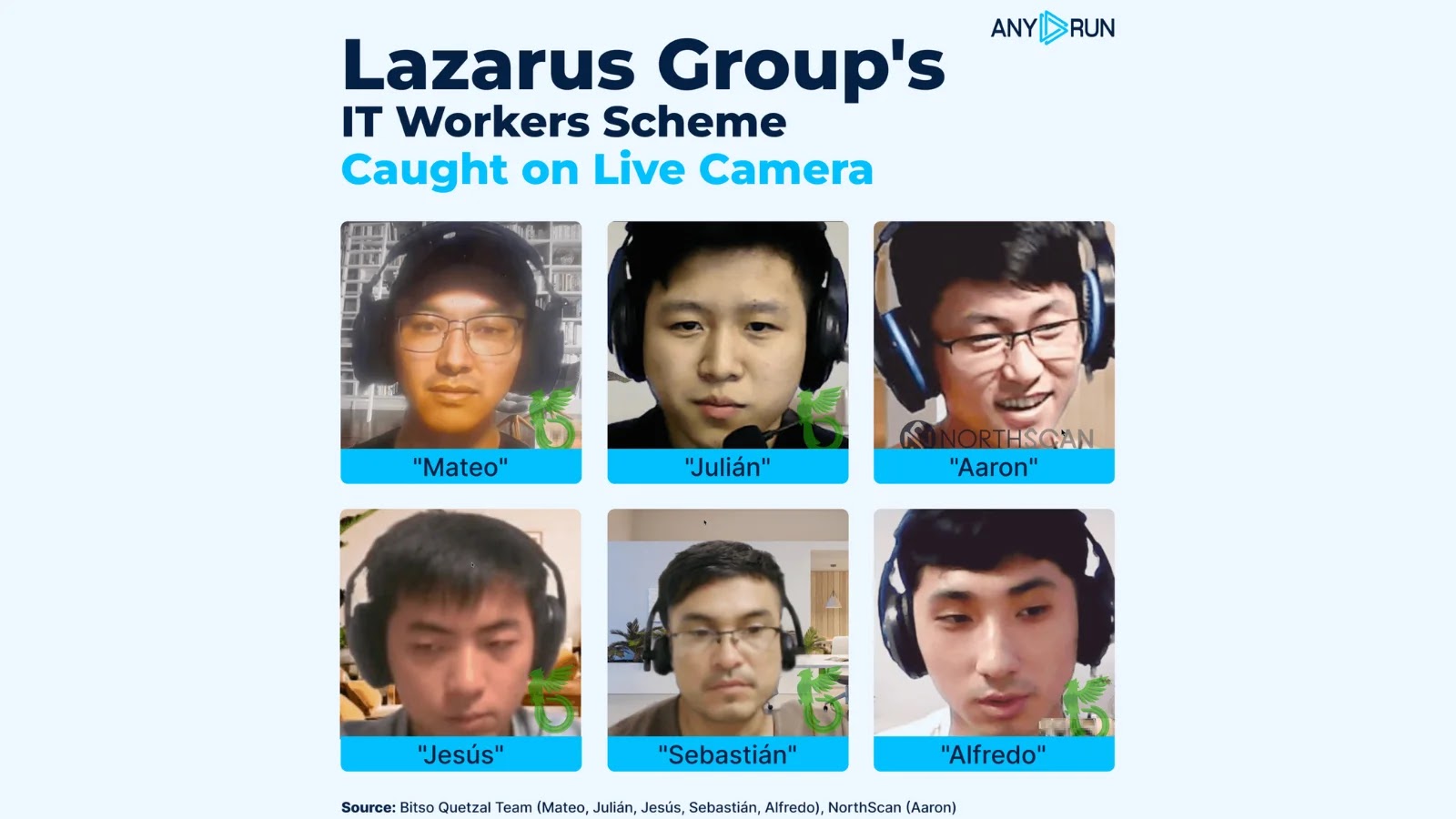
Lazarus Group’s IT Workers Scheme Hacker Group Caught Live On Camera
The digital battlefield continues to evolve, and with it, the sophistication of state-sponsored threat actors. One name consistently at the forefront of these discussions is the Lazarus Group, a notorious North Korean advanced persistent threat (APT) actor. Recently, a groundbreaking investigation pulled back the curtain, catching a unit of the Lazarus Group – specifically the infamous Chollima unit – in the act of executing its elaborate remote IT worker scheme. This unprecedented “live on camera” exposure offers invaluable insights into their methods, demonstrating how meticulously they leverage identity theft and off-the-shelf tools to infiltrate organizations.
The Sting Operation: Exposing Lazarus Group’s Modus Operandi
Researchers orchestrated a sophisticated sting operation that effectively funneled Lazarus operatives into controlled, long-running sandbox environments resembling legitimate laptop setups. This allowed for full surveillance, providing a real-time, unvarnished look at their operational tactics. The primary objective of this scheme is not always direct cyber espionage, but often financial gain through the placement of North Korean IT professionals within global companies, granting them access to internal systems and financial resources.
