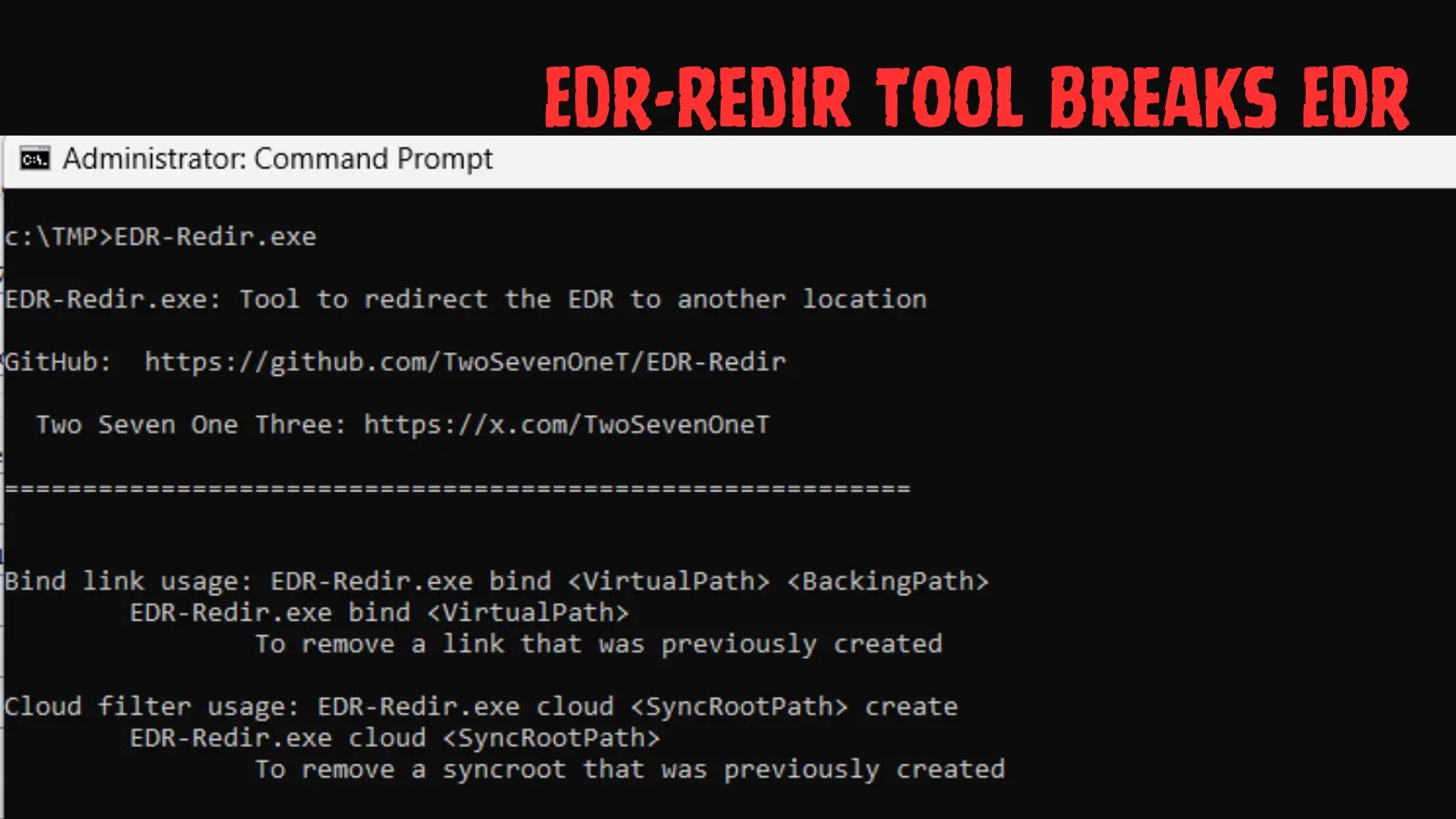
New EDR-Redir Tool Breaks EDR Exploiting Bind Filter and Cloud Filter Driver
Unmasking EDR-Redir: How a New Tool Exploits Windows Filters to Bypass Endpoint Security
Endpoint Detection and Response (EDR) solutions are the bedrock of modern cyber defense, acting as critical sentinels against sophisticated threats. However, a newly unveiled tool named EDR-Redir threatens to undermine these vital protections by exploiting subtle yet powerful mechanisms within the Windows operating system. This development signals a concerning advancement in attacker techniques, allowing the redirecting or isolation of EDR executable folders without requiring privileged kernel-level access.
The EDR-Redir Threat: A User-Mode Bypass
Cybersecurity researcher TwoSevenOneT demonstrated EDR-Redir, a novel technique that operates entirely in user mode. This distinction is crucial: historical methods for bypassing EDR often relied on kernel-level exploits, which are significantly more complex and risky for attackers to execute. EDR-Redir, by contrast, leverages built-in Windows functionalities, making it stealthier and potentially more widespread.
