Hackers Exploiting Cisco IOS XE Vulnerability in the Wild to Deploy BADCANDY Web Shell
Urgent Threat: BADCANDY Web Shell Exploits Cisco IOS XE Vulnerability in the Wild
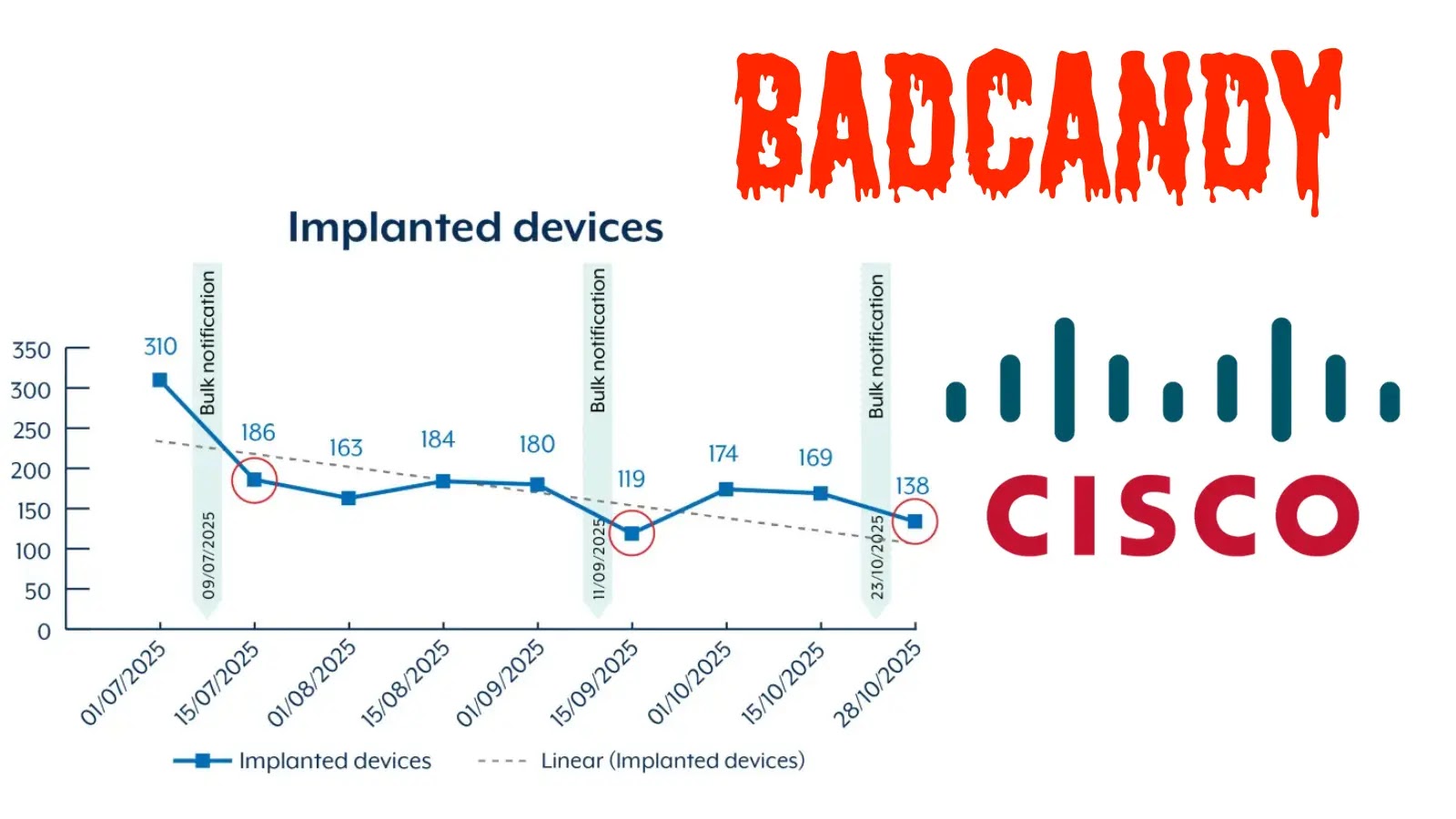
Cybersecurity practitioners worldwide are on high alert as sophisticated threat actors, including both cybercriminals and state-sponsored groups, are actively leveraging a critical vulnerability in Cisco IOS XE devices. These attackers are deploying a persistent Lua-based web shell known as BADCANDY to establish and maintain unauthorized access, particularly targeting unpatched systems across Australia and beyond. This escalating campaign underscores the immediate need for robust defensive measures and patch management.
