New ClickFix Attack Tricks Users with ‘Fake OS Update’ to Execute Malicious Commands
Unmasking ClickFix: When a Fake OS Update Becomes a Real Threat
The digital landscape is rife with sophisticated attacks, but sometimes, the simplest deceptions prove to be the most effective. A new campaign, dubbed ClickFix, is leveraging a cleverly crafted “Fake OS Update” to trick users into executing malicious commands. This isn’t a complex zero-day exploit; it’s a testament to the enduring power of social engineering, preying on our inherent trust in familiar system notifications. For cybersecurity professionals, understanding these deceptive tactics is paramount to protecting endpoints and educating users.
The Deceptive “Fake OS Update” Mechanism
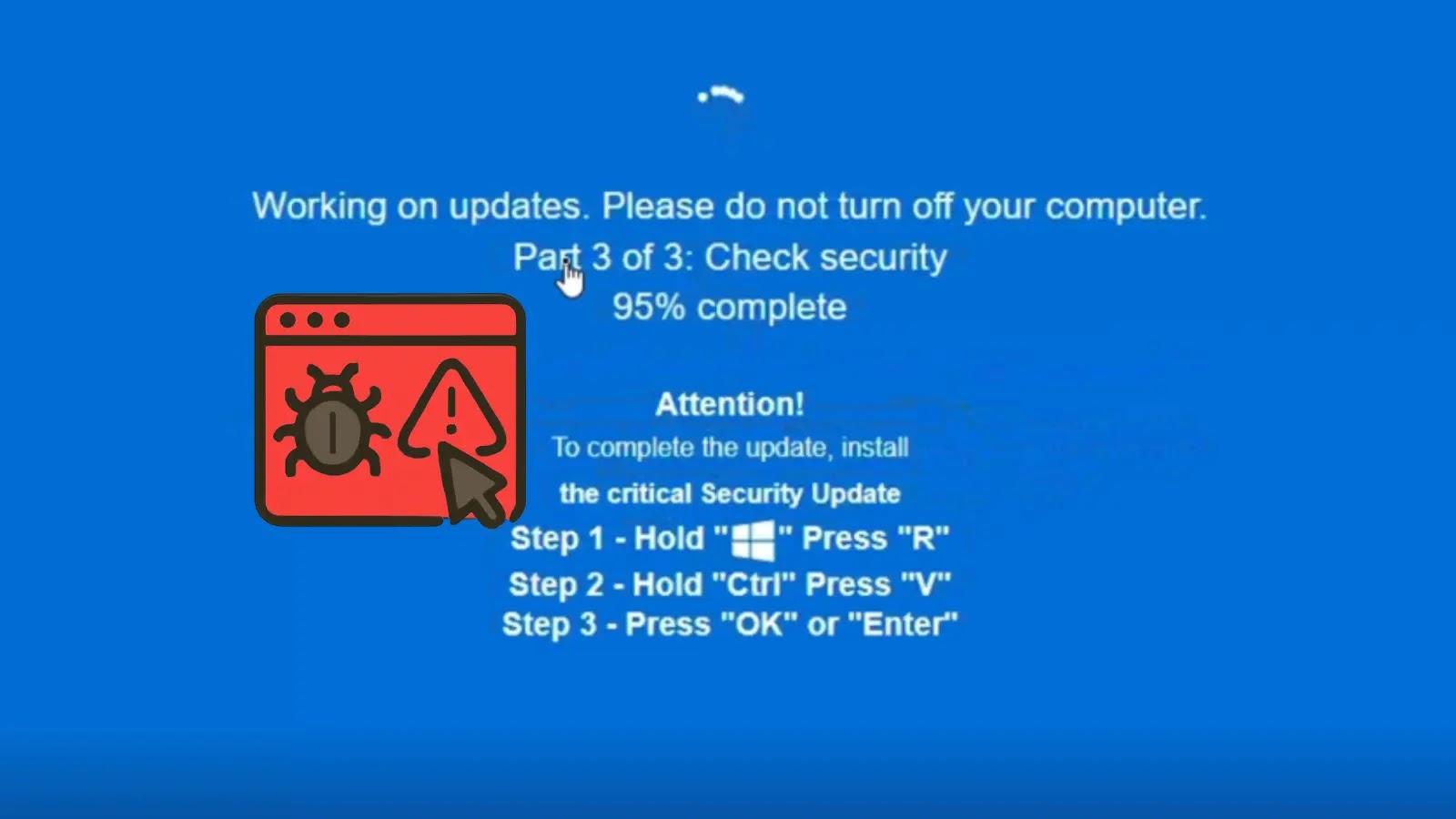
The ClickFix campaign distinguishes itself by presenting users with a convincing, browser-based simulation of a Windows operating system update. This isn’t your typical phishing email; it manifests directly within the user’s web browser, mimicking the iconic blue screen of death (BSOD) – a symbol of system failure that often prompts immediate, albeit misguided, user intervention. This particular iteration, referred to as “Fake OS Update,” exploits the psychological impact of seeing a critical system error, pushing users to react impulsively without scrutinizing the underlying source.