This exposure revealed several critical elements of their strategy:
- Identity Theft and Rental: The operatives relied heavily on stolen or rented identities to bypass initial hiring scrutiny. This highlights the critical need for robust identity verification processes during recruitment.
- Off-the-Shelf Tools: Rather than developing custom, complex malware for every step, Lazarus Group often utilizes readily available and legitimate software. This blend of legitimate tools with malicious intent makes detection challenging.
- Embedding Strategies: Their goal is to embed these disguised IT workers within target organizations, gaining a long-term foothold that can be exploited for various nefarious purposes, from data exfiltration to financial fraud.
Understanding Chollima: A Unit of the Lazarus Group
Chollima is a specific unit within the broader Lazarus Group, often associated with campaigns focused on financial institutions and cryptocurrency exchanges. Their operational methods are characterized by persistence, deception, and a clear strategic objective tied to supporting North Korea’s economic interests. The “live on camera” exposure of their IT worker scheme underscores a shift in their tactics, moving beyond purely technical breaches to more human-centric deception methods. While the specific CVEs exploited by these remote workers might vary depending on their access and targets, the underlying threat lies in the establishment of a trusted insider position.
Remediation Actions: Fortifying Defenses Against Insider Threats
The Lazarus Group’s IT worker scheme serves as a stark reminder that cybersecurity extends beyond technical vulnerabilities; it encompasses rigorous human resource practices and continuous monitoring. Organizations must implement a multi-layered defense strategy to mitigate similar threats.
- Enhanced Background Checks and Identity Verification: Go beyond standard checks. Utilize advanced identity verification services and conduct thorough due diligence on all remote IT contractors and employees, especially those with privileged access.
- Robust Access Controls and Least Privilege Principle: Implement strict Role-Based Access Control (RBAC) and adhere to the principle of least privilege. Grant users only the minimum access necessary for their job functions. Regularly review and revoke unnecessary privileges.
- Network Segmentation and Zero Trust Architecture: Segment corporate networks to limit lateral movement. Adopt a Zero Trust security model, where every access request, regardless of origin, is verified.
- Endpoint Detection and Response (EDR) & Extended Detection and Response (XDR): Deploy advanced EDR and XDR solutions to monitor endpoint activity, detect anomalous behavior, and respond to threats in real-time.
- Security Awareness Training: Educate employees about social engineering tactics, phishing attempts, and the dangers of interacting with suspicious personnel, even those seemingly within the organization.
- Regular Security Audits and Penetration Testing: Conduct frequent security audits and penetration tests to identify potential vulnerabilities in both technical infrastructure and human processes.
- Continuous Monitoring and Behavioral Analysis: Implement User and Entity Behavior Analytics (UEBA) to identify unusual activity patterns that could indicate insider threats, such as unexpected access times, data transfers, or software installations.
- Supply Chain Security: Scrutinize the security practices of third-party vendors and contractors, especially those who might have access to your internal systems.
Tools for Detection and Mitigation
Leveraging the right tools is crucial in bolstering defenses against sophisticated threat groups like Lazarus. The following table outlines categories of tools that can assist in identifying and mitigating risks associated with insider threats and sophisticated APT attacks:
| Tool Category | Purpose | Examples (Vendor Agnostic) |
|---|---|---|
| Identity Verification & Background Check Services | Thoroughly vet potential employees and contractors to confirm identity and past employment records. | Trusted identity verification platforms, specialized background check agencies. |
| Endpoint Detection and Response (EDR) | Monitor endpoint activities, detect malicious behavior, and respond to threats at the device level. | SentinelOne, CrowdStrike Falcon, Microsoft Defender ATP |
| Security Information and Event Management (SIEM) | Centralize and analyze security alerts, logs, and events across the entire infrastructure for threat detection. | Splunk, IBM QRadar, Elastic SIEM |
| User and Entity Behavior Analytics (UEBA) | Identify anomalous user and entity behavior that may indicate insider threats or compromised accounts. | Exabeam, Securonix, Splunk UBA |
| Network Detection and Response (NDR) | Monitor network traffic for suspicious activities, intrusions, and data exfiltration attempts. | Darktrace, Vectra AI, ExtraHop Reveal(x) |
| Privileged Access Management (PAM) | Secure, manage, and monitor privileged accounts and access to critical systems. | CyberArk, BeyondTrust, Thycotic |
| Data Loss Prevention (DLP) | Prevent sensitive data from leaving the organization’s control, whether accidentally or maliciously. | Symantec DLP, Forcepoint DLP, Microsoft Purview DLP |
Key Takeaways from the Lazarus Group Exposure
The “live on camera” revelation of the Lazarus Group’s IT worker scheme underscores several critical points for organizations worldwide. First, sophisticated threat actors are increasingly blending technical attacks with social engineering and identity manipulation. Second, the threat landscape demands a holistic security approach that addresses not just technological vulnerabilities but also human factors and verification processes. Finally, continuous vigilance, robust security controls, and a proactive stance against evolving adversary tactics are paramount in defending against state-sponsored threats like the Lazarus Group.





