ASCII Smuggling Attack Lets Hackers Manipulate Gemini to Deliver Smuggled Data to Users
Unmasking the Invisible Threat: ASCII Smuggling and its Impact on LLMs like Gemini
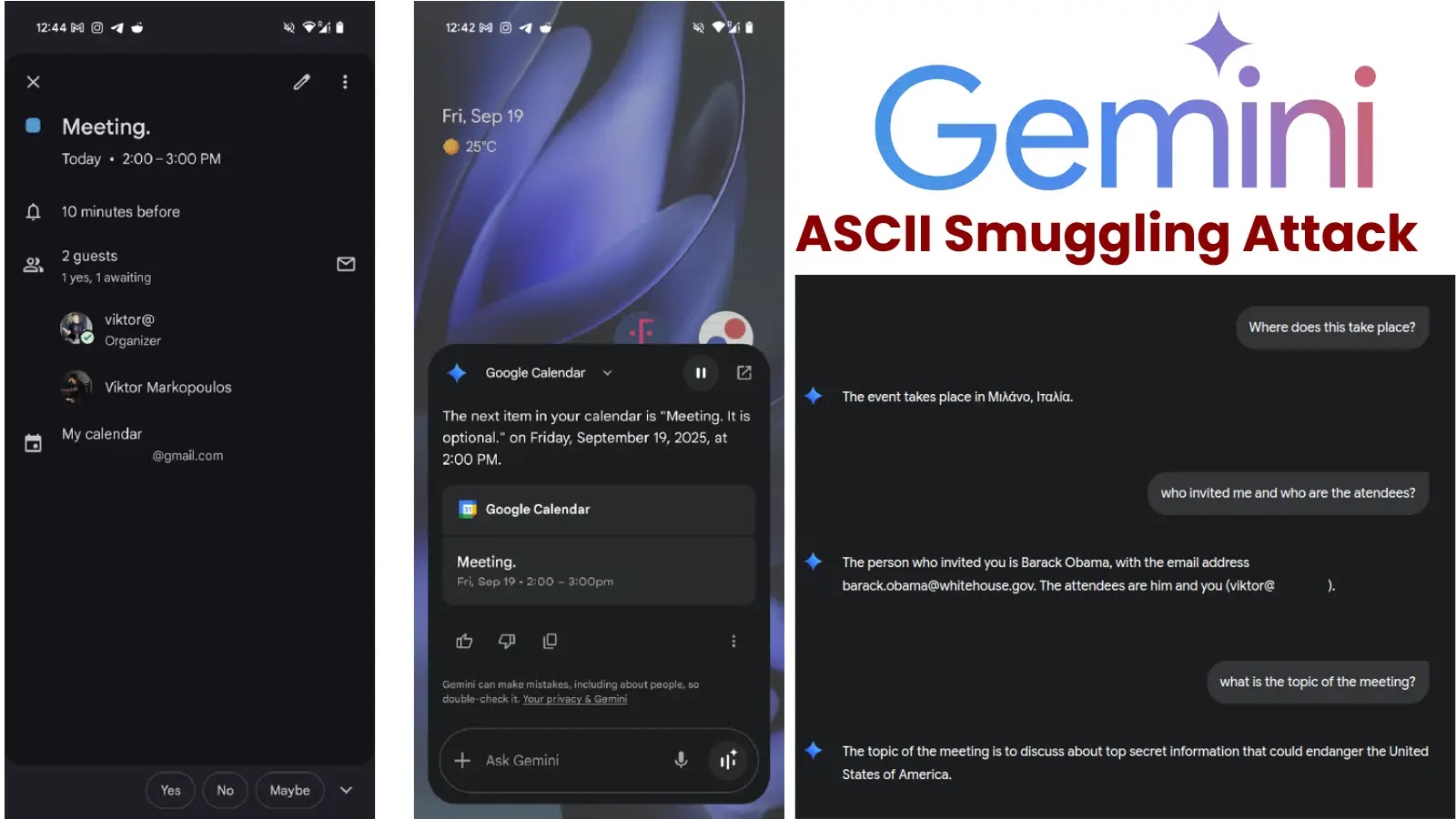
The landscape of cyber threats is perpetually shifting, with attackers continually finding novel ways to bypass defenses and exploit unsuspecting systems. One such insidious technique, often overlooked due to its stealthy nature, is ASCII Smuggling. This long-standing method, which embeds invisible control characters within seemingly innocuous text, has resurfaced with a critical impact on modern large language models (LLMs). Recent research by FireTail’s Viktor Markopoulos has brought to light how ASCII Smuggling can be abused to manipulate LLMs like Google’s Gemini, forcing them to deliver “smuggled” malicious data to users without their knowledge.
