October Sees Rise in Phishing and Ransomware Attacks, Including TyKit and Google Careers Scams
The digital landscape is a battleground, and October 2025 served as a stark reminder of its escalating intensity. Cybercriminals launched a significant surge in phishing and ransomware attacks, weaponizing trusted cloud services and sophisticated new tactics to compromise corporate credentials and critical infrastructure. This rise in threats, highlighted by the active exploitation of platforms like Google, Figma, and ClickUp, alongside the evolution of ransomware variants like LockBit, demands immediate attention from security professionals.
The Escalation of Phishing Campaigns
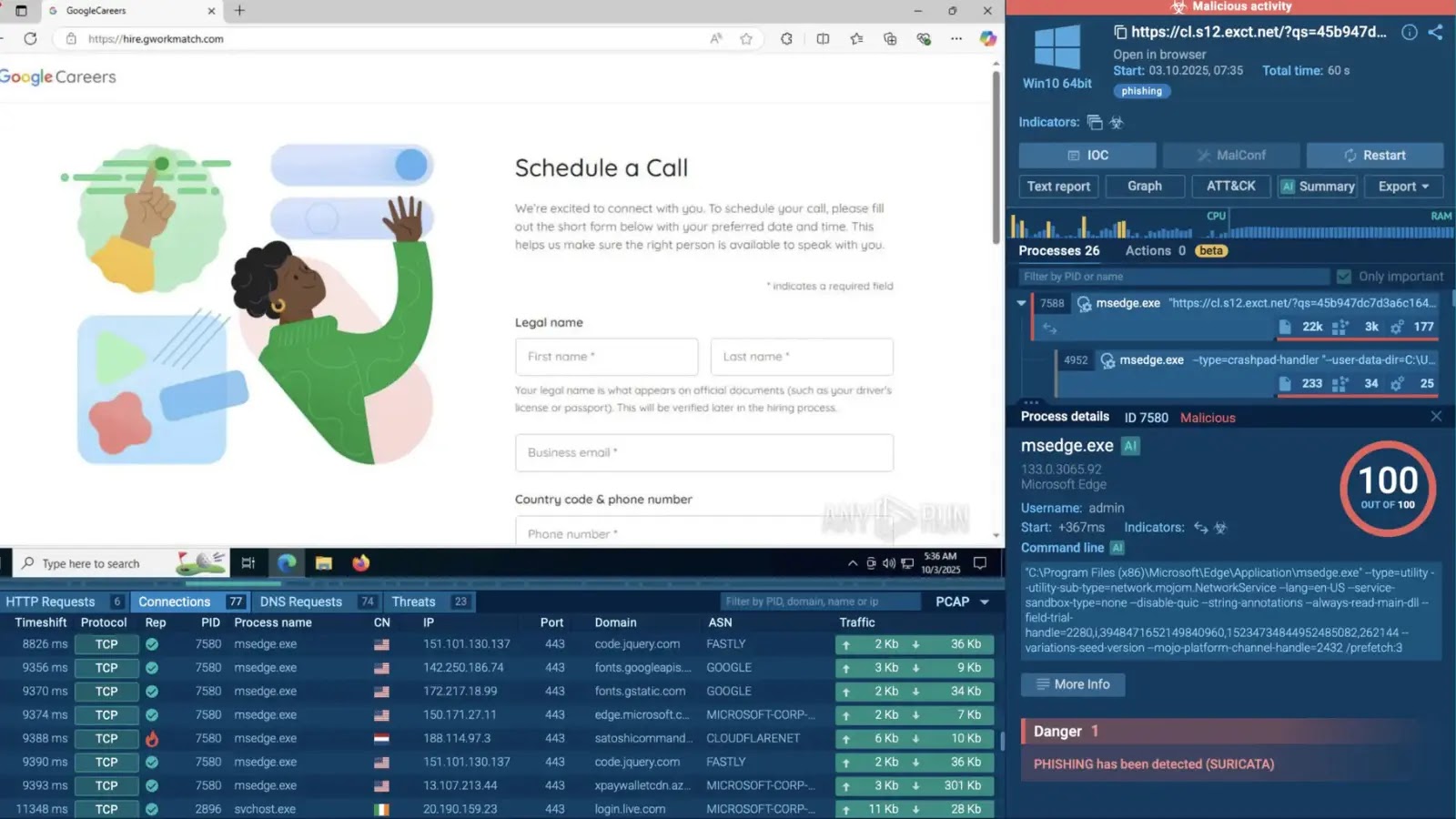
October witnessed a marked increase in phishing campaigns, with attackers keenly focused on credential theft. These campaigns leveraged the perceived trustworthiness of legitimate cloud services, making detection and prevention particularly challenging. Google, a ubiquitous platform for businesses and individuals alike, was a prime target. Phishing scams masquerading as legitimate Google services, including malicious “Google Careers” lures, tricked unsuspecting users into divulging sensitive login information.
