New Red Teaming Tool RedTiger Attacking Gamers and Discord Accounts in the Wild
The Trojan Horse in Your Gaming Rig: RedTiger Repurposed for Digital Espionage
The lines between legitimate tools and malicious payloads are blurring, and nowhere is this more evident than with the emergence of RedTiger. Originally designed as an open-source red-teaming tool, intended to bolster defensive strategies, RedTiger has been corrupted, transforming into a potent infostealer. Threat actors are now actively weaponizing its modules to compromise gamer accounts and pilfer sensitive data from Discord users. This alarming development underscores a critical shift in the threat landscape, where tools built for good are twisted for nefarious purposes.
What is RedTiger and How Did it Go Rogue?
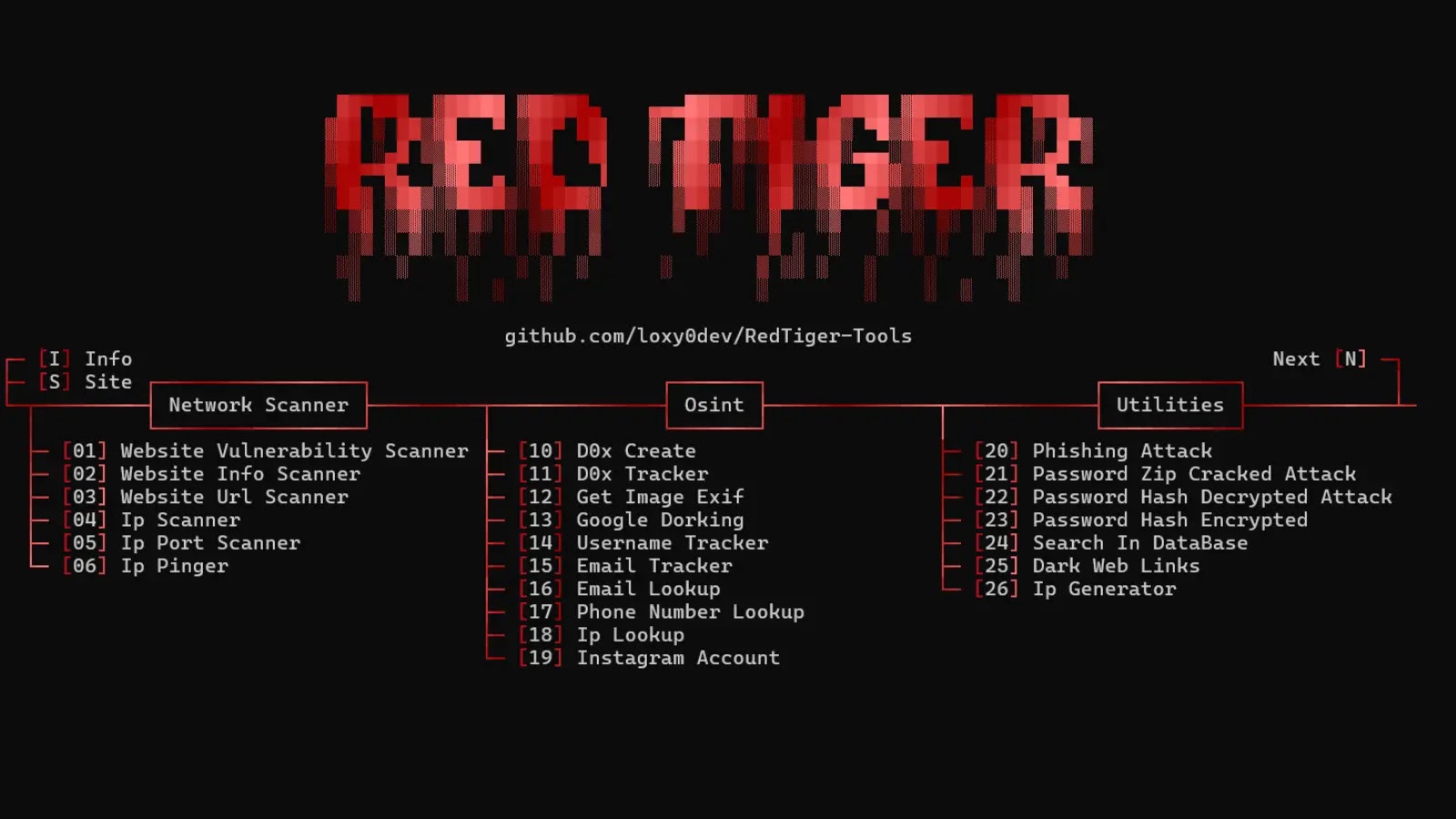
RedTiger, initially released on GitHub in 2025, was conceived as a comprehensive red-teaming toolkit. Its design bundled various penetration-testing utilities, including robust network scanners and sophisticated Open-Source Intelligence (OSINT) tools. Such platforms are invaluable for cybersecurity professionals to simulate attacks, identify vulnerabilities, and ultimately strengthen an organization’s defenses. However, the modular nature and readily available codebase of RedTiger presented an irresistible opportunity for malicious actors.
