New “JackFix” Attack Leverages Windows Updates into Executing Malicious Commands
Unmasking JackFix: How Malicious Actors Weaponize Windows Updates
The digital threat landscape is perpetually shifting, with adversaries continually innovating to breach defenses. A new, particularly insidious campaign dubbed “JackFix” has emerged, demonstrating a alarming evolution in social engineering and malware delivery. This sophisticated attack leverages the trusted facade of Windows Update prompts to trick unsuspecting users into executing multistage malware payloads. Understanding the mechanics of JackFix is crucial for bolstering our collective cybersecurity posture.
The Deceptive Lure: Fake Adult Websites and Realistic Prompts
The JackFix campaign initiates its assault through a classic yet effective social engineering tactic: luring victims to fake adult websites. These sites, often meticulously crafted to mimic popular platforms like xHamster, are typically propagated through malvertising on less reputable online platforms. The attackers exploit human curiosity and the allure of illicit content to drive traffic to their phishing pages.
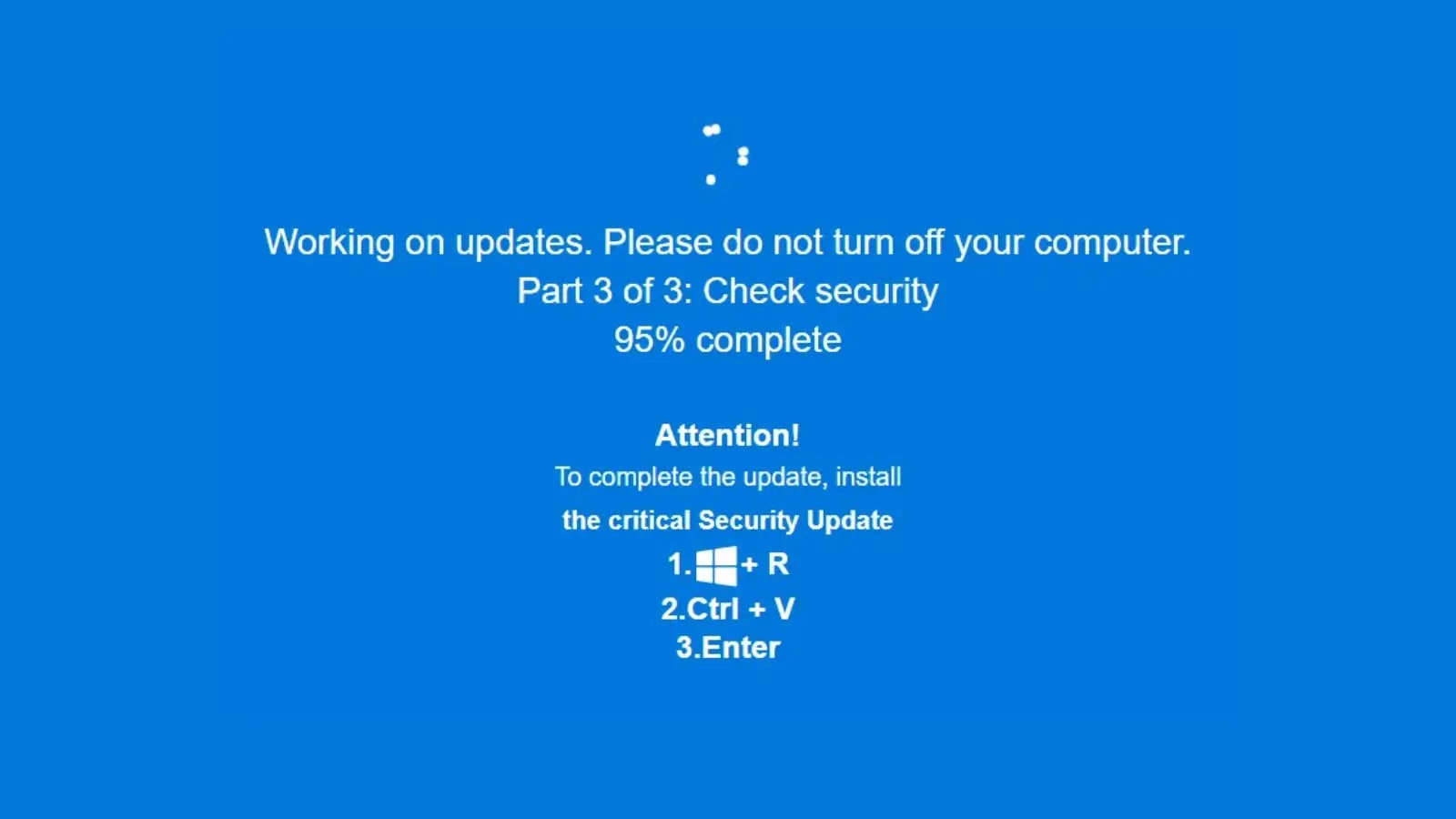
Upon interacting with these deceptive websites, users are immediately confronted with a full-screen overlay designed to perfectly replicate a critical Windows Update prompt. The realism of these prompts is a key factor in JackFix’s success, instilling a sense of urgency and legitimacy that compels users to comply with the instructions.
