SOCs Have a Quishing Problem: Here’s How to Solve It
The Sneaky Threat: How Quishing is Exploiting SOC Blind Spots
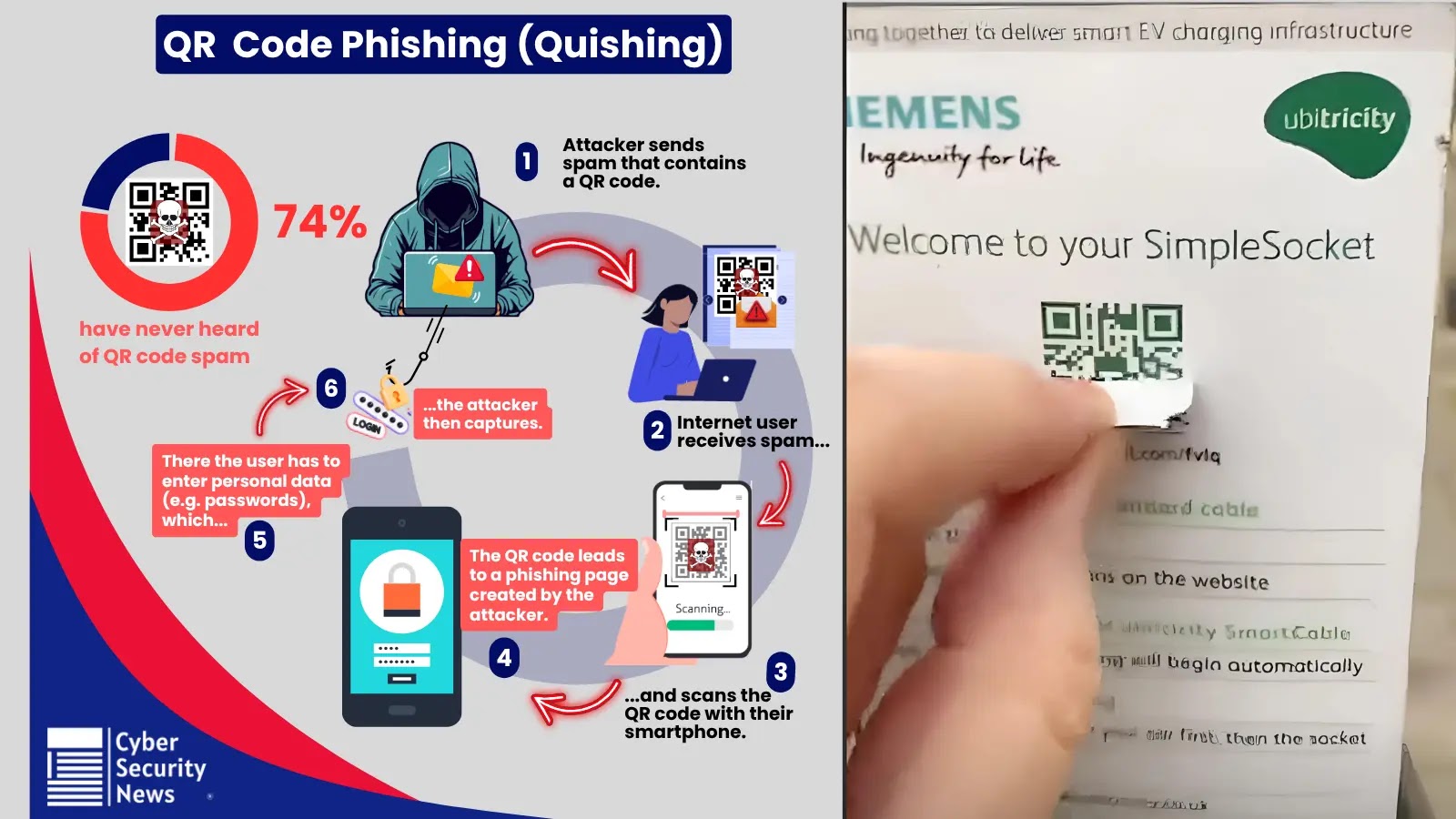
QR codes, once a convenient tool for quick information access, have undergone a sinister transformation. No longer harmless, these innocent-looking graphical squares are now a primary vector for sophisticated phishing attacks known as quishing. For Security Operations Centers (SOCs), this escalating threat presents a critical blind spot, as traditional security measures often fail to detect these cunning attacks. This article delves into the mechanics of quishing, its impact on SOC visibility, and, most importantly, provides actionable strategies to defend against it.
Understanding the Quishing Menace
Quishing, or QR code phishing, operates by embedding malicious links within a QR code image. The brilliance (and danger) of this technique lies in its ability to bypass standard email filters and URL scanning tools that are designed to scrutinize text-based links. A user simply scans the QR code, often from a physical printout, an email attachment, or even a digital display, and is immediately redirected to a fraudulent website. These sites are meticulously crafted to mimic legitimate login portals for services like banking, email, or corporate applications, with the sole purpose of stealing credentials or initiating malware downloads.
A significant challenge arises from the common use of mobile devices for scanning QR codes. This moves the attack vector outside the direct purview of many SOC monitoring tools, which are typically focused on network traffic originating from managed endpoints. The lack of visibility into mobile device activity makes detecting and responding to quishing attempts significantly more complex.
