New EDR-Redir V2 Blinds Windows Defender on Windows 11 With Fake Program Files
EDR-Redir V2: Blinding Windows Defender with Novel Redirection Loops
Endpoint Detection and Response (EDR) systems are the frontline guardians of modern enterprise security, designed to detect and mitigate threats in real-time. Yet, even the most sophisticated EDR solutions can be vulnerable to clever evasion techniques. A recent development, EDR-Redir V2, has demonstrated a concerning ability to blind Windows Defender on Windows 11 by exploiting fundamental aspects of how the operating system handles file paths. This upgraded tool presents a novel method for threat actors to operate undetected, highlighting the constant evolution of cyber threats.
Understanding the Evasion Mechanism of EDR-Redir V2
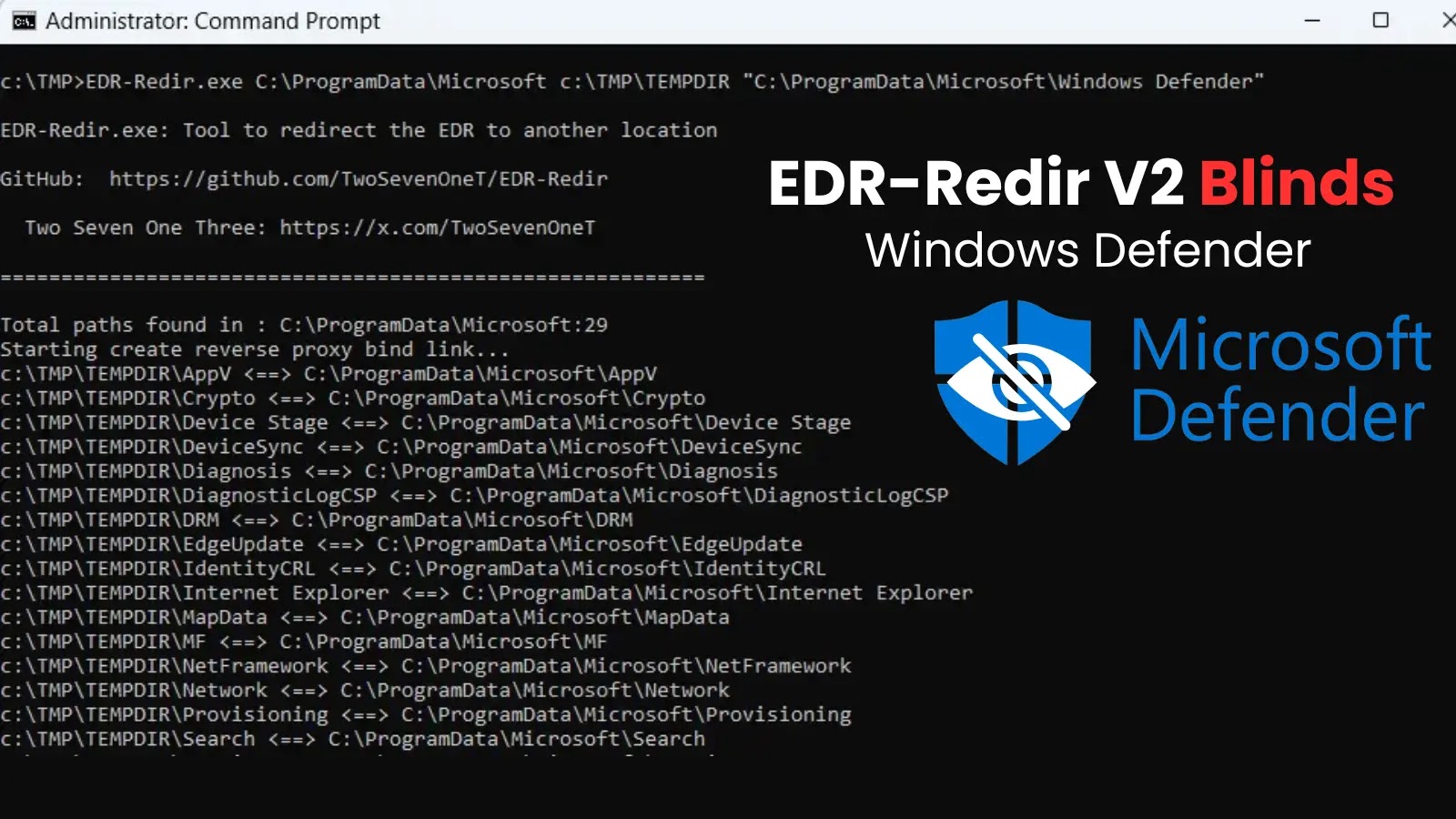
At its core, EDR-Redir V2 leverages Windows bind link technology, a feature often used for legitimate system operations, to create deceptive redirection loops. The researcher TwoSevenOneT, who developed this updated version, revealed that EDR-Redir V2 focuses its attack on the parent directories of EDR installations. Specifically, it targets common locations like the Program Files directory.
