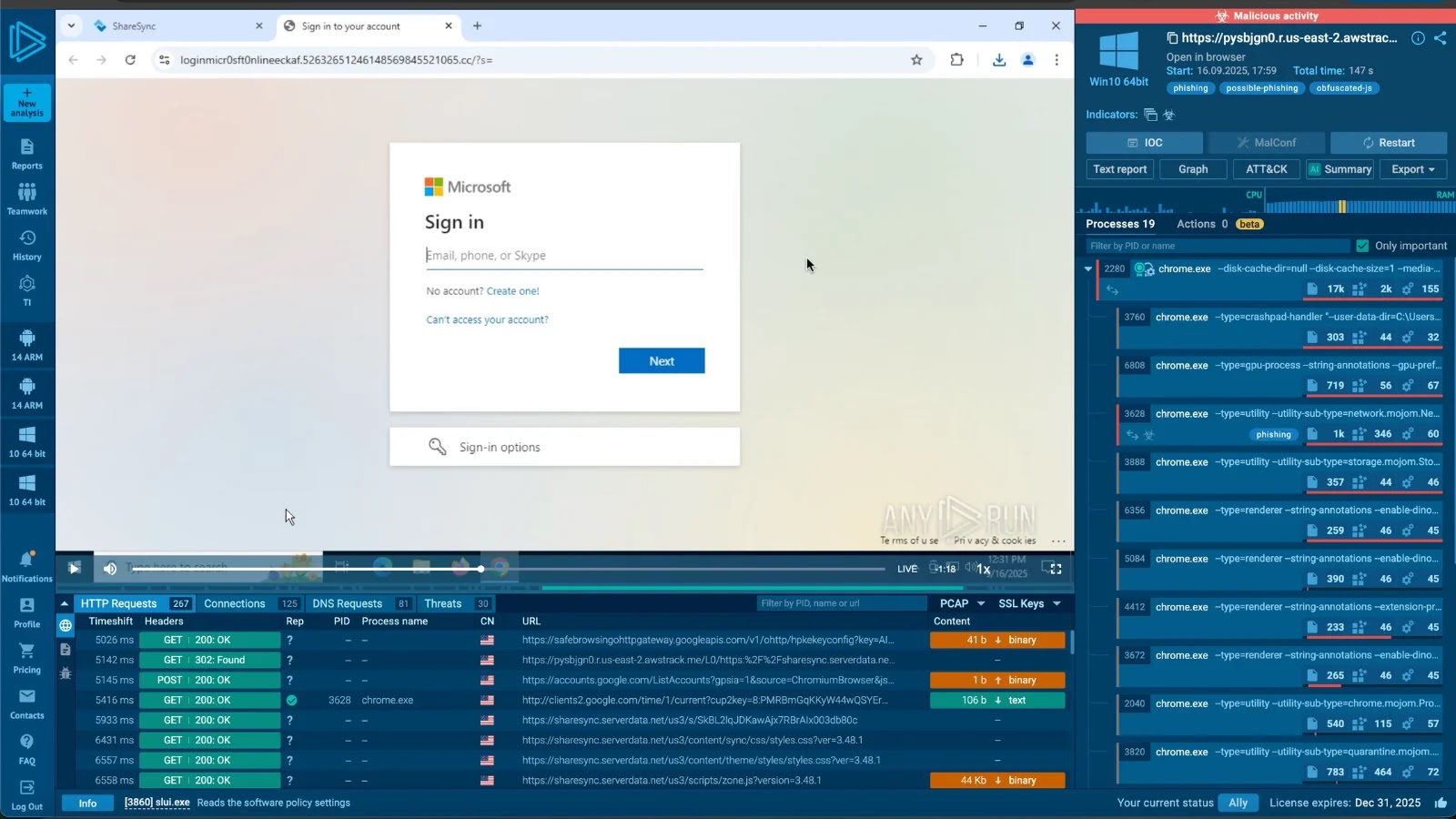
New Tykit Phishing Kit Mimics Microsoft 365 Login Pages to Steal Corporate Account Credentials
In the relentless battle against cyber threats, a new contender has emerged, specifically targeting one of the most widely used business platforms: Microsoft 365. The Tykit phishing kit, a sophisticated tool designed to mimic legitimate Microsoft 365 login pages, has significantly escalated its activity, posing a direct threat to corporate account credentials. As cybersecurity professionals, understanding the nuances of such threats is paramount to developing effective defense strategies.
