Microsoft Intune MDM and Entra ID Leveraged to Elevate your Trust in Device Identity
Unveiling Device Identity: How Intune MDM Certificates and Entra ID Strengthen Trust
In the complex landscape of modern IT, accurately verifying device identity is paramount for maintaining robust security. Traditional methods often fall short, leaving organizations vulnerable to sophisticated threats. New research, however, illuminates a more reliable path leveraging the often-overlooked insights within Microsoft Intune’s Mobile Device Management (MDM) certificates, in conjunction with Microsoft Entra ID (formerly Azure Active Directory). This approach promises to significantly elevate trust in device and tenant identities, offering a critical advantage for security professionals and IT administrators alike.
The Challenge of Traditional Device Identification
For too long, organizations have relied on less robust methods for device identification, such as registry values. While these might offer a quick glance at device information, they are inherently susceptible to manipulation, impersonation, and inaccuracy. This weak link in the security chain can lead to unauthorized access, data breaches, and a compromise of an organization’s entire digital infrastructure. The need for a cryptographic, immutable, and verifiable source of device identity has never been more urgent in an era of zero-trust architectures and ever-escalating cyber threats.
Leveraging Intune MDM Certificates for Enhanced Trust
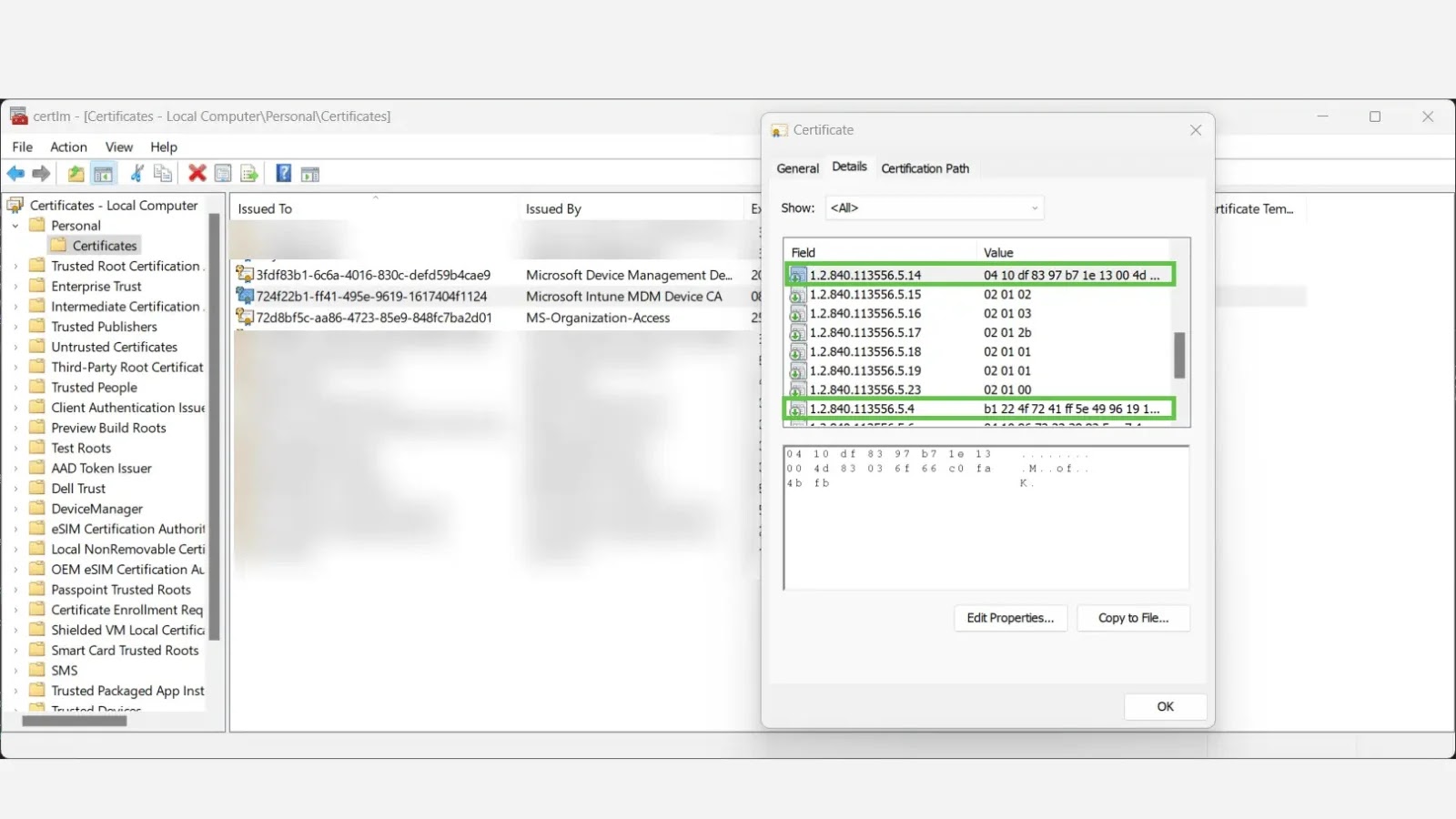
The core of this enhanced trust lies within the MDM certificates automatically issued to devices enrolled in Microsoft Intune. These aren’t just generic digital signatures; they contain a wealth of structured data, specifically Object Identifiers (OIDs). When properly decoded and interpreted, these OIDs reveal unique GUIDs (Globally Unique Identifiers) that precisely identify the MDM Device ID and, crucially, the tenant identity to which the device belongs. Unlike easily modified registry entries, these certificate-bound OIDs provide a cryptographically strong anchor for device identity, making them incredibly difficult to spoof or tamper with.
This method drastically improves the granularity and reliability of device identification, allowing security systems to not just “see” a device, but to “authenticate” its unique identity and its legitimate association with the organizational tenant. This capability is foundational for implementing fine-grained access controls and ensuring only trusted devices can access sensitive corporate resources. For further details on this innovative approach, refer to the original findings linked here.
The Role of Microsoft Entra ID in Identity Verification
