SilentButDeadly – Network Communication Blocker Tool That Neutralizes EDR/AV
The ever-escalating arms race between cyber defenders and attackers recently saw a new development with the emergence of SilentButDeadly. This open-source tool introduces a novel method for attackers to neutralize Endpoint Detection and Response (EDR) and antivirus (AV) solutions by selectively severing their network communications. Understanding its operational mechanics, implications, and potential countermeasures is critical for maintaining robust cybersecurity postures.
Understanding SilentButDeadly: A New Threat Vector
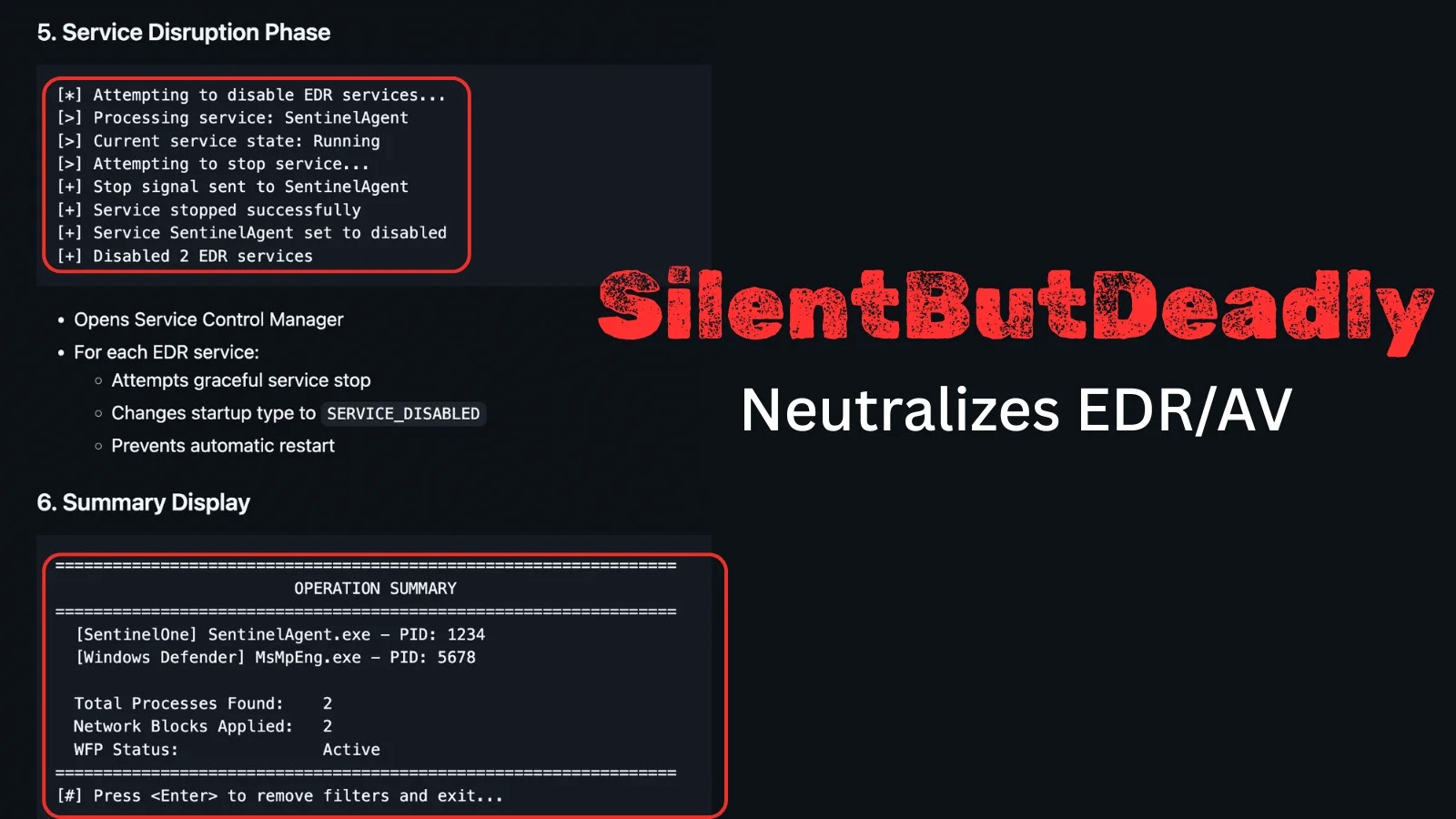
Developed by security researcher Ryan Framiñán, SilentButDeadly leverages the Windows Filtering Platform (WFP) to create temporary, bidirectional communication blocks. Unlike traditional methods that aim to terminate EDR/AV processes directly, SilentButDeadly focuses on isolating these critical security tools from their cloud-based command-and-control infrastructure. This isolation prevents EDRs from receiving updates, sending telemetry, or performing real-time threat analysis, effectively rendering them blind and inert. The tool is designed to be stealthy, operating without raising immediate flags that a direct process termination might trigger.