The Multi-Stage Infection Chain of JackFix
The JackFix attack is not a simple, one-off download. It employs a multi-stage infection process designed for stealth and persistence:
- Initial Compromise: Users, believing they are interacting with a genuine Windows Update, are tricked into downloading and executing an initial malicious file.
- Payload Delivery: This initial file acts as a dropper, secretly downloading and installing further components of the malware. This often includes remote access trojans (RATs) or information stealers.
- Persistence Mechanisms: JackFix often establishes persistence on the compromised system, ensuring that the malware re-launches even after a system reboot. This can involve modifying registry keys or creating scheduled tasks.
- Command and Control (C2): Once established, the malware communicates with attacker-controlled C2 servers, allowing the threat actors to remotely control the infected system, exfiltrate data, or deploy additional malicious tools.
Why Windows Updates are a Potent Attack Vector
The effectiveness of JackFix lies in its exploitation of inherent user trust in familiar system processes. Windows Updates are a critical component of operating system security, regularly delivering patches and enhancements. Users are conditioned to perceive these prompts as legitimate and necessary, making them a prime target for social engineering. The attackers capitalize on this ingrained trust, transforming a vital security mechanism into a powerful vector for compromise.
Remediation Actions and Prevention Strategies
Defending against sophisticated campaigns like JackFix requires a multi-layered approach focusing on technical controls and user education.
- User Education and Awareness:
- Verify Source: Teach users to never click on update prompts or dialogs originating from within a web browser. Genuine Windows Updates are managed through the operating system’s settings, not directly in a browser.
- Hover Before Clicking: Encourage users to hover over links (without clicking) to inspect the URL before proceeding. Malicious sites often use misspelled domain names or unrelated domains.
- Be Wary of Urgency: Phishing attacks often create a false sense of urgency. Advise users to be skeptical of any prompt demanding immediate action.
- Technical Controls:
- Endpoint Detection and Response (EDR): Implement robust EDR solutions that can detect and prevent the execution of malicious files, even if they bypass traditional antivirus.
- Next-Generation Antivirus (NGAV): Ensure NGAV solutions are up-to-date and configured to perform behavioral analysis to identify suspicious process activity.
- Web Content Filtering: Deploy web filters to block access to known malicious and adult websites, mitigating the initial lure.
- Principle of Least Privilege: Limit user privileges to prevent the execution of unauthorized software or changes to critical system settings.
- Regular Patch Management: While JackFix exploits the *idea* of Windows Updates, maintaining a rigorous patching schedule for all software eliminates known vulnerabilities that attackers might silently exploit after initial compromise.
- Network Segmentation: Segment networks to contain potential breaches and limit lateral movement should an infection occur.
- Incident Response Plan: Have a well-defined incident response plan in place to quickly detect, contain, eradicate, and recover from successful attacks.
Detection and Analysis Tools
Effective defense against JackFix relies on proactive monitoring and the use of appropriate security tools:
| Tool Name | Purpose | Link |
|---|---|---|
| VirusTotal | Upload suspicious files for analysis against multiple antivirus engines and threat intelligence sources. | https://www.virustotal.com/ |
| Process Explorer | Advanced task manager to inspect running processes, their parent-child relationships, and loaded modules. | https://learn.microsoft.com/en-us/sysinternals/downloads/processexplorer |
| Wireshark | Network protocol analyzer to capture and inspect network traffic for suspicious C2 communications. | https://www.wireshark.org/ |
| Sysmon | Windows system service and device driver that logs detailed process activity, network connections, and file creation. | https://learn.microsoft.com/en-us/sysinternals/downloads/sysmon |
Conclusion: Heightened Vigilance Against Evolving Threats
The JackFix campaign serves as a stark reminder of the persistent and evolving nature of cyber threats. By weaponizing trusted system prompts and leveraging social engineering, attackers can bypass traditional defenses. Organizations and individuals must prioritize robust security awareness training, implement advanced endpoint protection, and maintain an agile incident response capability. Staying informed about new attack vectors like JackFix is paramount to safeguarding digital assets and preserving online security.