Microsoft Entra ID plays a pivotal role in this enhanced security posture. As the central identity and access management service, it acts as the authoritative source for user and device identities within the Microsoft ecosystem. When Intune-managed devices communicate with Entra ID, the MDM certificate information, including the OIDs representing the device and tenant GUIDs, can be seamlessly integrated into the identity verification process. This integration allows Entra ID to cross-reference and validate the device’s certified identity against its registered profile, providing an undeniable assurance of authenticity.
This synergy between Intune MDM certificates and Entra ID creates a powerful framework for:
- Stronger Device Authentication: Moving beyond simple passwords or easily compromised device attributes.
- Enhanced Compliance Auditing: Providing verifiable proof of device enrollment and association with the correct tenant.
- Improved Incident Response: Quickly identifying and isolating compromised or unauthorized devices based on their cryptographic identity.
- Refined Access Policies: Implementing conditional access policies that can rely on a high degree of confidence in device identity.
Remediation Actions: Implementing Enhanced Device Trust
Organizations should proactively adopt strategies to leverage these insights into their security infrastructure. While this discovery isn’t a direct vulnerability, it highlights a previously underutilized mechanism for robust security. Here are key actions:
- Prioritize Intune Enrollment: Ensure all corporate devices are enrolled and actively managed by Microsoft Intune to benefit from MDM certificates.
- Integrate with SIEM/SOAR: Develop or adapt existing security information and event management (SIEM) and security orchestration, automation, and response (SOAR) solutions to parse and interpret OID data from MDM certificates for richer context in security alerts.
- Review Conditional Access Policies: Update Microsoft Entra Conditional Access policies to incorporate device trust signals derived from MDM certificate identity, moving towards a true zero-trust model.
- Educate Security Teams: Train security analysts on how to interpret and utilize MDM certificate data for forensic analysis and incident response.
- Monitor Certificate Lifecycles: Implement robust processes for monitoring the issuance, renewal, and revocation of MDM certificates to prevent expired or compromised certificates from undermining trust.
Conclusion
The discovery of verifiable insights within Microsoft Intune MDM certificates, coupled with the power of Microsoft Entra ID, offers a transformative opportunity for organizations to fundamentally increase their trust in device and tenant identities. By moving beyond easily manipulated attributes to cryptographically secured OIDs, businesses can build far more resilient security postures against an ever-evolving threat landscape. Embracing this approach is not merely an enhancement; it’s a strategic imperative for securing the modern enterprise and bolstering the foundational elements of a zero-trust architecture.