Tykit: A Deep Dive into a Sophisticated Phishing Kit
First detected in May 2023, the Tykit phishing kit has showcased a notable surge in deployments during September and October. Its primary objective is straightforward: to harvest corporate credentials by deceiving users into believing they are interactin with official Microsoft 365 login portals. What sets Tykit apart from more rudimentary phishing attempts is its advanced operational methodology and consistent efforts to evade detection.
A key characteristic of Tykit’s stealth is its use of SVG files as a delivery mechanism. This technique allows the phishing pages to be delivered in a less conspicuous manner, often bypassing traditional email filters that might flag more common malicious attachments or embedded links. Once a user interacts with the SVG file, they are typically redirected to a convincing replica of a Microsoft 365 login page.
Beyond Basic Lures: Tykit’s Evolved Tactics
Unlike less sophisticated phishing campaigns, Tykit exhibits a marked maturity in its approach. This includes:
- Consistent Obfuscation Techniques: The kit employs various methods to obscure its malicious code and activities, making it challenging for security systems to analyze and block. This consistent obfuscation is a hallmark of well-developed threat actor tools.
- Multi-Stage Command-and-Control (C2) Interactions: Tykit doesn’t rely on a single, easily traceable point of contact for its operations. Instead, it utilizes multi-stage C2 communications, adding layers of complexity for threat hunters attempting to map its infrastructure and disrupt its operations. This distributed approach enhances its resilience and persistence.
The combination of these advanced tactics indicates that Tykit is not a fleeting threat but a well-engineered tool, likely wielded by sophisticated attackers with a clear understanding of corporate network defenses and user psychology.
Remediation Actions and Protective Measures
Given the escalating threat posed by the Tykit phishing kit, organizations must implement robust defensive strategies to protect their Microsoft 365 environments. Proactive measures are crucial to prevent credential compromise.
- Implement Multi-Factor Authentication (MFA): Even if credentials are stolen, MFA significantly complicates an attacker’s ability to gain unauthorized access. This is arguably the single most effective defense against phishing attacks that target credentials.
- Enhanced Email Security Gateways: Deploy and configure advanced email security solutions capable of detecting and blocking sophisticated phishing attempts, including those utilizing SVG files or obfuscated links. Regularly update threat intelligence feeds for these systems.
- User Awareness Training: Conduct regular and realistic security awareness training for all employees. Educate them on the tell-tale signs of phishing attempts, especially those mimicking trusted brands like Microsoft. Emphasize checking URL legitimacy and exercising caution before entering credentials.
- Endpoint Detection and Response (EDR): Utilize EDR solutions to monitor for suspicious activity on endpoints that might indicate a successful phishing attempt or a subsequent compromise. This includes unusual login patterns or access attempts from unrecognized locations.
- Conditional Access Policies: Leverage Microsoft 365’s conditional access policies to enforce stricter access requirements based on user location, device compliance, or application usage.
- Regular Security Audits: Conduct periodic security audits and penetration tests to identify potential vulnerabilities in your security posture and ensure that existing controls are effective against evolving threats.
Detection and Analysis Tools
While Tykit does not yet have an assigned CVE (e.g., CVE-2023-12345 is a placeholder for demonstration), the principles of detection remain consistent for advanced phishing campaigns. Security analysts can utilize various tools to identify and analyze such threats:
| Tool Name | Purpose | Link |
|---|---|---|
| PhishTank | Community-driven phishing URL database for checking known malicious URLs. | https://www.phishtank.com/ |
| URLScan.io | Automated website scanner that analyzes URLs for suspicious activity and content. | https://urlscan.io/ |
| VirusTotal | Aggregates results from multiple antivirus engines and URL/domain blacklisting services. | https://www.virustotal.com/ |
| Custom SIEM Rules | Develop specific rules within your Security Information and Event Management (SIEM) system to flag unusual login patterns or access from suspicious IP addresses. | (Integrates into existing SIEM platforms) |
Conclusion
The emergence and increasing prevalence of sophisticated phishing kits like Tykit underscore the adaptive nature of cyber threats. By impersonating critical services like Microsoft 365 and employing advanced obfuscation and delivery mechanisms, these kits pose a significant challenge to corporate cybersecurity. Organizations must move beyond basic defenses, embracing a multi-layered security approach that combines robust technical controls with continuous user education. Staying informed about the latest threats and proactively implementing remediation actions are essential steps in protecting valuable corporate account credentials.





