New AmCache EvilHunter Tool For Detecting Malicious Activities in Windows Systems
Unmasking Malice: Introducing AmCache EvilHunter for Windows System Forensics
In the relentless battle against cyber threats, understanding system activity is paramount. Malicious actors constantly devise new ways to hide their tracks, making robust forensic tools indispensable for cybersecurity professionals. This is where AmCache EvilHunter emerges as a critical utility, providing an unprecedented view into Windows system execution history, even when malware attempts to self-delete and vanish without a trace.
The AmCache database, a core component of Windows, serves as a vital repository of executed program information. Its inherent resilience and tamper-proof nature make it a goldmine for incident responders and threat hunters. AmCache EvilHunter leverages this strength, offering security analysts a powerful new ally in detecting and investigating malicious activities.
The Power of AmCache: A Digital Fingerprint of Execution
Windows systems meticulously record details about executed applications in the AmCache database. This crucial data includes file paths, execution times, and, most importantly, SHA-1 hashes of the executed binaries. These hashes act as unique digital fingerprints, allowing for precise identification of both legitimate and malicious software that has run on a machine.
What makes AmCache particularly valuable in cybersecurity forensics is its persistence. Managed directly by the operating system, AmCache data is notoriously difficult to alter or erase by malicious software. Even if malware executes, performs its nefarious tasks, and then attempts to cover its tracks by self-deleting, the AmCache record often remains, providing irrefutable evidence of its presence and activity.
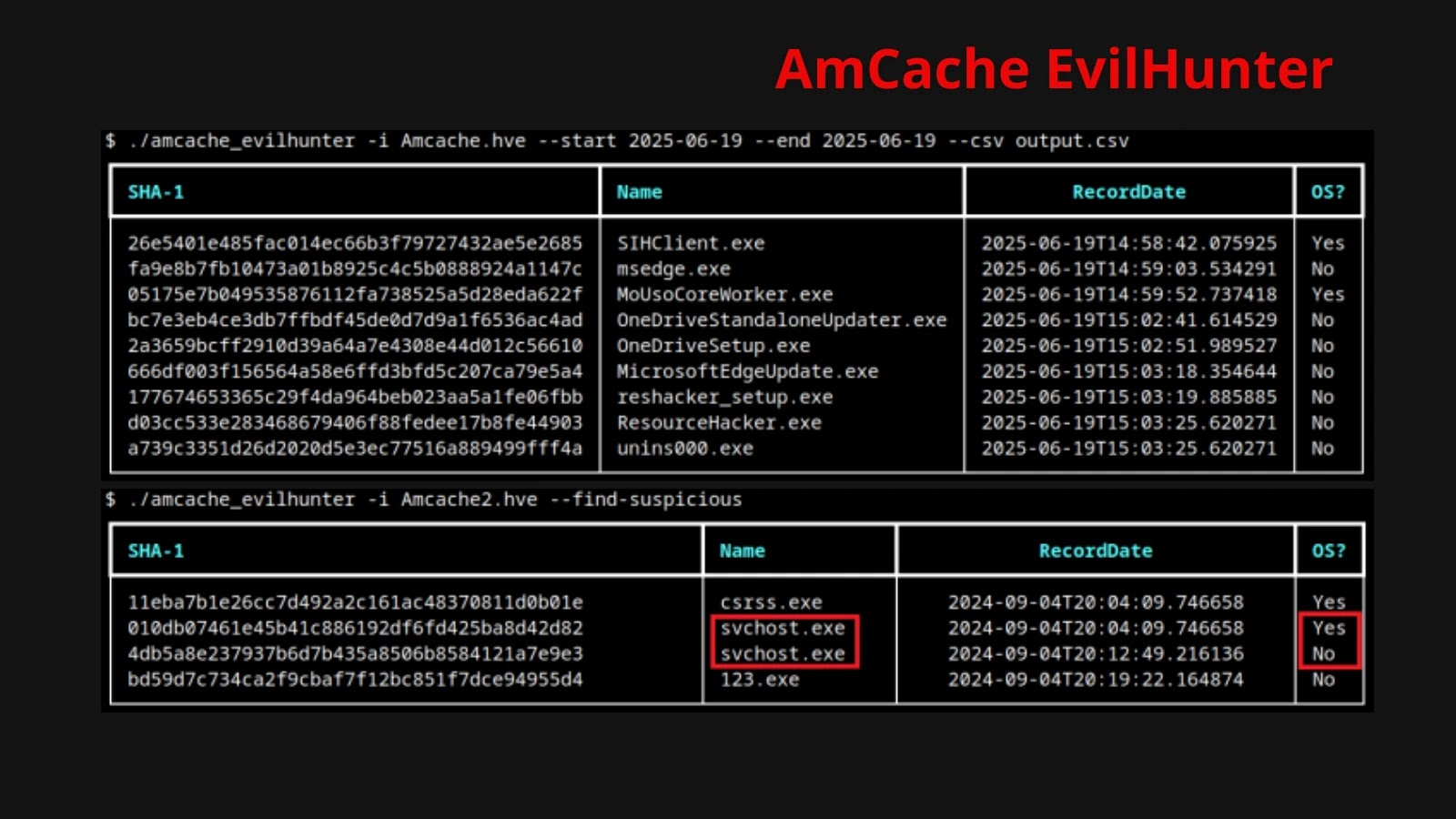
Introducing AmCache EvilHunter: Enhancing Detection Capabilities
Designed to extract and analyze this invaluable AmCache data, the new AmCache EvilHunter tool significantly enhances the ability of security teams to detect and investigate suspicious activity. By parsing the stored SHA-1 hashes and associated data, investigators can quickly identify unknown or suspicious executables that have run on a system. This allows for:
- Identification of Unauthorized Software: Quickly pinpoint applications that shouldn’t be present or running on a corporate network.
