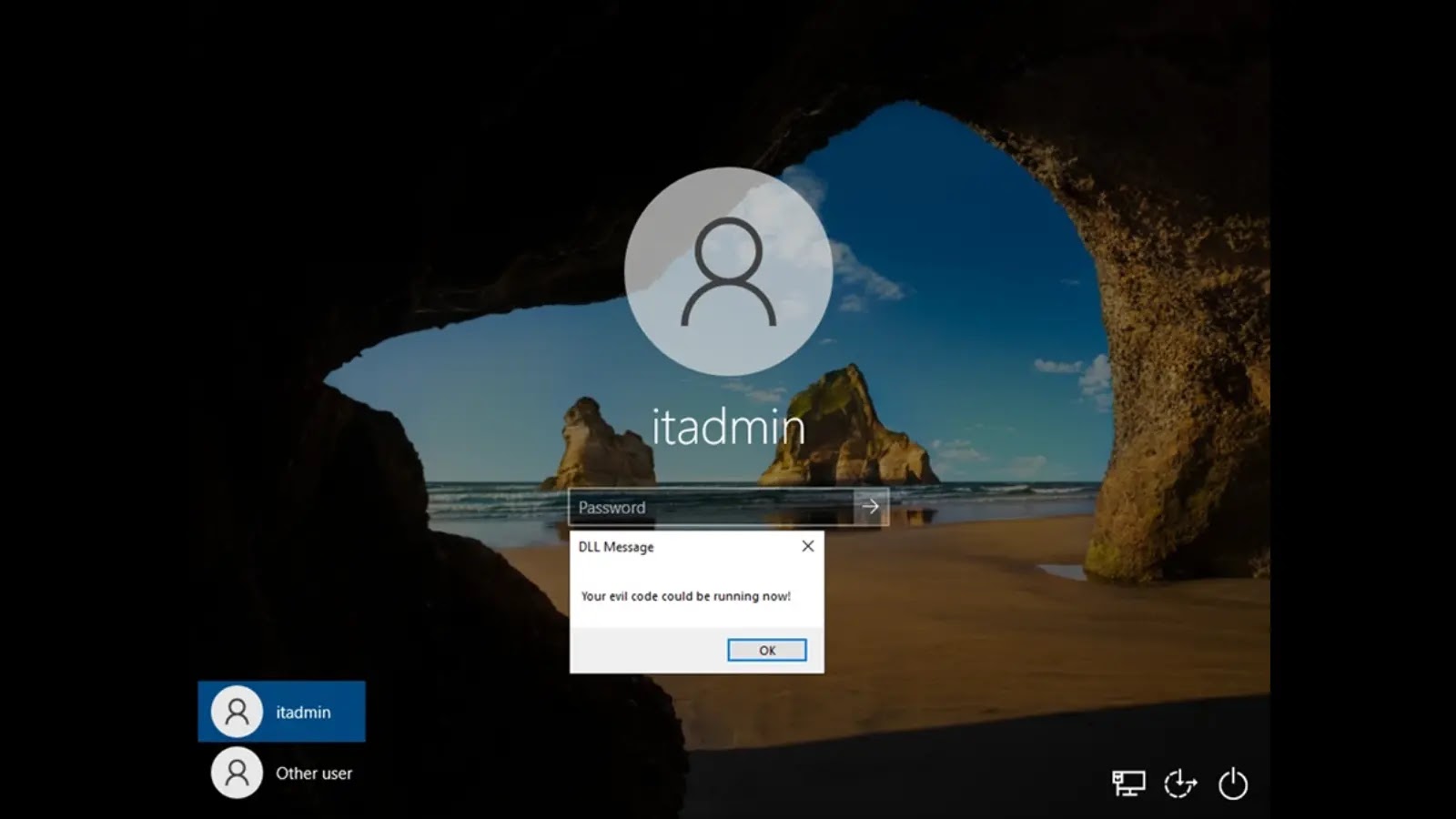
Windows Accessibility Flaw Allows Stealthy Persistence and Lateral Movement via Narrator DLL Hijack
Unmasking the Stealthy Threat: Windows Narrator DLL Hijacking
The digital landscape demands constant vigilance against evolving threats. Even seemingly innocuous system features can harbor critical vulnerabilities. One such persistent concern is the recurring issue of DLL hijacking, and a recent spotlight shines on the Windows Narrator accessibility tool. This flaw allows attackers to establish stealthy persistence and facilitate lateral movement within compromised networks, posing a significant risk to organizations.