The core of EDR-Redir’s efficacy lies in its manipulation of two specific Windows components:
- Bind Filter Driver (
bindflt.sys): This driver is designed for file system binding, allowing one folder’s content to be represented as another. Attackers can abuse this to redirect critical EDR executables to a different, attacker-controlled location, effectively “shadowing” them. - Cloud Filter Driver (
cldflt.sys): Primarily used for cloud storage synchronization, this driver can be exploited to isolate EDR processes or directories. By “filtering” the EDR’s access to its own files or system resources, attackers can cripple its ability to monitor and respond to threats.
Understanding the Bind Filter Driver Exploitation
The bindflt.sys driver, while benign in its intended purpose, presents a powerful attack surface. By manipulating its functions, EDR-Redir can create a “bind mount” that effectively swaps the EDR’s expected executable path with a decoy. For instance, if an EDR’s main executable is at C:\Program Files\EDR\edr.exe, EDR-Redir could bind an empty or malicious directory to C:\Program Files\EDR\. When the EDR attempts to access its files, it would instead interact with the attacker’s chosen location, rendering it ineffective or even vulnerable to further compromise.
Understanding the Cloud Filter Driver Exploitation
Similarly, the cldflt.sys driver, typically used by services like OneDrive, offers another avenue for compromise. EDR-Redir can exploit this driver to quarantine or impede EDR processes. By configuring filters that block specific file operations or directory access for EDR components, attackers can effectively “sand-box” the EDR, preventing it from performing its detection and response duties. This can create a blind spot, allowing malicious activities to proceed undetected.
The Impact: A New Frontier for Evasion
The emergence of EDR-Redir underscores a continuous cat-and-mouse game between defenders and attackers. This user-mode technique poses a significant challenge because:
- Lower Barrier to Entry: User-mode exploits are generally easier to develop and deploy than kernel-level attacks.
- Stealth: Operating in user space may make these activities harder for some EDRs to detect, especially those with less robust behavioral analytics tailored to these specific Windows native functions.
- Widespread Applicability: Given that
bindflt.sysandcldflt.sysare fundamental Windows components, this exploitation method could potentially affect a broad range of EDR solutions across various Windows versions.
Remediation Actions and Mitigations
Organizations must proactively address the threat posed by tools like EDR-Redir. While no single solution offers a complete panacea, a multi-layered security strategy is paramount:
- Enhanced EDR Behavioral Analytics: Focus on EDR solutions that possess advanced behavioral analytics capable of detecting anomalous activity related to file system binding, cloud filter manipulation, and process isolation, even if executed in user mode.
- Regular Patching and Updates: Ensure all Windows systems and EDR solutions are kept up-to-date with the latest security patches. While EDR-Redir exploits existing functionality, future Windows updates might introduce mitigations or better monitoring hooks.
- Principle of Least Privilege: Enforce strict adherence to the principle of least privilege for all user accounts and applications. This limits the potential impact if an account or application is compromised.
- Integrity Monitoring: Implement robust file and process integrity monitoring. Alert on any unauthorized changes to critical system files, EDR binaries, or unexpected changes in filter driver configurations.
- Network Segmentation: Segment your network to limit the lateral movement of attackers even if an endpoint’s EDR is compromised.
- Threat Hunting: Actively hunt for indicators of compromise (IOCs) related to bind filter or cloud filter driver manipulation. Educate security teams on these specific techniques.
- Advanced Memory Protection: Employ EDRs that offer advanced memory protection features to detect and prevent code injection or manipulation within legitimate processes.
Tools for Detection and Mitigation
While EDR-Redir is a new technique, existing tools and practices can aid in detection and response:
| Tool Name | Purpose | Link |
|---|---|---|
| Sysmon | Advanced system activity monitoring for detailed event logging. Can detect file system binds and driver loads. | Microsoft Sysmon |
| Process Monitor | Real-time file system, registry, and process/thread activity monitoring. Useful for investigating suspicious file operations. | Microsoft Process Monitor |
| EDR Solutions (with advanced behavioral analysis) | Endpoint detection and response for detecting anomalous process behavior, file system manipulation, and potential EDR bypass attempts. | (Vendor Specific) |
| Windows Event Viewer | Review system logs for suspicious driver loads, service changes, or file system errors related to EDR interference. | (Built-in Windows Utility) |
Conclusion
The EDR-Redir tool represents a significant evolution in evasion tactics, highlighting the ongoing need for vigilance and adaptation in cybersecurity. By exploiting native Windows functionalities like the Bind Filter and Cloud Filter drivers, attackers can bypass EDR protections without resorting to complex kernel-level exploits. Organizations must prioritize robust EDR solutions with advanced behavioral detection capabilities, enforce the principle of least privilege, and maintain diligent patching and integrity monitoring. Staying ahead requires understanding these novel attack vectors and continuously refining defense strategies to counter emerging threats.





