower barrier to entry for threat actors.
Unlike many traditional ransomware variants that rely solely on custom malicious code, FunkLocker reportedly integrates AI to enhance various stages of its lifecycle. This could include automating code generation, improving obfuscation techniques, or even optimizing target selection based on network reconnaissance data. The objective is clear: create a more resilient, stealthy, and damaging ransomware package.
Abusing Windows Utilities: A Stealthy Approach
A key operational tactic of FunkLocker is its reliance on legitimate, built-in Windows utilities to disable security mechanisms and achieve its objectives. This technique, often referred to as “living off the land” (LotL), allows the ransomware to operate with a reduced footprint, making it more challenging for traditional endpoint detection and response (EDR) solutions to identify and block.
Threat actors frequently abuse tools like PowerShell, PsExec, WMIC, and others to:
- Disable Security Software: Using administrative privileges obtained through various means, FunkLocker can execute commands to stop security services, modify firewall rules, or even uninstall security products.
- Evade Detection: By leveraging trusted Windows processes, the ransomware can blend in with legitimate system activity, making behavioral analysis more difficult.
- Lateral Movement: Utilities like PsExec can be used to move within a network, spread the ransomware to other systems, and increase the scope of compromise.
- Data Exfiltration: While not explicitly stated for FunkLocker in the source, threat actors frequently utilize built-in tools for data staging and exfiltration prior to encryption.
Remediation Actions and Proactive Defense
Mitigating the threat posed by FunkLocker and similar AI-powered, LotL-abusing ransomware requires a multi-layered and proactive defense strategy. Organizations must move beyond signature-based detection and prioritize robust behavioral analysis, privilege management, and employee education.
- Implement Principle of Least Privilege: Restrict user and service account permissions to only what is absolutely necessary. This limits the damage an attacker can inflict even if they compromise an account.
- Enhance Endpoint Detection and Response (EDR): Deploy EDR solutions capable of advanced behavioral analysis to detect anomalous activity, even when legitimate tools are being misused. Focus on detecting command-line tool abuse and unusual process trees.
- Monitor and Audit Administrative Tools: Scrutinize the usage of PowerShell, Task Scheduler, WMI, and other administrative utilities. Implement logging and alerting for unusual execution patterns or commands.
- Regularly Back Up Data: Maintain immutable, off-site backups of all critical data. Test restoration procedures regularly to ensure business continuity in the event of a successful ransomware attack.
- Segment Networks: Isolate critical systems and data with network segmentation. This limits lateral movement and prevents ransomware from spreading rapidly across the entire infrastructure.
- Implement User Awareness Training: Educate employees on phishing, social engineering, and the importance of strong, unique passwords. Many ransomware attacks begin with initial access gained through human error.
- Patch and Update Systems: Keep all operating systems, applications, and security software fully patched and updated to address known vulnerabilities that attackers might exploit for initial access or privilege escalation.
- Review and Harden Security Configurations: Follow security best practices for hardening Windows systems, such as disabling unnecessary services, implementing account lockout policies, and enabling advanced audit policies.
Recommended Security Tools
To aid in the detection, scanning, and mitigation of threats like FunkLocker, consider leveraging the following types of tools:
| Tool Name | Purpose | Link |
|---|---|---|
| Osquery | Endpoint visibility and behavioral monitoring. | https://osquery.io/ |
| Sysmon | Advanced Windows system activity monitoring. | https://learn.microsoft.com/en-us/sysinternals/downloads/sysmon |
| Mandiant Commando VM | Penetration testing and red teaming for offensive security assessments. | https://github.com/mandiant/commando-vm |
| Microsoft Defender for Endpoint | Comprehensive EDR and threat intelligence. | https://www.microsoft.com/en-us/security/business/microsoft-defender-for-endpoint |
| Varonis Data Security Platform | Data visibility, threat detection, and user behavior analytics. | https://www.varonis.com/products/data-security-platform |
Conclusion
The emergence of AI-powered ransomware like FunkLocker, with its dual threat of artificial intelligence for accelerated development and “living off the land” tactics, signals a significant escalation in cybersecurity challenges. Organizations must recognize the sophisticated nature of these attacks and move towards adaptive, behavioral-based security strategies. Prioritizing robust EDR, stringent privilege management, continuous monitoring of legitimate tools, and comprehensive backup solutions are no longer optional but essential safeguards against these evolving threats.





