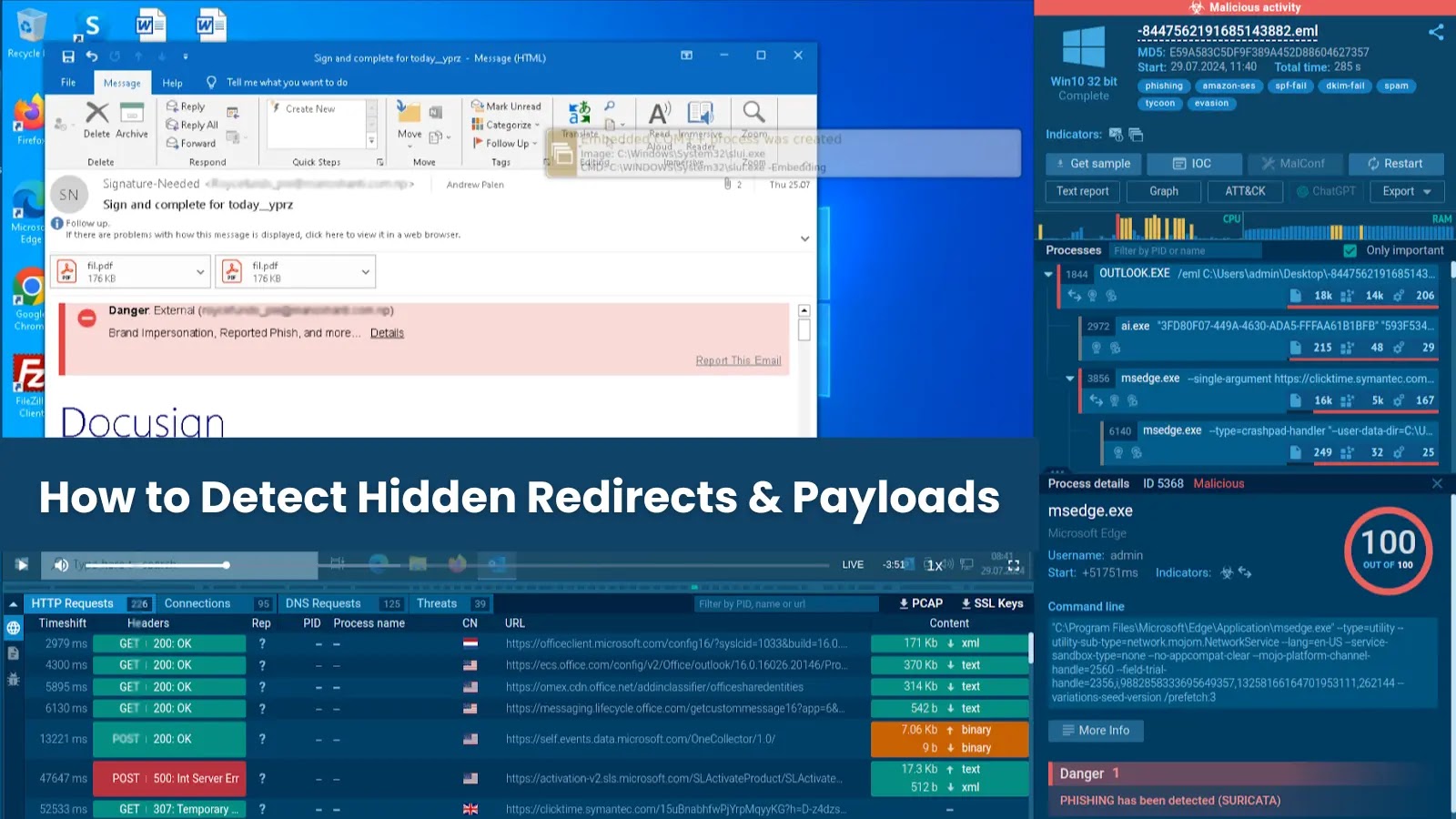
Malicious SVGs in Phishing Campaigns: How to Detect Hidden Redirects and Payloads
Phishing campaigns are constantly evolving, pushing the boundaries of what security professionals consider a threat vector. What if the very files you deemed harmless could harbor sophisticated attacks? Recently, cybersecurity analysts at ANY.RUN uncovered a disturbing trend: malicious Scalable Vector Graphics (SVGs) masquerading as benign documents, designed to redirect users to malicious payloads. This isn’t just an isolated incident; by mid-September, these tactics had escalated into a full-blown spam wave, leveraging Microsoft-themed lures to ensnare unsuspecting victims. Understanding this subtle but dangerous attack vector is crucial for bolstering your defenses against modern phishing.
The Devious Disguise: Malicious SVGs in Phishing
The core of this threat lies in the deceptive nature of SVG files. SVGs are XML-based vector image formats, meaning they contain code (like JavaScript) that can be executed by a browser. This inherent capability, while useful for interactive graphics, becomes a significant security vulnerability when wielded by malicious actors. In the observed campaigns, these malicious SVGs were often disguised as PDF documents, a common tactic to bypass initial scrutiny. The file extension might still appear as .svg, but the visual cues and social engineering lure it was bundled with convinced victims otherwise.