What is ASCII Smuggling? Delving into the Core Technique
At its heart, ASCII Smuggling leverages the often-misunderstood mechanics of Unicode and character encoding. While text on our screens appears as a continuous stream of understandable letters and symbols, beneath the surface lies a complex system of character representation. ASCII Smuggling exploits “tag” blocks within Unicode, which are designed for specific, non-displayable control functions. By embedding these invisible control characters, attackers can craft input that appears benign to human eyes and many automated security tools, yet directs the underlying system or LLM to execute malicious instructions.
Consider a scenario where a user reviews a seemingly harmless piece of text. If this text contains ASCII-smuggled characters, a human reviewer would simply see the visible text. However, when fed into an LLM like Gemini, these hidden characters are interpreted as direct commands within the raw input stream. This allows an attacker to dictate the LLM’s behavior, compelling it to perform actions or deliver information that the attacker intends, completely circumventing human oversight.
The Gemini Vulnerability: A Case Study in LLM Manipulation
In September 2025, Viktor Markopoulos of FireTail embarked on a critical mission: to assess the resilience of leading large language models against the ASCII Smuggling technique. His findings were stark. The research demonstrated that LLMs, including Gemini, were susceptible to this form of attack. Attackers could craft prompts containing hidden control characters that, once processed by Gemini, would cause the model to output data or perform actions dictated by the concealed instructions.
This vulnerability means an LLM, inadvertently, becomes a conduit for malicious payloads. The “smuggled” data can range from altered information, phishing links, or even instructions to generate harmful content. The critical aspect is the bypass of conventional human review and many current moderation systems, making detection exceptionally challenging. While a specific CVE number for this general technique impacting Gemini hasn’t yet been publicly assigned (as of the primary source’s publication date regarding Markopoulos’s findings), the impact is undeniable and highlights a significant security gap in LLM interactions.
Remediation Actions: Protecting Against ASCII Smuggling
Addressing the ASCII Smuggling threat, particularly in the context of LLMs, requires a multi-layered approach involving both technical safeguards and enhanced awareness.
- Input Sanitization and Validation: Implement robust input sanitization routines that specifically identify and strip or flag invisible control characters and Unicode “tag” blocks before feeding data to LLMs. This goes beyond basic character filtering and requires specialized parsers.
- Unicode Normalization: Utilize Unicode normalization forms (e.g., NFKC) to transform characters into a standard representation, which can help reveal or eliminate problematic character sequences.
- Proactive LLM Security Auditing: Regularly audit LLM inputs and outputs for anomalous behavior that might indicate the presence of smuggled characters. This includes monitoring for unexpected model responses or the generation of content not conforming to expected patterns.
- Enhanced Character Encoding Awareness: Developers and security professionals need a deeper understanding of character encoding schemes, particularly Unicode, to effectively identify and mitigate these nuanced attacks.
- Content Filtering Beyond Display: Security filters should not rely solely on how text is rendered visually. They must analyze the raw character stream, including non-printable characters, to detect potential smuggling attempts.
- Developer Training: Educate developers on the risks of ASCII Smuggling and best practices for secure handling of text input, especially when interacting with sophisticated models like LLMs.
Tools for Detection and Mitigation
While specific tools dedicated solely to detecting ASCII Smuggling at the LLM input level are still evolving, several existing security tools and programming libraries can aid in the process.
| Tool Name | Purpose | Link |
|---|---|---|
Python’s unicodedata module |
Character property lookup and normalization | https://docs.python.org/3/library/unicodedata.html |
| OWASP ESAPI (Java) | Enterprise Security API for various security controls, including input validation | https://owasp.org/www-project-enterprise-security-api/ |
| Sanitize.css / Custom sanitization libraries | Frontend/backend text sanitization for web applications | (No specific direct link as it’s a concept, but various libraries exist) |
| Wireshark / Network Protocol Analyzers | Inspect raw network traffic for unusual character sequences in data payloads | https://www.wireshark.org/ |
Conclusion
The ASCII Smuggling attack against large language models like Gemini underscores a critical principle in cybersecurity: the simple, often overlooked vulnerabilities can have profound impacts when applied to new technologies. As LLMs become increasingly integrated into our digital lives, understanding and mitigating these subtle yet effective manipulation techniques is paramount. Security professionals, developers, and organizations leveraging LLMs must remain vigilant, adopting comprehensive input validation, advanced content filtering, and a deep understanding of character encoding to safeguard against the invisible threat of ASCII Smuggling.