The ingenious aspect of this technique lies in its subtlety. By creating these redirection loops, EDR-Redir V2 effectively misdirects security software, including Windows Defender, causing it to lose visibility into critical system areas. This “blinding” occurs without disrupting the legitimate functions of the EDR system itself, making the evasion harder to detect. The security software believes it is monitoring the intended location, but in reality, it’s caught in an endless loop or redirected to a benign, fake directory, allowing malicious activities to proceed unnoticed in the true intended location.
Technical Deep Dive: How Bind Links Create Blind Spots
Windows bind links, technically known as NTFS junction points or symbolic links, allow a directory to point to another location on the file system. While powerful for system administration, EDR-Redir V2 weaponizes this functionality. Imagine an EDR system monitoring the C:\Program Files\EDR_Vendor\ directory for suspicious activity. EDR-Redir V2 might create a bind link at C:\Program Files\ that redirects any queries about C:\Program Files\EDR_Vendor\ to a benign, fabricated directory like C:\Fake_Program_Files\EDR_Vendor\. When the EDR system attempts to scan or monitor its own installation path, it is inadvertently sent down a rabbit hole to a location containing no malicious files, while the real EDR installation remains vulnerable and potentially compromised or bypassed.
This method is particularly effective against Windows Defender on Windows 11 because it exploits how the operating system resolves file paths and how security software perceives those paths. The current implementation of Windows Defender, in the context of this vulnerability, does not appear to adequately handle or anticipate such sophisticated bind link manipulation when monitoring critical system directories.
Impact on Windows Defender and System Security
The successful deployment of EDR-Redir V2 means that Windows Defender, a built-in and widely used EDR solution, can be rendered ineffective in detecting threats that operate within its blind spots. This dramatically increases the risk of successful cyberattacks, as initial compromise can go unnoticed, enabling lateral movement, data exfiltration, or the deployment of ransomware without immediate security intervention.
For organizations relying heavily on Windows Defender as their primary EDR, this finding is particularly critical. It underscores the necessity of a multi-layered security approach and the continuous evaluation of EDR capabilities against evolving evasion techniques.
Remediation Actions and Mitigations
While a direct patch for this specific bind link exploitation might be pending from Microsoft, organizations can take several proactive steps to bolster their defenses:
- Implement Advanced EDR/XDR Solutions: While EDR-Redir V2 targets Windows Defender, more advanced EDR or Extended Detection and Response (XDR) solutions often incorporate broader telemetry, behavioral analysis, and anomaly detection that might identify the creation of suspicious bind links or the unusual behavior associated with their exploitation.
- Regular File System Integrity Monitoring: Deploy tools that continuously monitor critical system directories (like
C:\Program Files) for unauthorized modifications, including the creation or alteration of bind links. Tools that can detect changes in NTFS junction points or symbolic links are crucial. - Principle of Least Privilege: Enforce strict least privilege principles. Restrict administrative access and the ability to create bind links to only essential personnel and automated processes. Reduce the attack surface by limiting what accounts can modify system directories.
- Enhanced Logging and Auditing: Ensure comprehensive logging for file system changes, especially within sensitive directories. Regularly review logs for unusual activity, specifically events related to creating or modifying symbolic links or junction points.
- Network Segmentation: Segment your network to limit the blast radius of any successful evasion. If an endpoint is compromised, network segmentation can prevent attackers from easily moving to other systems.
- Zero Trust Architecture: Adopt a Zero Trust security model. Assume breach and verify every access request, regardless of whether it originates inside or outside the network. This can help detect and mitigate threats even if an EDR system is temporarily blinded.
- Stay Informed: Keep abreast of the latest cybersecurity threats and vulnerabilities. Monitor advisories from Microsoft and security researchers regarding new evasion techniques.
Conclusion
The emergence of EDR-Redir V2 serves as a stark reminder that the cat-and-mouse game between defenders and attackers continues relentlessly. By ingeniously leveraging Windows bind link technology, this tool highlights a gap in current Windows Defender’s ability to maintain full visibility in the face of sophisticated evasion. Organizations must recognize the implications of such techniques and proactively adopt a robust, multi-faceted security strategy that extends beyond relying on a single EDR solution. Continuous vigilance, advanced threat detection capabilities, and stringent security hygiene are paramount to defending against these evolving threats.