One of the primary dangers of these malicious SVGs is their ability to host hidden redirects. These redirects, often embedded within the SVG’s XML structure, can silently whisk users away from a seemingly legitimate page to a phishing site, a malware download, or a credential harvesting portal. The use of legitimate domains to host these SVGs further enhances their credibility, making them harder for traditional security measures to flag.
Anatomy of a Malicious SVG Attack
The journey of a malicious SVG attack typically unfolds as follows:
- Initial Lure: Victims receive a phishing email, often impersonating a trusted entity like Microsoft, a financial institution, or a shipping company. The email might contain a link or an attachment that appears to be a crucial document.
- Deceptive Hosting: The malicious SVG is hosted on a compromised or legitimate domain, lending an air of trustworthiness to the link or download.
- Disguise and Delivery: The SVG is often disguised visually as a PDF or another common document type, encouraging the user to open it.
- Hidden Redirect: Upon opening the SVG in a web browser, embedded JavaScript or other XML functionalities execute a hidden redirect. This silently navigates the user’s browser to a malicious webpage.
- Payload Delivery: The redirected page could be a fake login portal designed to steal credentials, a drive-by download site for malware, or a page requesting sensitive personal information.
The sophistication lies in the seamless transition. The user experiences what appears to be a minor glitch or loading error, only to find themselves on a malicious site without explicit interaction.
Detecting Hidden Redirects and Payloads
Detecting malicious SVGs requires a multi-layered approach, combining user awareness with robust technical controls. Here’s how security teams and individuals can identify and mitigate this threat:
- Inspect File Extensions Carefully: Always scrutinize file extensions, even if the icon appears familiar. A file named “document.pdf.svg” is still an SVG.
- Sandbox Analysis: Utilize sandbox environments (like ANY.RUN, mentioned in the source material) to safely open and analyze suspicious files. Sandboxes execute the file in an isolated environment, revealing its true behavior, including any hidden redirects or payload drops.
- Static Code Analysis: For suspected SVG files, open them in a text editor. Look for suspicious JavaScript tags (
<script>), base64 encoded data, or unusual external references. Malicious scripts often attempt to obfuscate their true purpose. - Network Traffic Monitoring: Monitor network traffic for unusual outbound connections after opening a seemingly benign file. Unexpected requests to unfamiliar domains could indicate a hidden redirect.
- Email Security Gateways: Implement advanced email security gateways that can scan attachments for malicious code, including within SVG files, and flag suspicious links.
- Browser Security Features: Enable and configure browser security settings to block pop-ups and warn about suspicious redirects.
Remediation Actions
Once a malicious SVG attack is identified, swift remediation is critical to limit its impact:
- Isolate Affected Machines: Immediately disconnect any compromised systems from the network to prevent further spread of malware or data exfiltration.
- Credential Reset: If credentials were entered on a phishing page, force a password reset for all affected accounts, especially for critical services. Enable multi-factor authentication (MFA) if not already in use.
- Scan and Clean: Perform a thorough anti-malware scan on infected systems to identify and remove any installed payloads.
- Incident Response: Initiate your organization’s incident response plan. Document the attack vector, scope, and all remediation steps.
- User Education: Conduct immediate training refreshers for users on recognizing phishing attempts, inspecting file extensions, and the dangers of opening unsolicited attachments or clicking suspicious links. Emphasize the specific threat of disguised files.
- Update Security Software: Ensure all antivirus, anti-malware, and endpoint detection and response (EDR) solutions are updated with the latest threat intelligence.
Tools for Detection and Analysis
Leveraging the right tools can significantly enhance your ability to detect and analyze malicious SVGs.
| Tool Name | Purpose | Link |
|---|---|---|
| ANY.RUN | Interactive online sandbox for malware analysis, including file execution and network activity monitoring. | https://any.run/ |
| Virustotal | Aggregates results from multiple antivirus engines and file analysis tools. Useful for initial file scanning. | https://www.virustotal.com/gui/home/upload |
| Text Editor (e.g., Notepad++, VS Code) | Manual static analysis of SVG source code to detect embedded scripts or suspicious elements. | |
| Wireshark | Network protocol analyzer to capture and inspect network traffic for suspicious egress connections or redirects. | https://www.wireshark.org/ |
Staying Ahead of the Curve
The evolution of phishing attacks, particularly the use of seemingly innocuous files like SVGs, underscores the need for continuous vigilance and adaptive security strategies. Attackers will relentlessly seek new avenues to exploit trust and bypass defenses. By understanding the mechanics of these sophisticated campaigns, implementing robust technical controls, and fostering a security-conscious culture, organizations can significantly reduce their risk exposure to these increasingly prevalent threats.





