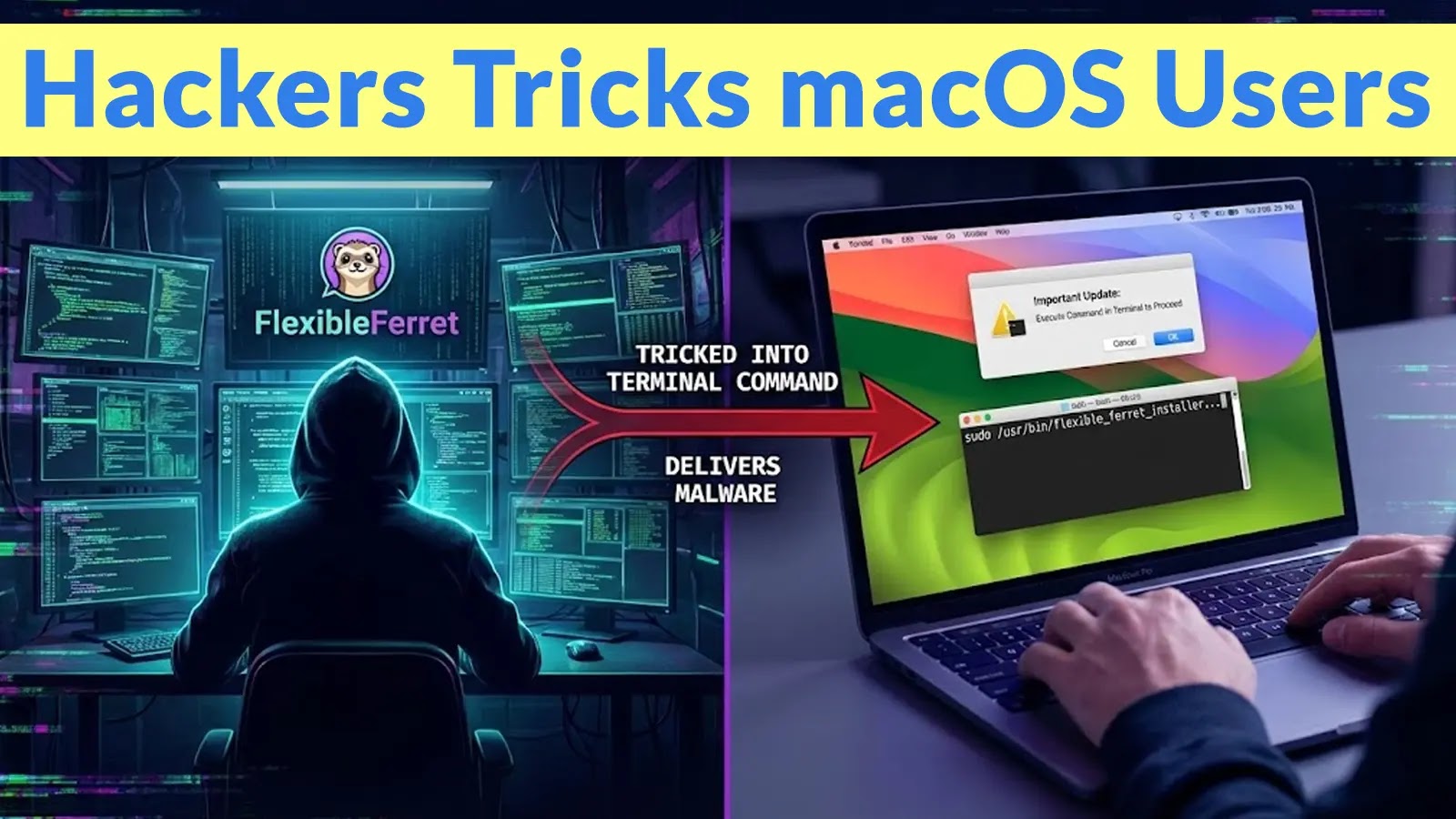
Hackers Tricks macOS Users to Execute Command in Terminal to Deliver FlexibleFerret Malware
A disturbing trend has emerged targeting macOS users: sophisticated social engineering tactics are compelling individuals to execute malicious commands directly within their terminals. This cunning attack vectors the FlexibleFerret malware, a threat attributed to North Korean threat actors. This tactic is a direct continuation of the Contagious Interview campaign, which has persistently operated throughout 2025.
The Evolution of Contagious Interview: FlexibleFerret on macOS
North Korean operators, known for their persistent and evolving cyber warfare strategies, have escalated their attacks on Apple’s macOS ecosystem. The Contagious Interview campaign, a long-standing operation observed through 2025, has introduced a new, particularly insidious malware variant: FlexibleFerret. This malware primarily proliferates through deceptive job offers, leveraging the aspirations of unsuspecting victims.
Social Engineering at Its Core
The success of the FlexibleFerret campaign hinges on highly effective social engineering. Attackers craft seemingly legitimate job postings or recruitment communications, often tailored to specific industries or roles. Once a victim engages, they are guided through a series of steps that culminate in them being convinced to manually input and execute malicious commands in their macOS Terminal. This bypasses many traditional security layers, as the user themselves is initiating the harmful action.
How FlexibleFerret Compromises Systems
The command executed by the victim typically involves fetching and running a script from a remote server. This script then downloads and installs FlexibleFerret. Once established, FlexibleFerret offers attackers a flexible and potent toolkit for espionage and data exfiltration. While specific technical details of its capabilities are still emerging, its attribution to North Korean state-sponsored groups suggests a focus on intelligence gathering and disruption.
The Persistent Threat of State-Sponsored Actors
The involvement of North Korean operators in the FlexibleFerret campaign underscores the persistent and sophisticated threat posed by state-sponsored cyber adversaries. These groups often possess significant resources, advanced techniques, and a long-term strategic agenda, making their campaigns particularly challenging to detect and mitigate. Their adaptation to macOS and their reliance on social engineering signify a dynamic threat landscape.
Remediation Actions
- User Education: Implement rigorous security awareness training for all employees, emphasizing the dangers of unsolicited job offers and the risks associated with executing unfamiliar commands in the Terminal.
- Principle of Least Privilege: Ensure users operate with the minimum necessary privileges, restricting their ability to install unauthorized software or execute administrative commands.
- Endpoint Detection and Response (EDR): Deploy and configure EDR solutions capable of monitoring unusual process execution, network connections, and file modifications on macOS endpoints.
- Network Traffic Monitoring: Implement egress filtering and monitor network traffic for suspicious connections to known command and control (C2) infrastructure or unusual data exfiltration attempts.
- Application Whitelisting: Consider implementing application whitelisting policies to prevent the execution of untrusted applications and scripts.
- Regular Backups: Maintain regular, secure backups of critical data to facilitate recovery in the event of a successful compromise.
Tools for Detection and Mitigation
| Tool Name | Purpose | Link |
|---|---|---|
| Osquery | Endpoint visibility and threat detection on macOS | https://osquery.io/ |
| Splunk Enterprise Security | SIEM for threat detection and incident response | https://www.splunk.com/en_us/software/splunk-enterprise-security.html |
| Jamf Protect | Endpoint security and threat prevention for macOS | https://www.jamf.com/products/jamf-protect/ |
Conclusion
The FlexibleFerret malware campaign targeting macOS users, driven by North Korean operators and an evolution of the Contagious Interview campaign, underscores the critical need for vigilance. The effectiveness of this attack rests on human error induced by clever social engineering. Preventing such intrusions requires a multi-layered defense strategy, combining robust security education, stringent technical controls, and continuous monitoring to safeguard against sophisticated and adaptive threats.