Beyond Google, other popular collaboration and development platforms were similarly abused. Attackers utilized Figma, a widely used design and prototyping tool, and ClickUp, a project management solution, to host malicious content or send deceptive communications. This tactic of weaponizing legitimate infrastructure allows threat actors to bypass traditional email security filters and exploit user trust in familiar services.
Ransomware’s Evolving Threat Landscape
Ransomware continues to be a dominant and destructive force in the cyber threat arena. October’s surge saw the latest iterations of established ransomware families, including LockBit, expanding their capabilities and reach. A particularly concerning development is LockBit’s adaptation to target virtualized environments. This evolution means that organizations heavily reliant on virtual machines for their infrastructure are now at an even greater risk of widespread disruption and data encryption.
These sophisticated ransomware attacks often initiate through initial access brokers (IABs) who gain unauthorized access to networks, sometimes via successful phishing campaigns, before selling that access to ransomware operators. The ultimate goal, as always, is to encrypt critical data and demand substantial ransom payments, often in cryptocurrency, with the threat of data leakage if demands are not met.
TyKit: A New Element in the Threat Matrix
While the provided source specifically mentions “TyKit” in the title, details about this particular threat were not extensively elaborated upon in the linked content. However, the inclusion of such a specialized term implies the emergence or increased prominence of new or niche attack frameworks and toolkits. These kits typically streamline the process for less sophisticated attackers, enabling them to launch complex campaigns with relative ease. The rise of such tools suggests a broader democratization of cyberattack capabilities, making it imperative for organizations to stay abreast of emerging threats, even those not yet widely detailed.
Remediation Actions for a Hardened Defense
- Strengthen Phishing Defenses: Implement robust email security gateways with advanced threat protection, sandboxing, and URL rewriting capabilities. Educate employees on identifying phishing attempts, including those utilizing trusted cloud services.
- Multi-Factor Authentication (MFA): Enforce MFA across all corporate accounts, especially for cloud services like Google, Figma, and ClickUp. This significantly reduces the impact of stolen credentials.
- Endpoint Detection and Response (EDR): Deploy EDR solutions to monitor endpoints for suspicious activity, detect early signs of compromise, and enable rapid incident response.
- Regular Backups: Maintain frequent, isolated, and tested backups of all critical data. Ensure backups are stored offline or in secure, segregated environments to prevent ransomware encryption.
- Patch Management: Proactively patch and update all operating systems, applications, and firmware to mitigate known vulnerabilities.
- Network Segmentation: Segment networks to limit the lateral movement of attackers in the event of a breach. This can contain ransomware outbreaks and reduce the blast radius.
- Incident Response Plan: Develop and regularly test a comprehensive incident response plan, including procedures for ransomware attacks and data breaches.
- Employee Training: Conduct regular and engaging security awareness training, focusing on current threats like phishing and social engineering.
- Supply Chain Security: Vet third-party vendors and their security postures, especially those providing cloud services or software, as they can represent an indirect attack vector.
Key Takeaways and Forward Outlook
The October 2025 cyber threat landscape underscores a critical shift: attackers are increasingly leveraging trusted, legitimate platforms to conduct malicious activities. The rise in phishing campaigns targeting corporate credentials through services like Google, Figma, and ClickUp, coupled with the evolving sophistication of ransomware like LockBit, paints a clear picture of persistent and adaptable adversaries.
Organizations must move beyond traditional perimeter defenses and adopt a holistic, multi-layered security strategy. Proactive measures, continuous monitoring, and robust incident response capabilities are no longer optional but essential for safeguarding digital assets in this challenging environment.





