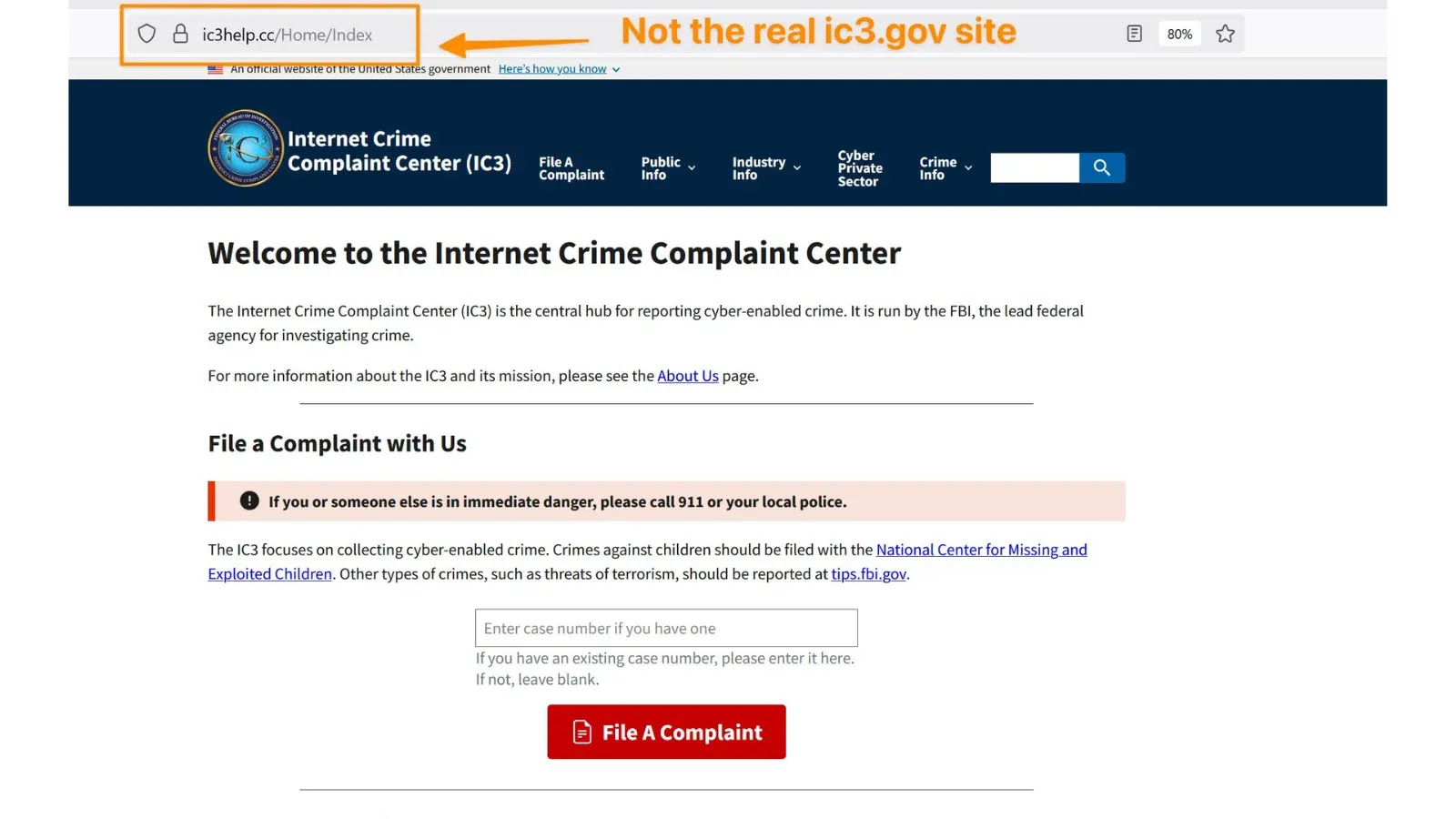
FBI Warns of Fake Internet Crime Complaint Center (IC3) Website Used for Phishing Attacks
The digital landscape is a constant battleground, and even the most trusted entities can be weaponized by cybercriminals. The Federal Bureau of Investigation (FBI) has issued an urgent public warning: malicious actors are now deploying highly sophisticated fake Internet Crime Complaint Center (IC3) websites to harvest sensitive personal data through elaborate phishing campaigns. This isn’t merely a minor inconvenience; it’s a direct assault on the trust users place in official government resources, designed to steal identities and facilitate further cybercrime.