Understanding the Threat: CVE-2023-20198 and BADCANDY
The core of this attack vector lies in the exploitation of CVE-2023-20198, a critical vulnerability impacting Cisco IOS XE software. This flaw allows unauthenticated remote attackers to create an account with privilege level 15, effectively granting them full administrative control over the affected device. Once this initial access is gained, attackers proceed to deploy the BADCANDY web shell.
BADCANDY is a Lua-based implant designed for persistence and control. First observed in various iterations since October 2023, its renewed and widespread exploitation throughout 2024 and extending into 2025 demonstrates its effectiveness and the ongoing threat it poses. This web shell provides attackers with a backdoor, enabling them to execute arbitrary commands, exfiltrate data, and further compromise the network infrastructure without immediate detection.
Tactics and Targets: Why Cisco IOS XE Devices Are Lures
Cisco IOS XE devices are critical components of enterprise and service provider networks, often acting as routers, switches, and wireless controllers. Their pervasive deployment makes them attractive targets for adversaries aiming to gain a foothold deep within an organization’s network. By compromising these devices, attackers can:
- Establish a persistent presence that survives reboots.
- Monitor network traffic and bypass existing security controls.
- Launch further attacks against internal systems.
- Exfiltrate sensitive data.
- Disrupt network operations.
The targeting of unpatched systems highlights a common attack pattern where adversaries capitalize on organizations that lag in their patching cycles. The geographic focus on Australia, as noted in recent analyses, serves as a stark reminder that these threats are global and constantly adapting.
Remediation Actions: Securing Your Cisco IOS XE Infrastructure
Given the active exploitation of CVE-2023-20198 and the presence of the BADCANDY web shell, immediate and decisive action is paramount for any organization utilizing Cisco IOS XE devices.
- Patch Immediately: The most critical step is to apply the security patches released by Cisco to address CVE-2023-20198. Refer to Cisco’s official security advisories for specific version requirements.
- Detect and Eradicate BADCANDY: Implement network and endpoint detection tools capable of identifying unusual Lua script activity or the presence of the BADCANDY web shell. Indicators of Compromise (IoCs) related to BADCANDY should be integrated into your detection mechanisms.
- Review User Accounts: Scrutinize all user accounts on Cisco IOS XE devices, specifically looking for new, unauthorized accounts, particularly those with privilege level 15.
- Audit Configuration Changes: Regularly audit device configurations for any unauthorized modifications. Maintain a baseline of known good configurations to quickly identify deviations.
- Implement Strong Access Controls: Enforce multi-factor authentication (MFA) for all administrative access to network devices. Limit access to only necessary personnel and IP addresses.
- Segment Networks: Implement network segmentation to limit the lateral movement of attackers if a device is compromised.
- Monitor Logs: Continuously monitor device logs for suspicious activities, failed login attempts, unusual command executions, and any signs of web shell activity.
Recommended Tools for Detection and Mitigation
| Tool Name | Purpose | Link |
|---|---|---|
| Cisco Security Advisories | Official patching guidance and vulnerability details | Cisco Advisory |
| Network Intrusion Detection/Prevention Systems (NIDS/NIPS) | Detecting anomalous network traffic and known attack patterns | (Vendor-specific, e.g., Cisco Firepower, Snort rules) |
| Security Information and Event Management (SIEM) | Aggregating and analyzing logs for suspicious activity | (Vendor-specific, e.g., Splunk, IBM QRadar) |
| Vulnerability Scanners | Identifying unpatched systems and configuration weaknesses | (Vendor-specific, e.g., Tenable Nessus, Qualys) |
Conclusion
The active exploitation of CVE-2023-20198 by the BADCANDY web shell represents a severe and ongoing threat to organizations relying on Cisco IOS XE devices. Proactive patching, rigorous monitoring, and comprehensive incident response plans are no longer optional but essential. Organizations must prioritize the security of their critical network infrastructure to safeguard against sophisticated adversaries who continue to adapt and scale their attacks.