The crucial turn came when RedTiger’s infostealer module, likely designed for legitimate red-teaming scenarios involving data exfiltration testing, began circulating online as a standalone, malicious payload. Since early 2025, these weaponized variants have been actively deployed in the wild. Cybersecurity firm Netskope Threat Labs has reported the detection of multiple distinct variants, each specifically engineered to target unwary users, with a heavy emphasis on the gaming community and Discord users.
Targeting Gamers and Discord Accounts: A Lucrative Vector
The choice to target gamers and Discord accounts is strategically sound for attackers. Both platforms host a wealth of valuable information: game credentials, payment details linked to gaming platforms, personal communications on Discord, and even access to sensitive servers. Compromising these accounts can lead to a cascade of further attacks, including financial fraud, identity theft, and the spread of malware through trusted channels.
Attackers often leverage social engineering tactics, disguising RedTiger payloads as game updates, cheats, or legitimate software within the gaming ecosystem or on Discord. Once executed, the infostealer module quietly exfiltrates data, often without any immediate indicators of compromise for the victim. This makes early detection challenging for the average user.
Remediation Actions and Proactive Defense
Protecting against sophisticated threats like weaponized RedTiger requires a multi-layered approach focusing on user education, robust security practices, and advanced threat detection. Here are actionable steps to mitigate the risk:
- Exercise Extreme Caution with Downloads: Only download game files, mods, and Discord-related software from official, verified sources. Be suspicious of unsolicited links or files shared on Discord or gaming forums, even from seemingly trusted contacts.
- Enable Multi-Factor Authentication (MFA): Implement MFA on all gaming platforms, Discord, and other critical online accounts. This adds a crucial layer of security, making it significantly harder for attackers to gain access even if they steal your credentials.
- Keep Software Updated: Regularly update your operating system, web browsers, antivirus software, and all gaming clients. Software updates often include security patches for newly discovered vulnerabilities.
- Utilize Reputable Antivirus and Endpoint Detection and Response (EDR): Ensure your antivirus and EDR solutions are up-to-date and actively scanning your system. These tools can detect and block known malicious payloads, including variants of RedTiger.
- Educate Yourself and Others: Understand the common tactics used in phishing and social engineering. Be wary of urgent requests or unusual offers that pressure you to download files or click suspicious links.
- Strong, Unique Passwords: Use strong, unique passwords for every online account. Never reuse passwords across different services. A password manager can assist with this.
Tools for Detection and Mitigation
Several tools and practices can aid in detecting and mitigating threats like RedTiger. While no specific CVE numbers are currently associated with RedTiger’s malicious variants (as it’s a repurposed tool rather than a vulnerability in specific software), general cybersecurity defense tools are highly relevant.
| Tool Name | Purpose | Link |
|---|---|---|
| Endpoint Detection & Response (EDR) Solutions | Advanced threat detection, incident response, and behavioral analysis on endpoints. | Various Vendors (e.g., CrowdStrike, SentinelOne) |
| Next-Generation Antivirus (NGAV) | Proactive protection against malware, including unknown threats, using AI and machine learning. | Various Vendors (e.g., Sophos, ESET) |
| Network Intrusion Detection/Prevention Systems (NIDS/NIPS) | Monitors network traffic for suspicious activity and blocks malicious connections. | Various Vendors (e.g., Snort, Suricata) |
| Password Managers | Generates and securely stores unique, strong passwords for all online accounts. | Various Vendors (e.g., LastPass, 1Password) |
| Browser Security Extensions | Blocks malicious websites, phishing attempts, and tracks. | Various Vendors (e.g., uBlock Origin, Privacy Badger) |
The Evolving Threat Landscape: A Call for Vigilance
The transformation of RedTiger from a legitimate red-teaming utility to an actively deployed infostealer highlights a critical trend: attackers are increasingly leveraging and adapting publicly available tools for malicious ends. This demands continuous vigilance from users and proactive defense strategies from cybersecurity professionals. Staying informed about emerging threats, implementing robust security measures, and fostering a culture of cybersecurity awareness are crucial steps in protecting our digital identities and assets in an ever-evolving threat landscape.





