Phishing Breaks More Defenses Than Ever. Here’s the Fix
Your security tools flag a link as clean. Do you trust it implicitly? Many Security Operations Center (SOC) leaders no longer do, and for a critical reason. Phishing has evolved; it’s sophisticated, subtle, and meticulously crafted to blend into the relentless flow of daily digital communication. It bypasses conventional filters, silently infiltrates inboxes, and only reveals its malicious intent after a user engages. By the time the true nature of the attack becomes apparent, your established defenses have often already been compromised.
The Evolving Threat Landscape of Phishing
Traditional phishing detection mechanisms increasingly struggle against modern attack vectors. Attackers now leverage highly personalized spear-phishing campaigns, sophisticated spoofing techniques, and even compromised legitimate accounts to deliver their payloads. The efficacy of these new methods is alarming, leading to a significant increase in successful breaches despite robust security infrastructure.
Key observations on modern phishing:
- Polished Presentation: Phishing emails and websites are virtually indistinguishable from legitimate communications. They mimic branding, language, and user experience with alarming accuracy.
- Quiet Infiltration: Attackers often use newly registered domains, compromised subdomains of trusted entities, or intricate URL redirects to evade URL reputation services and content filters.
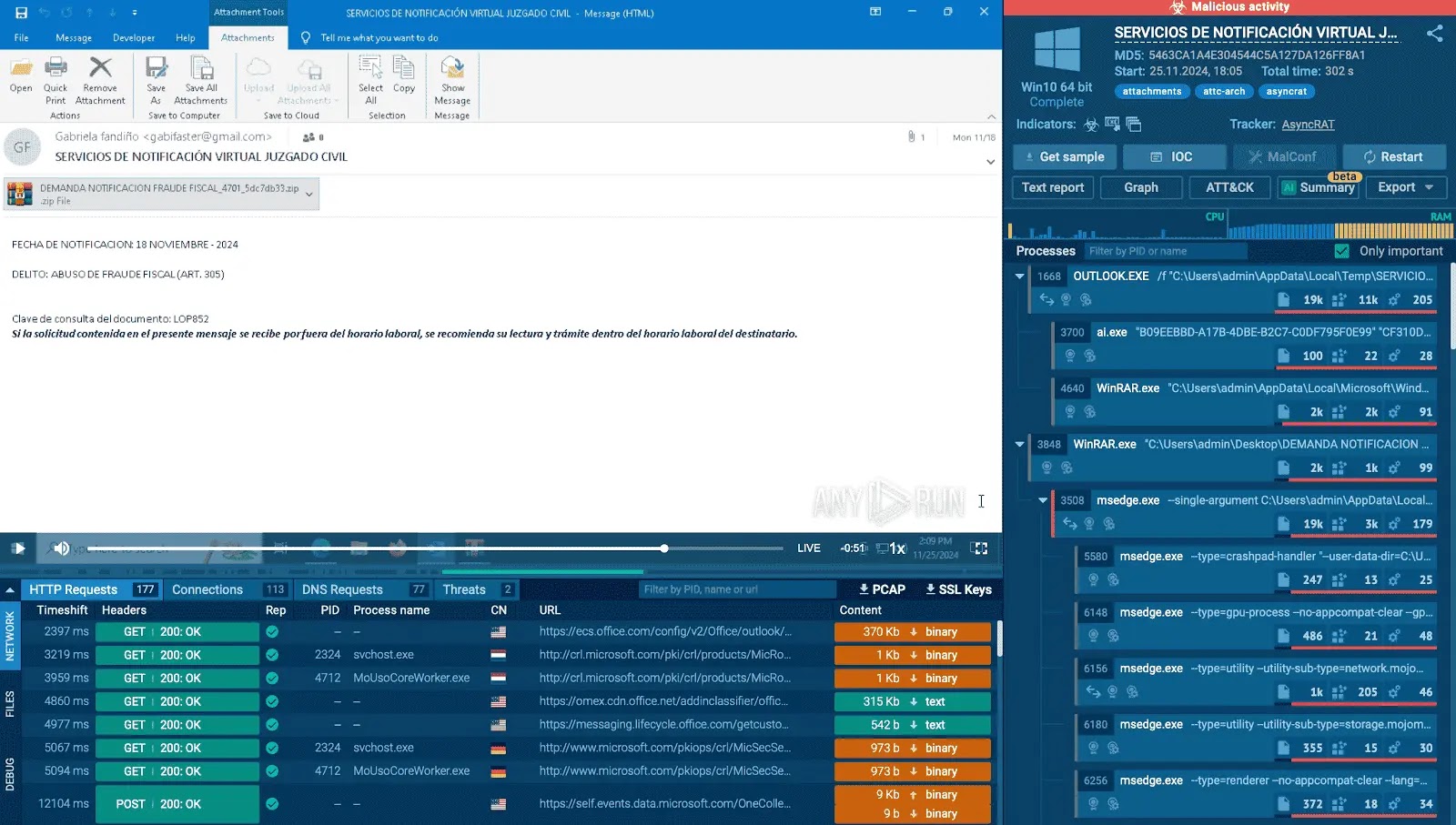
- Blended Tactics: Phishing frequently combines with other attack types, such as malware delivery or credential harvesting, making it a multi-faceted threat. For instance, a seemingly harmless link might lead to a drive-by download exploit (e.g., leveraging vulnerabilities like CVE-2023-38829 in WinRAR or CVE-2023-23397 in Outlook) or a meticulously crafted fake login page.
