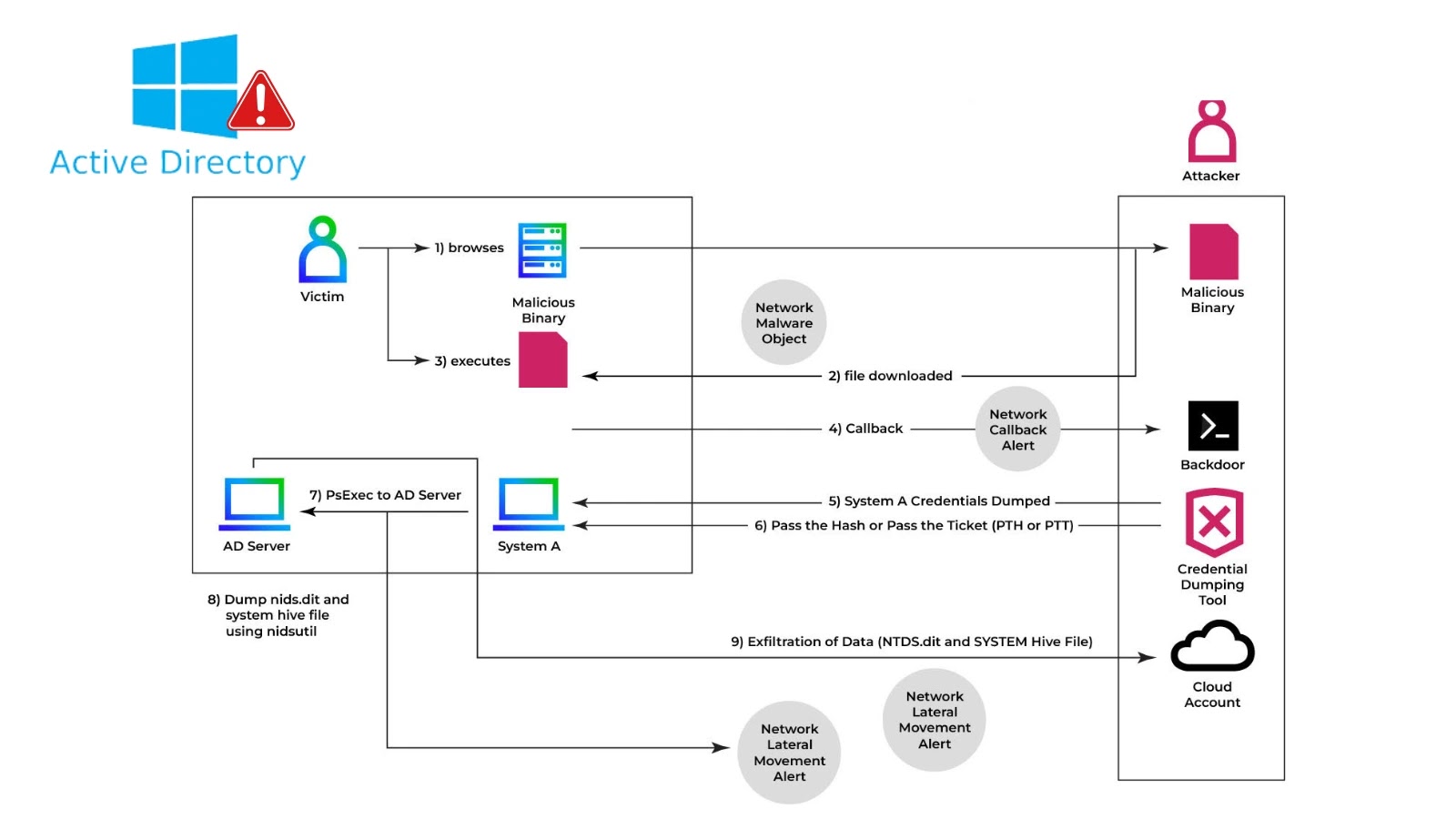
Hackers Compromise Active Directory to Steal NTDS.dit Exfiltration that Leads to Full Domain Compromise
Active Directory (AD) underpins the security and functionality of nearly every Windows-based enterprise environment. It’s the gatekeeper, arbitrator, and central repository for user identities, machine configurations, and access permissions. When AD is compromised, the entire organization is at risk. Recently, a critical breach leveraged sophisticated techniques to compromise Active Directory, specifically targeting the NTDS.dit database, leading to full domain compromise and unauthorized data exfiltration. This incident serves as a stark reminder of the persistent and evolving threats facing modern IT infrastructure.
The Critical Role of Active Directory in Enterprise Security
Active Directory is not merely a directory service; it’s the beating heart of authentication and authorization within Windows domains. Every login, every access request, every group policy application hinges on AD’s integrity. Its ubiquitous nature makes it an irresistible target for threat actors. A successful compromise of AD grants an attacker unparalleled control, enabling them to impersonate legitimate users, execute malicious code, and move laterally across networks unimpeded.
Understanding the NTDS.dit Database
The NTDS.dit file is the core component of Active Directory. It’s a database that stores virtually all Active Directory data, including user credentials (hashed passwords), group memberships, schema definitions, and other critical configuration information. Gaining access to this file is akin to possessing the master key to an entire enterprise: it allows attackers to harvest every domain credential, facilitating widespread lateral movement and ultimately, full domain compromise.