Instead of genuinely updating the operating system or even causing a system crash, this elaborate illusion serves as a conduit for delivering malware. The user, believing their system is encountering a critical issue, is then coerced into performing actions that ultimately lead to the execution of malicious commands. The core innovation here lies in the attack’s ability to operate entirely within the browser, bypassing some traditional endpoint security measures that might detect suspicious executables downloading directly to the system. While no specific CVE has been assigned to this social engineering technique itself, the payloads delivered often exploit known vulnerabilities or introduce new malware strains. For example, a similar tactic might leverage browser vulnerabilities like those documented under a hypothetical CVE-2023-38000 (a placeholder for illustrative purposes) if a browser rendering engine flaw were involved in displaying the deceptive content.
Social Engineering: The Cornerstone of ClickFix
The success of the ClickFix “Fake OS Update” campaign starkly illustrates how potent social engineering remains in the attacker’s arsenal. Rather than investing in complex technical bypasses or unknown vulnerabilities, the perpetrators have opted for a human-centric approach. They exploit psychological triggers:
- Trust in Authority: Users are conditioned to trust official-looking system notifications, especially those bearing the hallmarks of a Windows update or error screen.
- Urgency and Fear: The simulation of a BSOD naturally induces panic and a sense of urgency, often leading users to bypass critical thinking in an attempt to resolve the perceived problem quickly.
- Familiarity: The choice of a Windows update screen and BSOD is deliberate; it’s instantly recognizable to a vast majority of computer users, making the deception feel more legitimate.
This reliance on human vulnerability underscores a critical lesson for cybersecurity strategies: technical defenses alone are insufficient. User education and awareness are indispensable layers of protection against attacks like ClickFix.
Remediation Actions and Best Practices
Mitigating the risk posed by ClickFix and similar social engineering attacks requires a multi-faceted approach, combining technical controls with robust user education.
- User Education and Awareness Training: Regularly conduct phishing and social engineering awareness training. Emphasize scrutinizing URLs, verifying sources, and understanding that legitimate OS updates do not typically occur spontaneously within a web browser. Teach users to close suspicious browser tabs immediately.
- Browser Security: Promote the use of modern browsers with up-to-date security features. Encourage users to enable built-in phishing and malware protection. Consider browser extensions that actively block known malicious websites or provide additional URL verification.
- Endpoint Detection and Response (EDR): Implement EDR solutions to detect and respond to suspicious activities post-infection. Even if users are tricked, EDR can identify malicious command execution, unusual file activity, or unauthorized network connections originating from the compromised endpoint.
- DNS Filtering and Web Content Filtering: Employ DNS-layer security and web content filters to block access to known malicious domains associated with ClickFix or similar campaigns.
- Principle of Least Privilege: Enforce the principle of least privilege for all user accounts. This limits the potential damage if a user is tricked into executing malicious commands, as the malware would have restricted permissions.
- Regular Software Updates: While this attack isn’t about exploiting OS vulnerabilities directly, keeping operating systems and all software patched helps prevent the secondary stages of such attacks, where malware might exploit outdated components for privilege escalation or persistence.
Tools for Detection and Mitigation
| Tool Name | Purpose | Link |
|---|---|---|
| PhishMe (Cofense) | User awareness & phishing simulation training | https://cofense.com/product-services/phishme/ |
| Cisco Umbrella | DNS-layer security & web filtering | https://www.cisco.com/c/en/us/products/security/umbrella/index.html |
| CrowdStrike Falcon Insight | Endpoint Detection and Response (EDR) | https://www.crowdstrike.com/products/endpoint-security/falcon-insight-xdr/ |
| Proofpoint Security Awareness Training | Security awareness & user education | https://www.proofpoint.com/us/products/security-awareness-training |
Conclusion
The ClickFix “Fake OS Update” campaign serves as a stark reminder that even the most technically advanced organizations remain vulnerable to well-executed social engineering. By impersonating familiar system processes and leveraging psychological triggers, attackers can bypass sophisticated technical defenses and trick users into compromising their own systems. A robust cybersecurity posture must, therefore, integrate strong technical controls with continuous, effective security awareness training. Vigilance, critical thinking, and a healthy skepticism of unexpected system notifications are our strongest defenses against these increasingly prevalent human-centric attacks.