First reported as early as 2013, the vulnerability within Windows Narrator highlights a long-standing security gap. Malicious actors can exploit this legitimate system tool, transforming it into a conduit for compromise. Understanding the mechanics of this flaw is crucial for cybersecurity professionals tasked with defending their digital perimeters.
Understanding DLL Hijacking and the Narrator Exploit
Dynamic Link Library (DLL) hijacking is a code injection technique where an attacker manipulates a legitimate application to load a malicious DLL instead of its intended, legitimate counterpart. When the application attempts to load a DLL, it searches for it in a predefined order of directories. If an attacker places a malicious DLL with the same name in an earlier-searched directory, the application will load the attacker’s DLL, executing their code.
In the context of the Windows Narrator, this accessibility tool, essential for many users, becomes a vector for attack. The Narrator process, which often runs with elevated privileges, can be tricked into loading a malicious DLL. Once loaded, the attacker’s code operates within the trusted context of Narrator, granting them significant capabilities without raising immediate red flags.
The Dangers: Persistence and Lateral Movement
The implications of a successful Narrator DLL hijack are substantial, primarily focusing on two critical attack phases:
- Stealthy Persistence: By injecting a malicious DLL into a legitimate, often auto-starting, system process like Narrator, attackers can ensure their code is executed every time the system boots or the Narrator service is initiated. This grants them a persistent foothold, making detection and eradication challenging. Traditional endpoint detection and response (EDR) solutions might overlook this activity if they primarily monitor for new, unknown processes.
- Lateral Movement: With code execution within a privileged process, attackers can then leverage this access to explore the network, gain access to other systems, and elevate their privileges. The Narrator’s trusted status can facilitate bypassing certain security controls that might flag less legitimate-looking processes. This enables attackers to move laterally across an organization’s network, extending their reach and impact.
Remediation Actions: Securing Your Systems
Mitigating the risk of Narrator DLL hijacking, and DLL hijacking in general, requires a multi-layered approach. Organizations must prioritize proactive security measures and swift response capabilities.
- Implement Secure DLL Loading Practices: Developers should adhere to secure DLL loading practices, explicitly specifying the full path to necessary DLLs rather than relying on default search paths. Using mechanisms like
SetDllDirectoryor manifest files can help. - Patch and Update Regularly: While specific CVEs for this long-standing Narrator issue are not always distinct due to its nature as a technique rather than a single flaw, ensuring all Windows systems are fully patched and updated is paramount. Microsoft frequently releases security updates that address potential DLL loading vulnerabilities.
- Principle of Least Privilege: Enforce the principle of least privilege for all users and applications. Running Narrator or any application with the minimum necessary permissions can limit the potential damage if a DLL hijack occurs.
- Monitor for Suspicious Process Behavior: Utilize EDR and Security Information and Event Management (SIEM) solutions to monitor for unusual process behavior. Look for instances where legitimate processes like Narrator load unexpected DLLs, or initiate outbound connections to unusual destinations.
- Application Whitelisting: Implement application whitelisting to control which applications and DLLs are permitted to execute on your systems. This can prevent unauthorized malicious DLLs from being loaded.
Relevant Tools for Detection and Mitigation
Leveraging the right tools is critical for identifying and defending against DLL hijacking attempts.
| Tool Name | Purpose | Link |
|---|---|---|
| Microsoft Process Monitor | Real-time file system, Registry, and process/thread activity monitoring. Essential for observing DLL loading. | https://docs.microsoft.com/en-us/sysinternals/downloads/procmon |
| Sysmon | Collects detailed information about process creations, network connections, and changes to file creation time. Useful for detecting suspicious activity. | https://docs.microsoft.com/en-us/sysinternals/downloads/sysmon |
| Endpoint Detection & Response (EDR) Solutions | Advanced threat detection, investigation, and response capabilities. Many EDRs can detect malicious DLL injections. | (Vendor Specific – e.g., CrowdStrike Falcon, Microsoft Defender ATP) |
| Application Whitelisting Solutions | Controls which applications and executables can run on a system, preventing unauthorized DLLs. | (Vendor Specific – e.g., Microsoft AppLocker, Carbon Black App Control) |
Key Takeaways
The persistent vulnerability within the Windows Narrator, facilitated by DLL hijacking, serves as a stark reminder that even trusted system components can be weaponized. Attackers continuously seek avenues for stealthy persistence and lateral movement, and vulnerabilities like this provide them with potent tools. Organizations must prioritize robust patching, adhere to the principle of least privilege, and implement advanced monitoring solutions to detect and prevent such sophisticated attacks. Proactive security posture, coupled with a deep understanding of attack techniques, remains the best defense against these evolving threats.