The Attack Vector: Bypassing Defenses to Exfiltrate NTDS.dit
The reported incident highlighted a concerning trend: attackers leveraging native Windows utilities to dump and exfiltrate the NTDS.dit database. This method is particularly insidious because it can bypass standard security controls that might flag unusual executable behavior. By utilizing legitimate system tools, the adversary effectively masks their malicious activities within routine system operations. The initial breach culminated in the acquisition of DOMAIN ADMIN privileges, a catastrophic outcome that provided the attackers with unrestricted control over the entire Active Directory environment.
While the specific initial compromise vector for privilege escalation to DOMAIN ADMIN wasn’t fully detailed in the source, common methods include:
- Phishing campaigns leading to credential theft.
- Exploitation of unpatched vulnerabilities in internet-facing services.
- Supply chain attacks.
- Weak password policies or compromised administrative accounts.
- Specific vulnerabilities like PetitPotam (CVE-2021-36942) or PrintNightmare (CVE-2021-1675, CVE-2021-34527) which have historically been used to achieve privilege escalation on domain controllers.
The Impact of Full Domain Compromise
Once DOMAIN ADMIN privileges are obtained and the NTDS.dit is exfiltrated, the impact is comprehensive and devastating:
- Credential Theft: All hashed user passwords can be cracked offline, providing attackers with valid credentials for almost every user in the domain.
- Lateral Movement: With valid credentials, attackers can move freely across the network, accessing sensitive systems and data without detection.
- Persistence: Adversaries can create new administrative accounts, modify group policies, and establish backdoors, ensuring long-term access to the compromised environment.
- Data Exfiltration: With full control, any sensitive data reachable within the domain becomes vulnerable to exfiltration.
- System Disruption: Attackers can deploy ransomware, wipe data, or otherwise sabotage critical infrastructure.
Remediation Actions and Proactive Defenses
Mitigating the risk of Active Directory compromise and NTDS.dit exfiltration requires a multi-layered, proactive security strategy. Organizations must assume breach and implement robust detection and response capabilities.
- Principle of Least Privilege: Enforce strict adherence to the principle of least privilege, especially for administrative accounts. Regular audits of administrative group memberships are crucial.
- Multi-Factor Authentication (MFA): Implement MFA for all user accounts, particularly for privileged users, to significantly reduce the impact of stolen credentials.
- Regular Patch Management: Keep all operating systems and applications, especially domain controllers, up-to-date with the latest security patches. This includes critical vulnerabilities like those related to Print Spooler (e.g., CVE-2021-1675, CVE-2021-34527) and authentication protocols (e.g., CVE-2021-36942).
- Network Segmentation: Isolate domain controllers on a segmented network, limiting direct access from less trusted parts of the network.
- Advanced Threat Detection: Deploy Endpoint Detection and Response (EDR) and Security Information and Event Management (SIEM) solutions to monitor for suspicious activities, including attempts to access the NTDS.dit file or execute native dumping utilities. Look for anomalies in processes accessing the AD database or unusual network traffic patterns from domain controllers.
- DC Shadow Attacks Prevention: Implement strong controls and monitoring to detect and prevent techniques like DCShadow, which involves making a rogue machine appear as a legitimate domain controller.
- Secure Configuration of Domain Controllers: Harden domain controllers according to best practices, disabling unnecessary services and ports.
- Regular Backups: Maintain frequent, secure, and offline backups of Active Directory to ensure recovery capabilities in case of a catastrophic compromise. Test these backups regularly.
- Mimikatz and LSASS Protection: Implement protections against credential dumping tools like Mimikatz targeting LSASS (Local Security Authority Subsystem Service). While the NTDS.dit dump is a different vector, protecting LSASS is a crucial adjacent defense.
Tools for Detection and Mitigation
| Tool Name | Purpose | Link |
|---|---|---|
| Microsoft Defender for Identity (MDI) | Detects advanced threats, identity-based attacks, and suspicious activities targeting Active Directory. | Microsoft Learn |
| Sysinternals Process Monitor | Monitors file system, Registry, and process/thread activity in real-time, useful for detecting suspicious NTDS.dit access. | Microsoft Learn |
| ADSecure / BloodHound | Identifies complex attack paths in Active Directory environments, helps prioritize remediation. | BloodHound GitHub |
| Group Policy Management Console (GPMC) | Manages and audits Group Policy Objects (GPOs) for secure configuration. | Microsoft Learn |
| Kerberos Delegation Manager | Helps manage and secure Kerberos delegation, reducing attack surfaces. | Microsoft Blog (historic) |
Conclusion
The compromise of Active Directory via NTDS.dit exfiltration is a critical threat that demands immediate attention. Organizations must prioritize the security of their Active Directory infrastructure, understanding that it represents the most valuable target for adversaries seeking full control. By implementing strong proactive defenses, continuous monitoring, and prompt remediation strategies, enterprises can significantly reduce their attack surface and better protect against these sophisticated identity-based attacks. The lesson is clear: secure Active Directory, secure the enterprise.