The SOC Visibility Gap: Why Quishing Sidesteps Defenses
Traditional SOC tools, while effective against many cyber threats, struggle with quishing due to several inherent limitations:
- Image-Based Evasion: QR codes are images. Standard email gateways and web filters are not designed to “read” or analyze the embedded URL within an image.
- Mobile Device Blindness: Many organizations lack comprehensive security solutions for personal or unmanaged mobile devices. When an employee scans a malicious QR code on their personal phone, that activity is often invisible to the corporate SOC.
- Lack of DNS & URL Filtering: While endpoint protection platforms (EPP) and network detection and response (NDR) solutions continuously monitor network traffic for suspicious DNS requests and URLs, the initial redirection from a scanned QR code might occur on a device not fully integrated into the corporate security fabric.
- Social Engineering Exploitation: Quishing heavily relies on social engineering. Attackers craft convincing scenarios to entice users to scan codes, leveraging curiosity or urgency, often bypassing technological controls through human psychology.
Remediation Actions: Fortifying Your Defenses Against Quishing
Addressing the quishing problem requires a multi-layered approach, combining technological safeguards with robust security awareness training.
- Enhanced Email and Web Security with QR Code Scanning:Implement email security gateways that include advanced image analysis capabilities to detect embedded QR codes and extract/analyze their URLs. Some modern solutions offer this, moving beyond simple text analysis.
- Mobile Device Management (MDM) & Mobile Threat Defense (MTD):For organizations permitting bring-your-own-device (BYOD) or providing corporate mobile devices, robust MDM/MTD solutions are crucial. These tools can enforce security policies, detect malicious apps, and identify suspicious network activity originating from mobile devices, providing critical visibility where it was previously lacking. Look for solutions that integrate QR code scanning into their threat detection frameworks.
- Advanced Endpoint Protection Platforms (EPP) with Behavioral Analysis:Ensure EPP solutions are deployed across all endpoints, including laptops and desktops. While the initial scan might happen elsewhere, if a user lands on a malicious site or downloads malware, a good EPP with behavioral detection can often identify and block the subsequent malicious activity. This may include detecting common post-compromise activities, regardless of the initial infection vector.
- Strengthened DNS Filtering and Web Proxies:Deploy comprehensive DNS filtering and web proxies that block access to known malicious domains, command-and-control servers, and newly registered domains (NRDs) often used in phishing campaigns. This acts as a crucial safety net even if a user bypasses initial QR code detection.
- Security Awareness Training (SAT) Focused on QR Codes:This is arguably the most critical defense. Educate employees about the dangers of unsolicited QR codes. Key training points should include:
- Verify the Source: Always question the legitimacy of a QR code, especially if it appears in an unexpected context (e.g., in a suspicious email, on a public flyer that seems out of place).
- Inspect Before You Scan: Advise users to look for signs of tampering (stickers over legitimate codes, pixelated images).
- Preview the URL: Many QR code scanner apps offer a preview of the embedded URL before navigating. Teach users to always check this URL for legitimacy before proceeding. Train them to recognize common phishing indicators in URLs (e.g., misspelled domains like “g00gle.com” instead of “google.com”).
- Use Official Apps: Encourage the use of official, trusted apps for QR code scanning that may offer built-in security features or URL verification.
- Report Suspicious Codes: Establish a clear process for employees to report any suspicious QR codes encountered.
- Regular Penetration Testing and Phishing Simulations:Include QR code-based phishing scenarios in your regular penetration tests and phishing simulations. This helps identify vulnerabilities in user behavior and security controls before real attackers exploit them.
Tools for Detection and Mitigation
Securing against quishing necessitates a combination of preventative and detective technologies. Here are some categories of tools that can aid in your defense:
| Tool Category | Purpose | Examples/Considerations |
|---|---|---|
| Email Security Gateways (ESG) | Advanced threat protection, including image analysis for QR codes, URL rewriting/filtering. | Proofpoint, Mimecast, Microsoft Defender for Office 365 (with advanced features) |
| Mobile Threat Defense (MTD) | Real-time threat detection on mobile devices, preventing access to malicious sites, app scanning. | Zimperium, Lookout, Check Point Harmony Mobile |
| Endpoint Detection and Response (EDR) / Extended Detection and Response (XDR) | Behavioral analysis on endpoints to detect post-scan malicious activity, fileless malware. | CrowdStrike Falcon, SentinelOne, Microsoft Defender for Endpoint |
| DNS Filtering / Secure Web Gateways (SWG) | Blocking access to known malicious domains and unauthorized content, even if initial access was via a QR code. | Cisco Umbrella, Zscaler, Cloudflare Gateway |
| Security Awareness Training Platforms | Educating users on identifying and reporting phishing attacks, including quishing. | KnowBe4, Cofense, SANS Cyber Awareness Training |
Conclusion: A Proactive Stance Against Evolving Threats
The rise of quishing highlights a crucial lesson in cybersecurity: attackers constantly innovate, and our defenses must evolve just as quickly. By understanding the mechanics of QR code phishing, recognizing the visibility gaps in traditional SOC operations, and implementing a holistic strategy that combines advanced technology with comprehensive security awareness training, organizations can significantly reduce their risk exposure. A proactive approach to identifying and mitigating new threat vectors like quishing is not just a best practice; it’s a necessity in safeguarding digital assets and maintaining operational integrity.