- Post-Interaction Malice: The true danger often manifests only after a user clicks a link, opens an attachment, or inputs credentials, by which point the initial defensive layers have been bypassed.
Why Current Defenses Fall Short
Many organizations rely heavily on perimeter defenses and signature-based detection. While essential, these are often insufficient against advanced phishing:
- Signature Limitations: New phishing campaigns constantly emerge, making signature-based detection reactive rather than proactive.
- Sandboxing Evasion: Sophisticated phishers can detect sandboxed environments and alter their behavior to appear benign until deployed in a live user environment.
- User as the Weakest Link: Ultimately, phishing exploits human psychology. Even the most technologically advanced defenses can be circumvented if an employee falls victim to social engineering.
- Supply Chain Vulnerabilities: Phishing can originate from compromised third-party vendors or partners, bypassing internal security controls entirely.
Remediation Actions: Fortifying Against Advanced Phishing
Addressing the evolved phishing threat requires a multi-layered, proactive strategy that combines technology, process, and people.
Technical Controls and Enhancements
- Advanced Email Security Gateways (SEG): Implement SEGs with advanced AI/ML capabilities for anomaly detection, rather than just signature matching. These should analyze sender reputation, behavioral patterns, and email structure deviations.
- Domain-based Message Authentication, Reporting & Conformance (DMARC): Enforce strict DMARC policies (reject or quarantine) to prevent email spoofing of your domains and monitor DMARC reports for potential abuses.
- Browser Isolation/Remote Browser Isolation (RBI): For high-risk users or sensitive browsing, RBI can render web content in a remote, isolated environment, protecting endpoints from malicious code.
- Endpoint Detection and Response (EDR)/Extended Detection and Response (XDR): Deploy EDR/XDR solutions that monitor for post-click malicious activity, such as suspicious process execution, unusual network connections, or unauthorized data access stemming from a phishing compromise.
- Multi-Factor Authentication (MFA): Implement MFA across all critical systems and applications to mitigate the impact of stolen credentials from successful phishing attacks. Hardware tokens are generally more secure than SMS-based MFA.
- DNS Filtering and Web Content Filtering: Block access to known malicious domains and categorize potentially dangerous websites.
- Threat Intelligence Feeds: Integrate real-time threat intelligence feeds into your security tools to stay updated on emerging phishing campaigns and indicators of compromise (IoCs).
Process and Policy Improvements
- Regular Security Awareness Training (SAT): Conduct frequent, engaging, and realistic phishing simulations. Educate users on the latest phishing tactics, including spear-phishing, whaling, and QR code phishing (quishing).
- Incident Response Plan (IRP) for Phishing: Develop a clear, well-rehearsed IRP specifically for phishing incidents, detailing steps for detection, containment, eradication, and recovery.
- Least Privilege Access: Ensure users only have the minimum necessary access rights to perform their job functions, limiting the potential damage of a compromised account.
- Software and System Patching: Regularly patch and update all operating systems, applications, and firmware to address known vulnerabilities that attackers could exploit in phishing campaigns. For example, keeping browsers patched against vulnerabilities like CVE-2023-4863 is crucial.
- Email Reporting Mechanism: Provide an easy and conspicuous way for users to report suspicious emails, fostering a culture of active participation in security.
Tools for Detection and Remediation
| Tool Name | Purpose | Link |
|---|---|---|
| Proofpoint Email Protection | Advanced email security gateway, URL/attachment sandboxing, DMARC enforcement. | https://www.proofpoint.com/ |
| Mimecast Email Security | Email security, archiving, continuity, and DMARC enforcement. | https://www.mimecast.com/ |
| KnowBe4 Security Awareness Training | Phishing simulations, security awareness training, and reporting. | https://www.knowbe4.com/ |
| Abnormal Security | Behavioral AI-based email security, focuses on supply chain and internal email compromise. | https://abnormalsecurity.com/ |
| Cloudflare Gateway | DNS filtering, web content filtering, and secure web gateway functionalities. | https://www.cloudflare.com/products/zero-trust/gateway/ |
| Talon Workstation | Enterprise browser with integrated security and browser isolation. | https://talon.us/ |
Conclusion
The landscape of phishing attacks has definitively shifted towards greater sophistication and stealth. Relying solely on perimeter defenses is no longer adequate. Organizations must adopt a holistic, adaptive security strategy that integrates advanced technological controls, robust processes, and continuous employee education. By understanding the evolving tactics of attackers and proactively implementing multi-layered defenses, enterprises can significantly reduce their susceptibility to even the most elusive phishing attempts. The fix isn’t a single solution; it’s a persistent, intelligent combination of people, process, and technology working in concert.