The core innovation lies in its use of WFP, a set of API-based services built into Windows that allows developers to create network filtering applications. By integrating malicious filtering rules, SilentButDeadly can precisely target and disrupt the communication channels used by EDR and AV software, often without requiring administrative privileges for the initial execution.
How SilentButDeadly Operates
SilentButDeadly’s operational model focuses on network layer manipulation rather than process manipulation. Here’s a breakdown of its key operational aspects:
- Windows Filtering Platform (WFP) Exploitation: The tool creates dynamic filtering rules within WFP, which is a powerful and legitimate Windows networking component. These rules are designed to specifically block outbound and inbound connections associated with known EDR/AV processes or cloud services.
- Bidirectional Communication Blockade: It doesn’t just prevent data from leaving the endpoint; it also blocks incoming communications, ensuring complete isolation. This means EDRs cannot receive new policy updates or threat intelligence.
- Temporary & Reversible Disruption: A key aspect of its design is the temporary nature of the block. This allows attackers to perform malicious activities while the EDR is hobbled, and then potentially remove the block to delay detection, assuming the EDR service continues to run.
- Process Isolation, Not Termination: Crucially, SilentButDeadly does not attempt to terminate EDR or AV processes. This approach is designed to evade detection mechanisms that alert on unexpected process shutdowns or modifications to security software.
Implications for EDR/AV Effectiveness
The emergence of SilentButDeadly presents significant challenges for endpoint security:
- Blinding Critical Telemetry: EDR solutions rely heavily on sending telemetry data to cloud-based analysis engines for real-time threat detection and long-term behavioral analysis. Blocking this communication starves the system of vital intelligence.
- Preventing Real-time Remediation: Without communications, EDRs cannot receive new instructions or execute remediation actions initiated from the cloud console (e.g., isolating a host, killing a process).
- Difficulty in Detection: Since the EDR process continues to run, albeit in an isolated state, traditional health checks focusing solely on process existence might not immediately flag an issue.
- Escalation Path for Attackers: By neutralizing EDRs, attackers gain a critical window to execute subsequent stages of an attack, such as lateral movement, data exfiltration, or ransomware deployment, without immediate security intervention.
Remediation Actions and Mitigations
Addressing the threat posed by tools like SilentButDeadly requires a multi-layered defensive strategy. Organizations must consider both proactive and reactive measures:
- Network Segmentation and Micro-segmentation: Implement strict network segmentation to limit the blast radius of a compromised endpoint. Micro-segmentation for critical assets can further restrict unauthorized communications, even if an EDR is temporarily blinded.
- Proactive WFP Monitoring: Implement solutions that continuously monitor for unauthorized modifications to the Windows Filtering Platform rules. Any new, suspicious, or unexpected WFP rules should trigger immediate alerts.
- Host-Based Firewall Policies: Configure stringent host-based firewall policies that explicitly whitelist necessary EDR/AV communications and deny all other outbound connections unless explicitly permitted. This can prevent unauthorized WFP rule modifications from achieving their goal.
- Out-of-Band Monitoring for EDR Health: Beyond relying on the EDR itself for its health status, implement independent, out-of-band monitoring solutions that can verify the connectivity and operational status of EDR agents (e.g., checking for recent telemetry uploads, last check-in times).
- Integrity Monitoring of WFP: Utilize file and registry integrity monitoring tools that specifically track changes to WFP configurations and associated registry keys.
- Advanced Behavioral Analytics: While EDRs might be blinded to cloud communication, a strong behavioral analytics platform on the endpoint could still detect the malicious activity that SilentButDeadly is designed to facilitate, even if the EDR itself cannot report it immediately.
- Regular Security Audits and Penetration Testing: Conduct regular security audits and penetration tests that specifically include scenarios where EDR/AV communications are disrupted to assess the effectiveness of current controls.
The Ongoing Battle for Endpoint Security
SilentButDeadly serves as a stark reminder of the continuous innovation in the adversarial landscape. Attackers are constantly seeking novel ways to bypass established security controls, forcing defenders to adapt and evolve. The focus on network-level disruption rather than process termination highlights the need for a holistic security approach that extends beyond traditional endpoint protection to include robust network visibility, integrity monitoring, and adaptive defense strategies.
Securing endpoints effectively requires a deep understanding of the underlying operating system mechanisms that attackers can leverage. As tools like SilentButDeadly become more prevalent, the ability to monitor and control low-level system APIs like WFP will become increasingly vital for effective cyber defense.