The Deceptive Lure of Fake IC3 Websites
Cybercriminals are masters of mimicry. Their latest tactic involves creating nearly perfect replicas of the legitimate www.ic3.gov portal. These fraudulent sites meticulously borrow content, layout, and visual elements, making them incredibly difficult to distinguish from the real thing. The primary objective is to trick unsuspecting individuals—often victims of other cybercrimes seeking official recourse—into submitting their names, addresses, phone numbers, and other Personally Identifiable Information (PII).
The danger here is manifold. Victims, already stressed from a prior incident, might rush to report a crime and inadvertently provide their personal details directly to the very criminals they are trying to report. This data can then be used for:
- Identity theft.
- Further targeted phishing attacks.
- Financial fraud.
- Social engineering campaigns against the individual or their associates.
How Phishing Attacks Exploit Trust
Phishing remains one of the most effective and pervasive cyberattack vectors. In this scenario, the attackers are leveraging the inherent trust associated with official government agencies. They distribute links to these fake IC3 sites through various channels, including:
- Malicious emails disguised as official notifications from law enforcement.
- SMS messages (smishing) urging recipients to report a crime.
- Compromised websites or social media accounts.
The psychological element is key: individuals seeking help are often more vulnerable and less likely to scrutinize URLs or website legitimacy as closely as they might otherwise.
Remediation Actions and Proactive Defense
Protecting yourself and your organization from these sophisticated phishing attempts requires vigilance and specific security practices. Understanding these and implementing them diligently is paramount.
- Verify URLs: Always double-check the URL of any website asking for personal information. The official IC3 website is www.ic3.gov. Look for “https://” and a padlock icon in the address bar. Be wary of subtle misspellings or extra subdomains.
- Bookmark Official Sites: Instead of clicking links in emails, navigate directly to official websites by typing the URL into your browser or using a trusted bookmark.
- Be Suspicious of Unsolicited Communication: The FBI and other law enforcement agencies typically do not request sensitive personal information via unsolicited emails or SMS messages for crime reporting.
- Educate Yourself and Others: Regularly review best practices for identifying phishing attempts. Share this knowledge with colleagues, friends, and family. Awareness is a powerful defense.
- Use Multi-Factor Authentication (MFA): Where available, enable MFA on all online accounts. Even if credentials are compromised, MFA adds an additional layer of security.
- Report Suspected Phishing: If you encounter a suspicious website or receive a phishing email, report it to the appropriate authorities. For fake IC3 sites, directly inform the FBI.
- Network Monitoring: Organizations should implement robust network monitoring solutions to detect unusual traffic patterns or access attempts to known malicious domains.
- Implement Email Security Gateways: Advanced email security solutions can help filter out phishing emails before they reach end-users.
Detection and Analysis Tools
For security professionals, several tools can aid in detecting and analyzing potential phishing threats and fake websites.
| Tool Name | Purpose | Link |
|---|---|---|
| Brand Protection Services | Monitors for domain spoofing and brand impersonation, identifying fake websites. | (Varies by vendor) |
| PhishTank | Community-based phishing URL verification and reporting. | https://www.phishtank.com/ |
| URLScan.io | Scans and analyzes URLs, providing detailed information about the page, redirects, and linked resources. | https://urlscan.io/ |
| Email Security Gateways | Detects and blocks suspicious emails containing phishing links or malicious attachments. | (e.g., Proofpoint, Mimecast, Microsoft Defender for Office 365) |
| Browser Extensions (e.g., WOT) | Provides real-time warnings about untrustworthy websites. | (Varies by extension) |
Conclusion
The FBI’s warning about fake IC3 websites underscores the relentless adaptability of cybercriminals. Their ability to replicate official government portals with such precision highlights the critical need for constant vigilance and robust security hygiene. It is imperative for individuals and organizations alike to exercise extreme caution when navigating online spaces, particularly when asked for sensitive information. By understanding the tactics involved and implementing proactive defenses, we can collectively diminish the effectiveness of these deceptive phishing campaigns and safeguard our digital identities.