- Malware Tracing: Even if a malware sample is no longer on the disk, its execution record in AmCache can reveal its presence and execution history.
- Incident Response Acceleration: Expedite the initial stages of incident response by providing a clear timeline of executed programs, aiding in containment and eradication efforts.
- Proactive Threat Hunting: Integrate AmCache EvilHunter into routine threat hunting operations to proactively search for indicators of compromise (IOCs) based on execution patterns.
Understanding AmCache Data Structure for Forensic Analysis
While the internal structure of AmCache can seem complex, AmCache EvilHunter simplifies the extraction and interpretation process. Fundamentally, AmCache records metadata about program execution, including:
- Program Name and Path: The full path to the executed file.
- Execution Timestamps: When the program was first executed and the last time it ran.
- File Size: The size of the executable.
- SHA-1 Hash: A unique cryptographic hash of the executable’s content. This hash is crucial for comparing against threat intelligence feeds.
The immutability of these records, particularly the SHA-1 hashes, prevents attackers from simply renaming or moving a malicious file to evade detection. The hash remains constant, offering a reliable beacon for detection.
Remediation Actions and Proactive Security Measures
The insights gained from AmCache data and tools like EvilHunter are invaluable for both reactive incident response and proactive security posture improvement. Once malicious activity is identified, several remediation actions and preventative measures should be taken:
- Isolate Affected Systems: Immediately disconnect any identified compromised systems from the network to prevent further lateral movement or data exfiltration.
- Malware Analysis: If a suspicious SHA-1 hash is found, obtain the corresponding binary (if possible) and perform static and dynamic analysis to understand its capabilities and indicators of compromise (IOCs).
- Endpoint Detection and Response (EDR) Review: Enhance EDR rules and alerts based on the newly discovered IOCs from AmCache analysis. Ensure your EDR solution is configured to detect and block similar execution patterns.
- Patch Management: Verify that all systems are running the latest security patches. Many exploits leverage known vulnerabilities, such as a recent example, CVE-2023-38183, which could be exploited for privilege escalation.
- User Training: Reinforce security awareness training to educate users about phishing, social engineering, and safe browsing practices that often lead to initial compromises.
- Application Whitelisting: Implement application whitelisting policies to prevent unauthorized software from executing on critical systems. This can significantly reduce the attack surface.
| Tool Name | Purpose | Link |
|---|---|---|
| AmCache EvilHunter | Extracts and analyzes AmCache data for forensic investigation | Cyber Security News Article |
| Mandiant Redline | Endpoint security analysis and compromise assessment | Mandiant Redline |
| Sysinternals Autoruns | Identifies programs configured to run during system startup | Microsoft Sysinternals |
Conclusion: Strengthening Your Defensive Posture
The AmCache EvilHunter tool represents a significant advancement in forensic capabilities for Windows systems. By leveraging the resilient and detailed execution records within the AmCache database, security analysts gain a powerful new mechanism for identifying malicious activity, even in the face of sophisticated evasion techniques. Integrating tools like AmCache EvilHunter into your security operations framework not only aids in rapid incident response but also strengthens your overall defensive posture through enhanced visibility and actionable intelligence. Staying ahead of attackers requires innovative tools and a deep understanding of system forensics; AmCache EvilHunter provides a crucial piece of this puzzle for any cybersecurity professional.





